Difference between revisions of "CCNA Explorer 3 Basic Wireless Concepts and Configuration"
From Teknologisk videncenter
m (New page: =Basic Wireless Concepts and Configuration= ==The Wireless LAN== ===Why Use Wireless?=== {| |800px|left|thumb|Wireless Techonologies |- |[[Image:ScreenShot219.j...) |
m |
||
| Line 52: | Line 52: | ||
|- | |- | ||
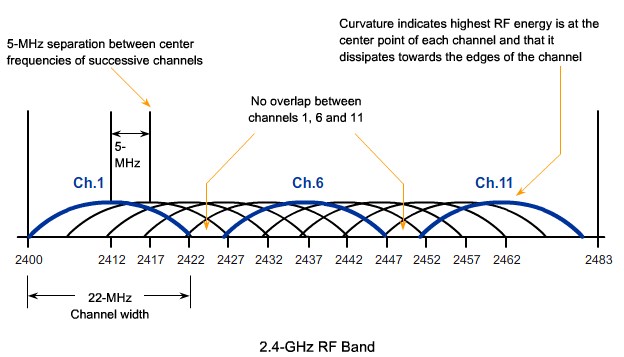
|[[Image:ScreenShot233.jpg|800px|left|thumb|Channels]] | |[[Image:ScreenShot233.jpg|800px|left|thumb|Channels]] | ||
| + | |- | ||
| + | |[[Image:ScreenShot234.jpg|800px|left|thumb|Ad Hoc Networks]] | ||
| + | |- | ||
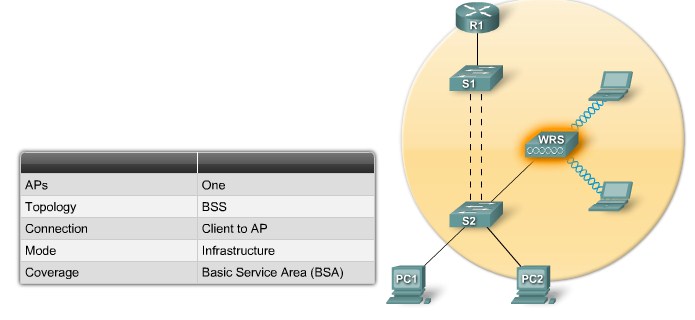
| + | |[[Image:ScreenShot235.jpg|800px|left|thumb|Basic Service Set]] | ||
| + | |- | ||
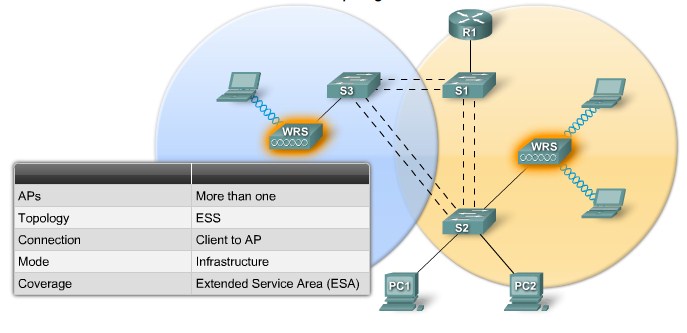
