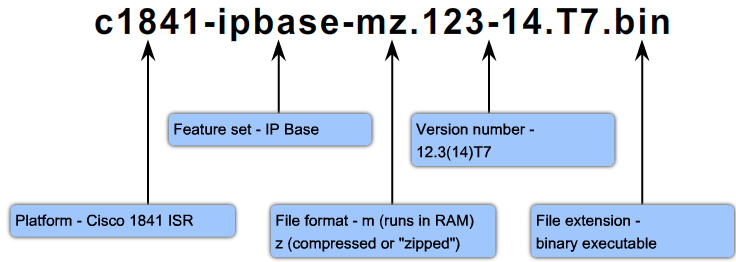
CCNA Explorer 4 Network Security
From Teknologisk videncenter
Sikkerhed
Security Terms
- White hat
- An individual who looks for vulnerabilities in systems or networks and then reports these vulnerabilities to the owners of the system so that they can be fixed.
- Black hat
- Another term for individuals who use their knowledge of computer systems to break into systems or networks that they are not authorized to use.
- Hacker
- A general term that has historically been used to describe a computer programming expert. More recently, this term is often used in a negative way to describe an individual that attempts to gain unauthorized access to network resources with malicious intent.
- Cracker
- A more accurate term to describe someone who tries to gain unauthorized access to network resources.
- Phreaker
- An individual who manipulates the phone network to cause it to perform a function that is not allowed.
- Spammer
- An individual who sends large quantities of unsolicited e-mail messages.
- Phisher
- Uses e-mail or other means to trick others into providing sensitive information.
Hacker Checklist
- Performe footprint analysis also called reconnaissance
- Find responsive IP addresses
- Enumerate information
- Collect more information about servers/network and version numbers
- Manipulate users to gain access
- Test common known usernames and passwords
- Find out how the company chooses usernames and default passwords
- Escalete privileges
- Gather additional usernames, password and secrets
- Install backdoors
- Levage the compomised system
- Attack other systems
Network Security Policies
ISO 27002 define some guidelines for developing organizational security standards through the following 12 sections:
- Risk assessment
- Security policy
- Organization of information security
- Asset management
- Human resources security
- Physical and environmental security
- Communications and operations management
- Access control
- Information systems acquisition, development, and maintenance
