CCNP TSHOOT Learning Guide/Chapter 1
Planning Maintenance for Complex Networks
Introduction to Network Maintenance
understanding Maintenance Mode
Introducing network maintenance
- Hardware and software installation and configuration.
- Troubleshooting problem reports.
- Monitoring and tuning network performance.
- Planning for network expansion.
- Documenting the network and any changes made to the network.
- Ensuring compliance with legal regulations and corporate policies.
- Securing the network against internal and external threats.
Proactive Versus Reactive Network Maintenance
- Structured tasks: Performed as a predefined plan.
- Interrupt driven tasks: Involve resolving issues as they are reported.
Well Known Network Maintenance Models
| Model | Explanation |
|---|---|
| FCAPS | Fault-, Configuration-, Accounting-, Performance- and Security management |
| defined by ISO | |
| ITIL | IT Infrastructure Library |
| Defines a collection of best-practice recommendations that work together to meet business goals. | |
| TMN | Telecommunications Management Network |
| ITU-T variation of FCAPS - See above - specially targeted towards Tele Communication Networks | |
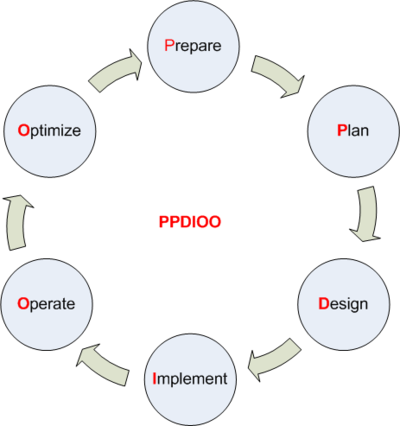
| PPDIOO | Also called Cisco Lifecycle Services (See drawing below) |
FCAPS
| Type of Management | Examples of tasks |
|---|---|
| Fault Management | Use network management software to collect information from routers and switches. |
| Send an E-mail alert when CPU utilization exceeds 80 percent. | |
| respond to incoming trouble tickets from the help desk. | |
| Configuration management | Require logging of any changes to hardware or software configurations. |
| Implement a change management system to alert relevant personal. | |
| Accounting management | Invoice IP telephony users for their long distance and international calls |
| Performance management | Monitor network performance for both LAN and WAN links |
| Deploy QoS to utilize limited WAN bandwidth. | |
| Security management | Deploy firewall, VPN and IPS technologies |
| Create a security policy dictating acceptable network use | |
| Use AAA server to validate user credentials | |
| Assign appropriate user privileges | |
| Log user activity |
Identifying Common Maintenance Procedures
Routine maintenance tasks
- Configuration Changes
- Replacement of older or failed hardware
- Scheduled backups
- Updating Software
- Monitoring network performance
Managing Network changes
- Who is responsible for authorizing network changes
- Which tasks should only be performed during scheduled maintenance windows
- What procedures should be followed prior making a change (Backup etc.)
- What measurable criteria determine the success or failure of a network change
- How will a network change be documented, and who is responsible for the documentation
- How will a roll-back plan be created prior to the change.
- Under what circumstances can formalized change management policies be overridden, and what authorization is required.
Maintaining Network Documentation
Logical Topology Diagram
Shows the interconnection between network segments. The protocols used and how end users interface with the network. (No physical locations)
Physical Topology Diagram
Show how geographical areas - floors in a building - interconnect. The diagram reflects where various network components are physically located.
Listning of Interconnections
A listing of interconnections. Ports on which devices to where. Fx. in a spreadsheet. Circuit ID's for ISP connections might be included.
Inventory of Network Equipment
Manufacturer, model, version of OS, licensing organizational tag etc.
IP Address assignments
Document IP plan.
Configuration Information
When a configuration change is made the current configuration should be backup up. Have generations of backed up configurations. could be useful. Use a logical name system to the backups. (Date etc.) Also remember to backup software. (Versions etc.)
Original design Documents
Documents created during the initial design might provide insight in the decisions the designers made. Plans for future expansions etc.
Restoring after failure
- Duplicate hardware
- OS and application software for the device. (Check licensing)
- Restore backup from failed device.
The Network Maintenance Toolkit
Basic Network Maintenance Tools
From very expensive to free tools. Vary in complexity.