| + | |[[Image:ScreenShot236.jpg|800px|left|thumb|Extended Service Set]] | ||
| + | |- | ||
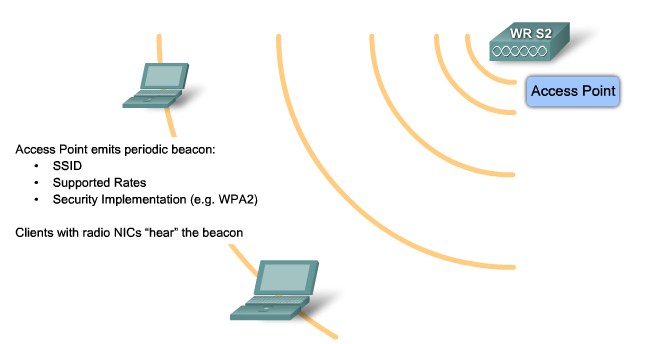
| + | |[[Image:ScreenShot237.jpg|800px|left|thumb|Wireless Beacon]] | ||
| + | |- | ||
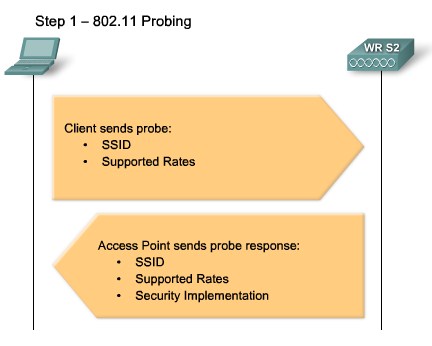
| + | |[[Image:ScreenShot238.jpg|800px|left|thumb|Wireless Probe]] | ||
| + | |- | ||
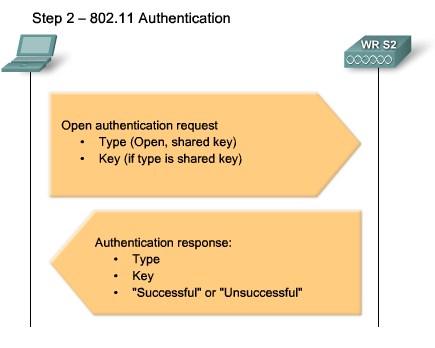
| + | |[[Image:ScreenShot239.jpg|800px|left|thumb|Wireless Authentication]] | ||
| + | |- | ||
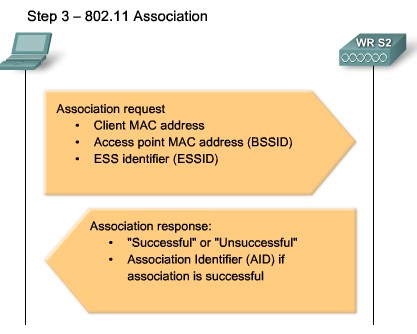
| + | |[[Image:ScreenShot240.jpg|800px|left|thumb|Wireless Association]] | ||
|- | |- | ||
| | | | ||
| + | ===Planning the Wireless LAN=== | ||
| + | {| | ||
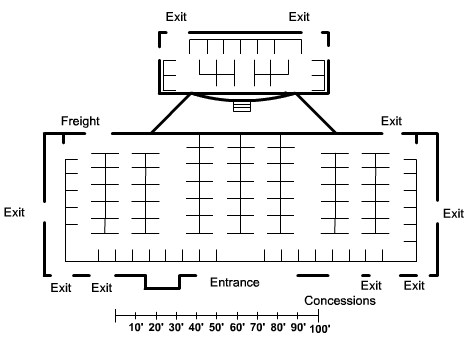
| + | |[[Image:ScreenShot241.jpg|800px|left|thumb|Map]] | ||
