Difference between revisions of "Netband Project - CoPP"
From Teknologisk videncenter
(→Configuration) |
|||
| (2 intermediate revisions by 2 users not shown) | |||
| Line 1: | Line 1: | ||
| − | + | =CoPP= | |
This page is part of the [[Netband_Project|Netband Project]] | This page is part of the [[Netband_Project|Netband Project]] | ||
==Control Plane Policing== | ==Control Plane Policing== | ||
| Line 148: | Line 148: | ||
<br> | <br> | ||
[http://www.cisco.com/web/about/security/intelligence/coppwp_gs.html CoPP best practice design guide] | [http://www.cisco.com/web/about/security/intelligence/coppwp_gs.html CoPP best practice design guide] | ||
| + | [[Category:network]][[Category:CCNP]][[category:students]] | ||
Latest revision as of 06:32, 13 May 2009
Contents
CoPP
This page is part of the Netband Project
Control Plane Policing
- The Control Plane Policing feature allows users to configure a quality of service (QoS) filter that manages the traffic flow of control plane packets to protect the control plane of Cisco IOS routers and switches against reconnaissance and denial-of-service (DoS) attacks.
- CoPP can help maintain packet forwarding and protocol states despite an attack or heavy traffic load on the router or switch.
- Uses MQC (Modular QoS CLI)
- In version 12.4(4)T additional features were introduced
- Control plane protection
- Port-filtering
- Queue-thresholding
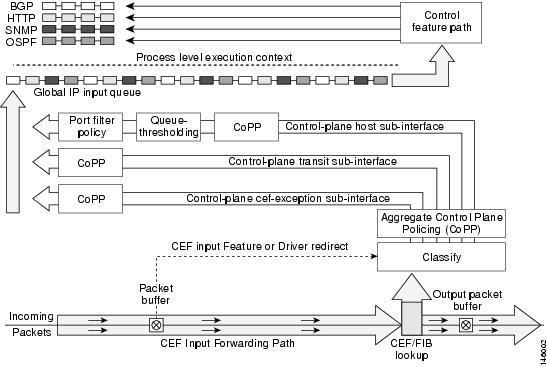
Control Plane Protection
- Introduces subinterfaces to the control plane
- Aggregrate Control Plane Policing
- Control Plane cef-exception subinterface
- receives all traffic that is either redirected as a result of a configured input feature in the CEF packet forwarding path for process switching or directly enqueued in the control plane input queue by the interface driver.
- Eg. ARP, L2 Keepalives and all non-IP host traffic.
- Control Plane host subinterface
- receives all control-plane IP traffic that is directly destined for one of the router interfaces.
- All host traffic terminates on and is processed by the router.
- Eg. SSH, SNMP, BGP, OSPF, Tunnel termination and EIGRP.
- Control Plane transit subinterface
- receives all control-plane IP traffic that is software switched by the route processor.
- Control Plane cef-exception subinterface
Port-filter policy
- Blocks traffic destined to closed or nonlistened TCP/UDP ports
- Only works with the host subinterface.
- Maintains a global database of all open TCP and UDP ports on the router, including ports created by applications.
Queue Threshold Policy
- limits the number of unprocessed packets for a given higher level protocol allowed in the control-plane IP input queue.
Configuration
Control plane Policing
Versions prior to 12.4(4)T or if you only want to configure the aggregate interface ip access-list extended coppacl-igp permit ospf any host 224.0.0.5 permit ospf any host 224.0.0.6 permit ospf any any ! ip access-list extended coppacl-management permit tcp 10.0.0.0 0.255.255.255 any eq 22 permit tcp 10.0.0.0 0.255.255.255 any eq telnet permit udp host 10.1.1.10 any eq snmp permit udp host 10.0.0.11 any eq ntp ! ip access-list extended coppacl-monitoring permit icmp any any ttl-exceeded permit icmp any any port-unreachable permit icmp any any echo-reply permit icmp any any echo ! ip access-list extended coppacl-critical-app permit udp host 0.0.0.0 host 255.255.255.255 eq bootps permit udp host 10.1.1.11 eq bootps any eq bootps ! class-map match-all coppclass-igp match access-group name coppacl-igp class-map match-all coppclass-management match access-group name coppacl-management class-map match-all coppclass-monitoring match access-group name coppacl-monitoring class-map match-all coppclass-critical-app match access-group name coppacl-critical-app class-map match-all coppclass-layer2 match protocol arp ! policy-map copp-policy class coppclass-igp class coppclass-management police rate 250 pps conform-action transmit exceed-action drop class coppclass-monitoring police rate 50 pps conform-action transmit exceed-action drop class coppclass-critical-app police rate 75 pps conform-action transmit exceed-action drop class coppclass-layer2 police rate 25 pps conform-action transmit exceed-action drop class class-default police rate 10 pps conform-action transmit exceed-action drop ! control-plane service-policy input copp-policy
Port-filter policy
class-map type port-filter match-any portfilter-cmap match closed-ports ! policy-map type port-filter portfilter-pmap class portfilter-cmap drop ! control-plane host service-policy type port-filter input portfilter-pmap !
Queue-threshold policy
class-map type queue-threshold match-all queue-cmap match host-protocols ! policy-map type queue-threshold queue-pmap class queue-cmap queue-limit 100 ! control-plane host service-policy type queue-threshold input queue-pmap
Show output
B1rt1#sh control-plane host open-ports Active internet connections (servers and established) Prot Local Address Foreign Address Service State tcp *:22 *:0 SSH-Server LISTEN tcp *:23 *:0 Telnet LISTEN tcp *:80 *:0 HTTP CORE LISTEN tcp *:22 10.1.2.50:5954 SSH-Server ESTABLIS udp *:67 *:0 DHCPD Receive LISTEN udp *:68 *:0 BootP client LISTEN udp *:123 *:0 NTP LISTEN
B1rt1#sh control-plane host counters Control plane host path counters : Feature Packets Processed/Dropped/Errors -------------------------------------------------------- TCP/UDP Portfilter 3337/2028/0 Protocol Queue Threshold 384/0/0 --------------------------------------------------------
B1rt1#sh control-plane counters Feature Path Packets processed/dropped/errors Aggregate 392996/2628/0 Host 9373/2135/0 Transit 369604/0/0 Cef-exception 11391/0/0
External Links
CoPP
CoP extended feature set
CoPP best practice design guide