Difference between revisions of "IPSec VTI Cisco IOS"
From Teknologisk videncenter
m (Created page with "Virtual Tunnel Interface(VTI) IPSec er en måde hvorpå man kan lave IPSec forbindelser der understøtter Broadcast & Multicast uden brug af GRE protokollen. ...") |
m (→R1) |
||
| Line 16: | Line 16: | ||
Der er konfigureret IPSec VTI imellem R2-R3, R2-R4 og alm. IPSec imellem R2-R5. | Der er konfigureret IPSec VTI imellem R2-R3, R2-R4 og alm. IPSec imellem R2-R5. | ||
==R1== | ==R1== | ||
| + | Der genbrugs noget af konfigurationen imellem alm. IPSec og VTI | ||
| + | ===VTI=== | ||
| + | VTI Konfiguration til R3 og R4 | ||
| + | <source lang=cli> | ||
| + | crypto isakmp policy 10 | ||
| + | encr aes 256 | ||
| + | authentication pre-share | ||
| + | group 16 | ||
| + | <notice>crypto isakmp key cisco address 0.0.0.0 0.0.0.0</notice> | ||
| + | ! | ||
| + | crypto ipsec transform-set TSET ah-sha-hmac | ||
| + | ! | ||
| + | <notice>crypto ipsec profile P1 | ||
| + | set transform-set TSET</notice> | ||
| + | ! | ||
| + | interface Tunnel23 | ||
| + | ip address 10.23.0.2 255.255.0.0 | ||
| + | tunnel source 192.168.1.2 | ||
| + | tunnel destination 192.168.2.2 | ||
| + | <notice>tunnel mode ipsec ipv4 | ||
| + | tunnel protection ipsec profile P1</notice> | ||
| + | ! | ||
| + | interface Tunnel24 | ||
| + | ip address 10.24.0.2 255.255.0.0 | ||
| + | tunnel source 192.168.1.2 | ||
| + | tunnel destination 192.168.3.2 | ||
| + | <notice>tunnel mode ipsec ipv4 | ||
| + | tunnel protection ipsec profile P1</notice> | ||
| + | ! | ||
| + | </source> | ||
| + | Konfigurationen af IPSec VTI på de andre routere er den samme | ||
| + | ===Alm. IPSec=== | ||
| + | <source lang=cli> | ||
| + | <notice>crypto map CMAP 10 ipsec-isakmp | ||
| + | set peer 192.168.4.2 | ||
| + | set transform-set TSET | ||
| + | match address 109</notice> | ||
| + | ! | ||
| + | interface Tunnel25 | ||
| + | ip address 10.25.0.2 255.255.0.0 | ||
| + | tunnel source 192.168.1.2 | ||
| + | tunnel destination 192.168.4.2 | ||
| + | ! | ||
| + | interface FastEthernet0/0 | ||
| + | ip address 192.168.1.2 255.255.255.252 | ||
| + | ip nat outside | ||
| + | ip virtual-reassembly | ||
| + | duplex auto | ||
| + | speed auto | ||
| + | <notice>crypto map CMAP</notice> | ||
| + | ! | ||
| + | <notice>access-list 109 permit gre host 192.168.1.2 host 192.168.4.2</notice> | ||
| + | </source> | ||
| + | Konfigurationen af R5 er også her bare den modsatte af ovenstående eksempel | ||
Revision as of 11:28, 13 February 2015
Virtual Tunnel Interface(VTI) IPSec er en måde hvorpå man kan lave IPSec forbindelser der understøtter Broadcast & Multicast uden brug af GRE protokollen. Der bliver stadig oprettet et tunnel interface, men det er af typen IPSec, så der kommer en ren IP pakke inden i en anden IP pakke, og altså ikke med GRE som mellem led. Fordele:
- Mindre konfiguration
- Bindes ikke til at fysisk interface
- Bruger færre resourcer
- Mindre pakker
- Generisk Crypto PSK der ikke bindes til en bestemt fjern adresse
Ulemper:
- Understøtter kun Unicast og Multicast
- Kræver VAM2+ crypto engine for at indpakke i hardware[1]
Contents
Setup
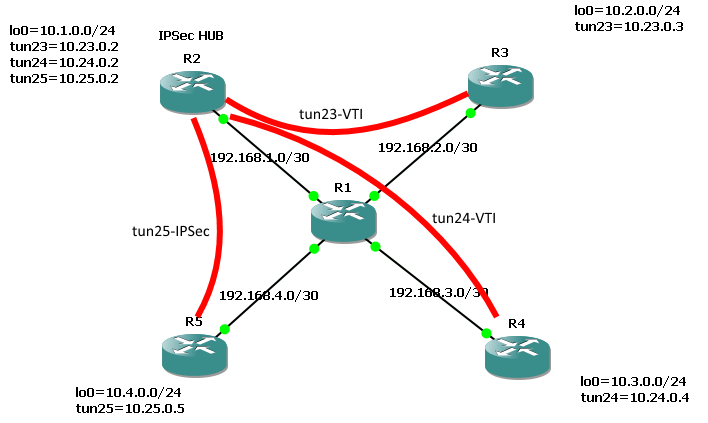
For at sammenligne bruges dette setup:
Der er konfigureret IPSec VTI imellem R2-R3, R2-R4 og alm. IPSec imellem R2-R5.
R1
Der genbrugs noget af konfigurationen imellem alm. IPSec og VTI
VTI
VTI Konfiguration til R3 og R4
crypto isakmp policy 10
encr aes 256
authentication pre-share
group 16
<notice>crypto isakmp key cisco address 0.0.0.0 0.0.0.0</notice>
!
crypto ipsec transform-set TSET ah-sha-hmac
!
<notice>crypto ipsec profile P1
set transform-set TSET</notice>
!
interface Tunnel23
ip address 10.23.0.2 255.255.0.0
tunnel source 192.168.1.2
tunnel destination 192.168.2.2
<notice>tunnel mode ipsec ipv4
tunnel protection ipsec profile P1</notice>
!
interface Tunnel24
ip address 10.24.0.2 255.255.0.0
tunnel source 192.168.1.2
tunnel destination 192.168.3.2
<notice>tunnel mode ipsec ipv4
tunnel protection ipsec profile P1</notice>
!Konfigurationen af IPSec VTI på de andre routere er den samme
Alm. IPSec
<notice>crypto map CMAP 10 ipsec-isakmp
set peer 192.168.4.2
set transform-set TSET
match address 109</notice>
!
interface Tunnel25
ip address 10.25.0.2 255.255.0.0
tunnel source 192.168.1.2
tunnel destination 192.168.4.2
!
interface FastEthernet0/0
ip address 192.168.1.2 255.255.255.252
ip nat outside
ip virtual-reassembly
duplex auto
speed auto
<notice>crypto map CMAP</notice>
!
<notice>access-list 109 permit gre host 192.168.1.2 host 192.168.4.2</notice>