| + | |- | ||
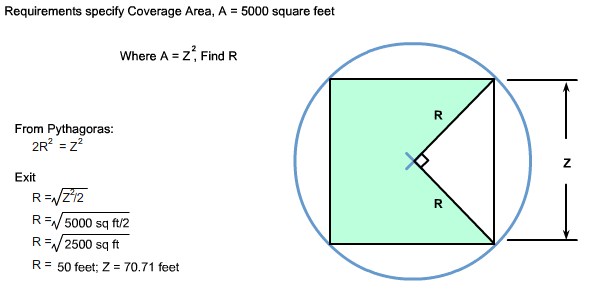
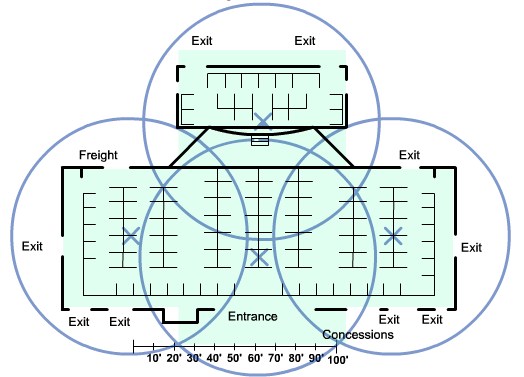
| + | |[[Image:ScreenShot242.jpg|800px|left|thumb|Coverage Area]] | ||
| + | |- | ||
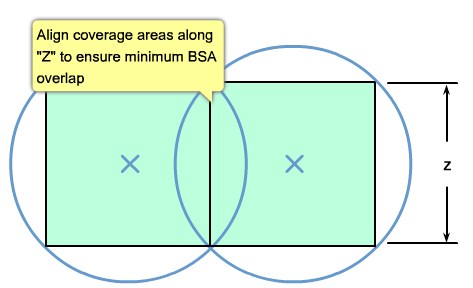
| + | |[[Image:ScreenShot243.jpg|800px|left|thumb|Align Coverage Areas]] | ||
| + | |- | ||
| + | |[[Image:ScreenShot244.jpg|800px|left|thumb|Plan]] | ||
| + | |- | ||
| + | | | ||
| + | ==WIreles LAN Security== | ||
| + | ===Threats to Wireless Security=== | ||
| + | {| | ||
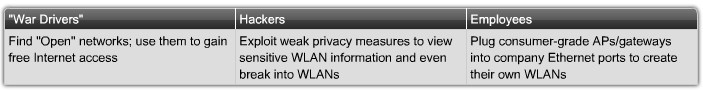
| + | |[[Image:ScreenShot245.jpg|800px|left|thumb|Unauthorized Access]] | ||
| + | |- | ||
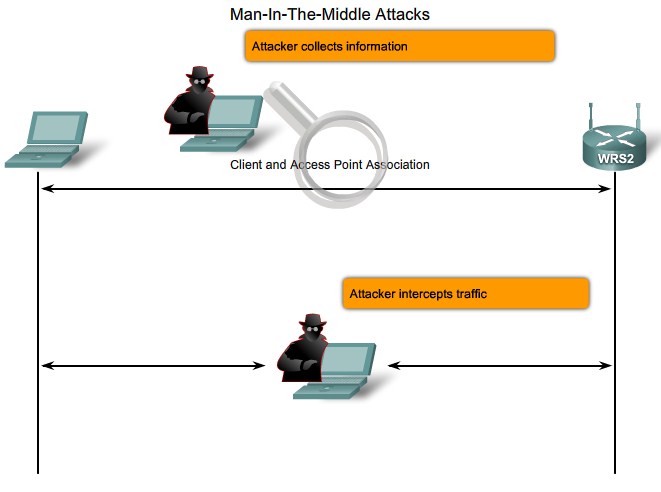
| + | |[[Image:ScreenShot246.jpg|800px|left|thumb|MITM]] | ||