- Information security incident management
- Business continuity management
- Compliance
See RFC 2196, Site Security Handbook
Security Weaknesses
There are three primary vulnerabilities or weaknesses:
- Technological weaknesses
- TCP/IP protocol weakness
- Syn flood
- Unsecure protocols
- OS Weakness
- All operating systems have weaknesses
- Is documented in CERT archives at www.cert.org
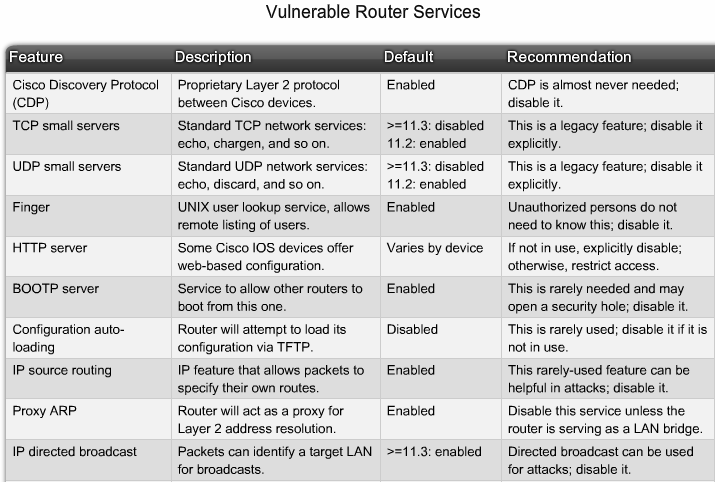
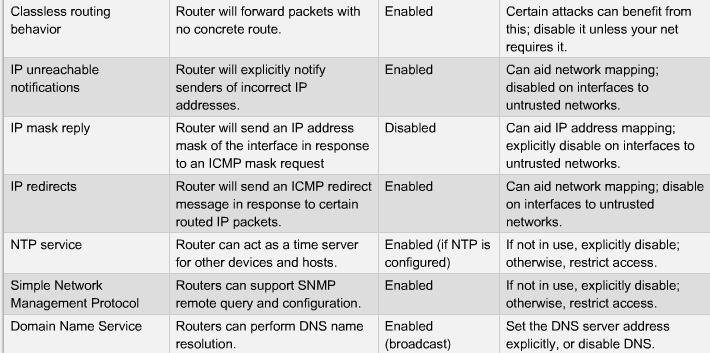
- Network Equipment weakness
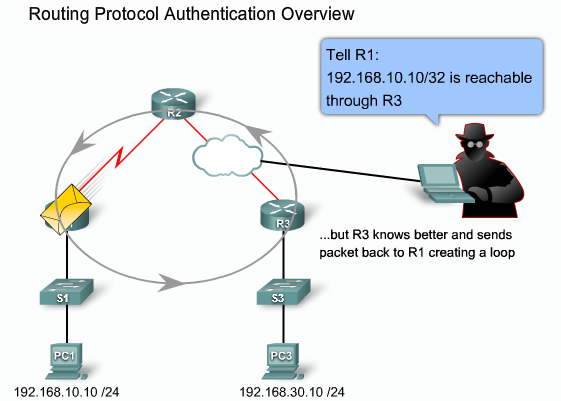
- Routing protocols
- Firewall holes
- Lack of authentication
- TCP/IP protocol weakness
- Configuration weaknesses
- Unsecure user accounts
- Weak password
- Misconfigures internet services
- Default configuration
- Security policy weaknesses
- Lack of written security policy
- Lack of authentication continuity
- Missing change management
- Missing disaster recovery plan
- Physical security
- Access Threats
- Unlocked doors to equipment
- Temperature Control
- Electrical
- No surge protection
- Missing UPS
- Maintenance threats
- Poor maintenance of critical components
- Lack of spare parts
- Poor cabling
- Poor labeling
- Access Threats
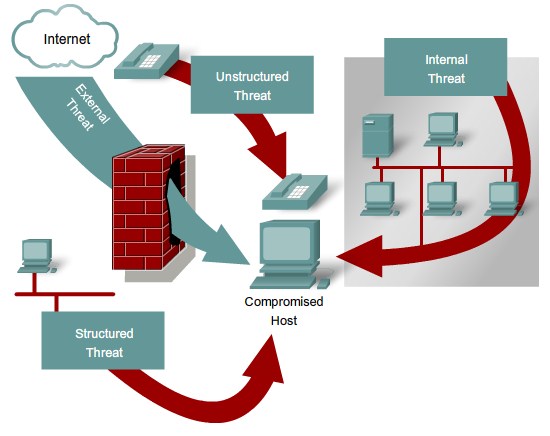
Security Threats
- Social engineering
- Phishing
- Niagara letters
- Fake Helpdesk calls to users
- Reconnaissance
- Internet Queries
- Ping sweeps
- PortScans
- Packet sniffers
- Access
- Password Attacks
- Easy passwords
- Dictionary
- Brute-force
- Trust Exploitation
- JumpHosts
- Port redirection
- MITM
- Password Attacks
- Denial of Service
- DoS
- Ping of Death
- SYN Flood
- DDoS
- Smurf Attack
- Tribe flood network(TFN)
- Stacheldraht
- MyDoom
- Worms, Viruses, and Trojan Horses
- Worms
- The enabling vulnerability
- Propagation mechanism
- Payload
- Virus
- Trojan Horses
- Worms
Mittegation Techniques
- Host mittegation
- Update OS
- Install firewall
- Install antivirus
- Shutdown unnecessary services
- Network Mittegation
- IPS
- IDS
- NAC
- ASA Firewalls
- IOS Firewalls