CLI Tools
Cisco IOS CLI
GUI Tools
- CCP: Cisco Configuration Professional
- CCA: Cisco Configuration Assistant
- CNA: Cisco Network Assistant
- SDM: Cisco Security Device Manager
Backup Tools
Cisco IOS Backup
Example 1: Backing up manually
R1# <input>copy startup-config ftp://kevin:dj7jS@192.168.22.33</input>
Address or name of remote host [ 192.168.22.33]?
Destination file name [r1-confg]?
Writing R1-confg !!!
3458 bytes copied in 3.443 secs (1243 bytes/sec)Example 2: Predefined ftp username/password
Define password
R1# <input>configure terminal</input>
R1(config)#<input>ip ftp username kevin</input>
R1(config)#<input>ip ftp password dj7jS</input>Backing up without specifying login credentials
R1# <input>copy startup-config ftp://192.168.22.33</input>
Address or name of remote host [ 192.168.22.33]?
Destination file name [r1-confg]?
Writing R1-confg !!!
3458 bytes copied in 3.443 secs (1243 bytes/sec)Example 3: Backing up automatically
The configuration below will make a backup:
- write-memory Trigger backup when running-config is copied to nvram
- time-period 1440 Trigger backup every 1440 minuttes. 60*24=1440
!
ip ftp username kevin
ip ftp password dj7jS
!
archive
path ftp://192.168.2.33/R1-config
write-memory
time-period 1440$h = Hostname
$t = Timestamp
ftp://192.168.2.33/$h-config-$t
Viewing
R1#<input>show archive</input>
The next archive file will be named ftp://192.168.2.33/R1-confg-4
Archive # Name
0
1 ftp://192.168.2.33/R1-confg-1
2 ftp://192.168.2.33/R1-confg-2
3 ftp://192.168.2.33/R1-confg-3 <- Most Recent
4
5
6
7
8
9
10
11
12
13
14Restoring an Archived Configuration
R1# <input> configure replace ftp://192.168.22.33/R1-confg-2</input>
This will apply all necessary additions and deletions
to replace the current running configuration with the
contents of the specified configuration file, which is
assumed to be a complete configuration, not a partial
configuration. Enter Y if you are sure you want to proceed. ? [no] <input>Y</input>
Loading R1-confg-2
[OK - 3113/4096 bytes]Logging tools
See Syslog
| Priority | Name |
|---|---|
| Severity level | Name |
| 0 | Emergencies |
| 1 | Alerts |
| 2 | Critical |
| 3 | Errors |
| 4 | Warnings |
| 5 | Notifications |
| 6 | Informational |
| 7 | Debugging |
Logging setup
R1#<input>show logging history</input>
Syslog History Table:1 maximum table entries,
saving level warnings or higher
9236 messages ignored, 0 dropped, 0 recursion drops
9764 table entries flushed
SNMP notifications not enabled
entry number 9765 : LINK-3-UPDOWN
Interface GigabitEthernet0/7, changed state to up
timestamp: 169726960Configure logging
In the example below all log messages from log level 4 (warnings) or less is buffered in max. 4096 bytes Ram and sent to log server 172.16.4.16 and same log levels to console. Set use of Router Ram to max. 4096 warnings newest
!
logging buffered 4096 warnings
logging console warnings
!
logging 172.16.4.16
logging trap 4Kiwi log server software for windows: http://kiwisyslog.com
Network Time Protocol
NTP setup
!
clock timezone EST - 5
clock summer-time EDT recurring 2 Sun Mar 2:00 1 Sun Nov 2:00
ntp server 172.16.4.16- clock summer-time TIMEZONE recurring WEEK 1-4 WEEKDAY MONTH TIME ...
Network Documentation tools
- Trouble Ticket Reporting System
- Wiki
Incident recovery tools
- Cisco Works RME (Resource Manager Essentials)
- Cisco Works LMS (Lan Manager Solutions)
Monitoring and Measuring Tools
- Cisco IOS NetFlow
- SNMP
- Assuring compliance with a SLA (Service Level Agreement)
- Trend monitoring (Bandwidth, CPU utilization)
- Troubleshooting performance issues - Compare to "normal/baseline" utilization.