| + | |- | ||
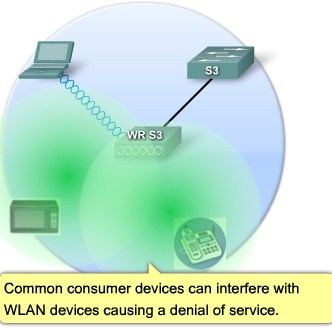
| + | |[[Image:ScreenShot247.jpg|800px|left|thumb|Denial of Service 1]] | ||
| + | |- | ||
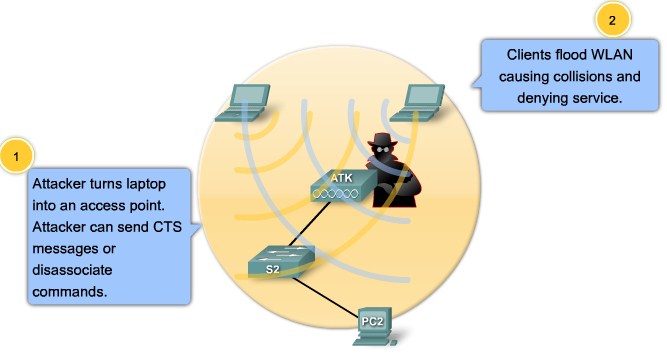
| + | |[[Image:ScreenShot248.jpg|800px|left|thumb|Denial of Service 2]] | ||
| + | |- | ||
| + | | | ||
| + | ===Wireless Security Protocols=== | ||
| + | {| | ||
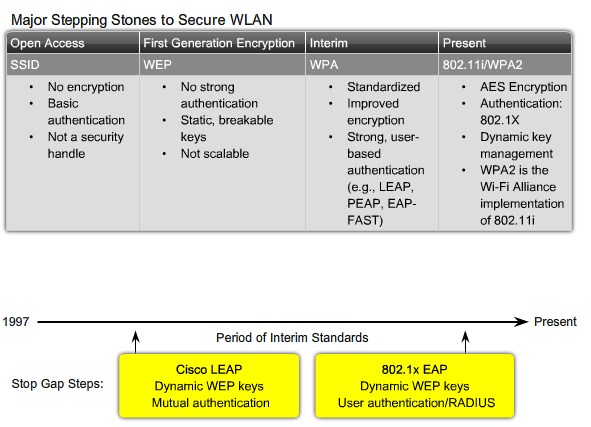
| + | |[[Image:ScreenShot249.jpg|800px|left|thumb|Wireless Security Protocols]] | ||
| + | |- | ||
| + | |7.2.2 | ||
Revision as of 16:58, 25 August 2010
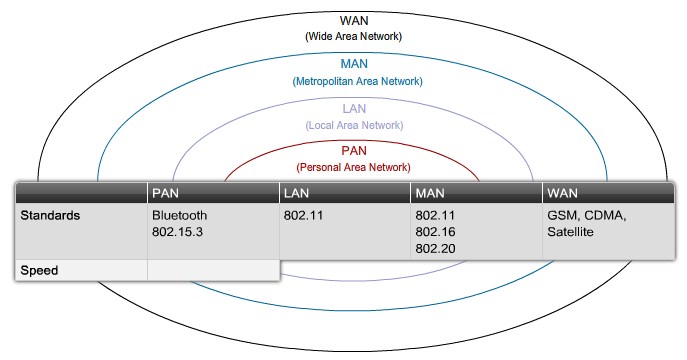
Basic Wireless Concepts and Configuration
The Wireless LAN
Why Use Wireless?
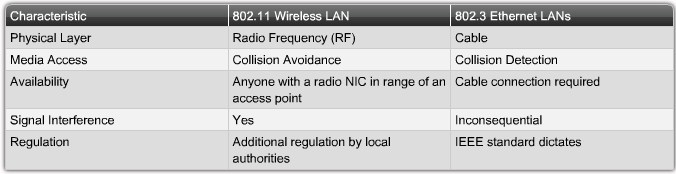
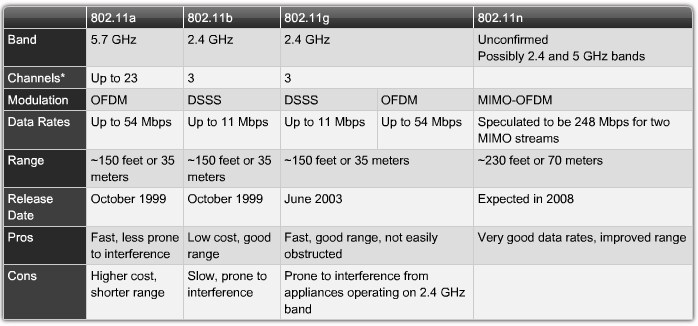
Wireless LAN Standards
|