IEEE 802.1Q
The IEEE 802.1Q trunk protocol connects two or more Ethernet or Token Ring switches, and allows transmission of packets between Switches sharing the same VLAN(s).
Contents
Principle
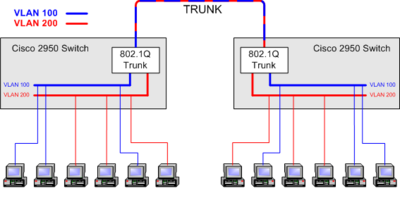
In figure 1 all PC's connected to ports which are in VLAN 100 - Blue - can communicate together, and all PC's connected to ports in VLAN 200 - Red - can communicate together. In figure 1 there can be no exchange of frames between VLAN 100 and VLAN 200.
Why is a trunk protocol needed
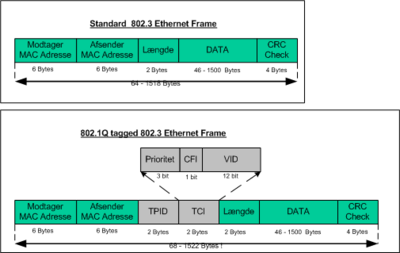
A trunk protocol is needed when using a OSI layer 2 technology as Ethernet or Token Ring because the Layer 2 header has no field describing the origin of the frames. Se figure two upper half Standard 802.3 Ethernet Frame. There is no field where the transmitting Switch can tell the receiving Switch which VLAN a receiving frame belongs.
Tagging a Frame
If both switches uses the IEEE 802.1Q tagging trunk protocol, the transmitting Switch tags the frame when sending it. Se figure 2 bottom half 802.1Q tagged 802.3 Ethernet Frame
| Field | Description |
|---|---|
| Priority | Also called CoS field or Class of Service. A priority between 0 and 7 |
| CFI | Canonical Field Indicator CFI=0 (Ethernet) CFI=1 (Token Ring) |
| VID | Vlan ID, to which VLAN number the Frame belongs (0 - 4095) |
Native VLAN
Defined in the 802.1Q specification there is one untagged VLAN. The standard untagged VLAN for ethernet is VLAN 1 which is the standard administrative VLAN. All ethernet ports belong to VLAN 1 on a unconfigured switch.
VLAN Hopping
VLAN hopping (virtual local area network hopping) is a computer security exploit, a method of attacking networked resources on a VLAN. The basic concept behind all VLAN hopping attacks is for an attacking host on a VLAN to gain access to traffic on other VLANs that would normally not be accessible. There are two primary methods of VLAN hopping: switch spoofing and double tagging.
In a switch spoofing attack, an attacking host that is capable of speaking the tagging and trunking protocols used in maintaining a VLAN imitates a trunking switch. Traffic for multiple VLANs is then accessible to the attacking host.
In a double tagging attack, an attacking host prepends two VLAN tags to packets that it transmits. The first header (which corresponds to the VLAN that the attacker is really a member of) is stripped off by a first switch the packet encounters, and the packet is then forwarded. The second, false, header is then visible to the second switch that the packet encounters. This false VLAN header indicates that the packet is destined for a host on a second, target VLAN. The packet is then sent to the target host as though it were layer 2 traffic. By this method, the attacking host can bypass layer 3 security measures that are used to logically isolate hosts from one another.
As an example of a double tagging attack, consider a secure web server on a VLAN called VLAN1. Hosts on VLAN1 are allowed access to the web server; hosts from outside the VLAN are blocked by layer 3 filters. An attacking host on a separate VLAN, called VLAN2, creates a specially formed packet to attack the web server. It places a header tagging the packet as belonging to VLAN2 on top of another header tagging the packet as belonging to VLAN1. When the packet is sent, the switch on VLAN2 sees the VLAN2 header and removes it, and forwards the packet. The VLAN2 switch expects that the packet will be treated as a standard TCP packet by the switch on VLAN1. However, when the packet reaches VLAN1, the switch sees a tag indicating that the packet is part of VLAN1, and so bypasses the layer 3 handling, treating it as a layer 2 packet on the same logical VLAN. The packet thus arrives at the target server as though it was sent from another host on VLAN1, ignoring any layer 3 filtering that might be in place.
Links
- VLAN Hopping as explained in a Cisco document ...
- Mausezahn as VLAN hopping tool. See also Mausezahn (local).
- VLAN hopping questions