Difference between revisions of "CCNP 3 Minimizing Service Loss and Data Theft in a Campus Network"
From Teknologisk videncenter
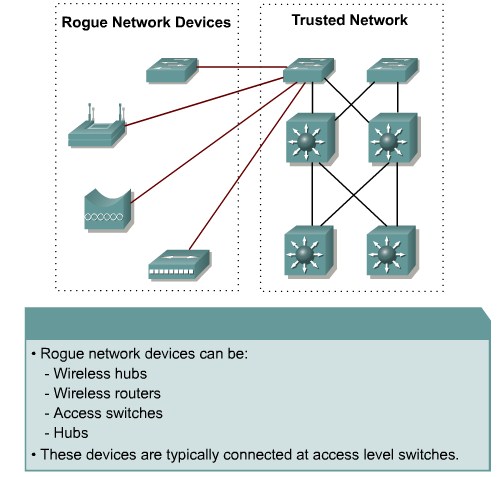
m (New page: =Understanding Switch Security Issues= ==Describing Unauthorized Access by Rogue Devices== {| |800px|left|thumb|Rouge Access Points |} {|border=1 |MAC address F...) |
m (→Describing Unauthorized Access by Rogue Devices) |
||
| Line 4: | Line 4: | ||
|[[Image:ScreenShot548.jpg|800px|left|thumb|Rouge Access Points]] | |[[Image:ScreenShot548.jpg|800px|left|thumb|Rouge Access Points]] | ||
|} | |} | ||
| + | ==Switch Attack Categories== | ||
| + | *MAC layer attacks | ||
| + | *VLAN attacks | ||
| + | *Spoof attacks | ||
| + | *Switch device attacks | ||
{|border=1 | {|border=1 | ||
|MAC address Flooding||Port Security | |MAC address Flooding||Port Security | ||
Revision as of 13:30, 15 September 2010
Understanding Switch Security Issues
Describing Unauthorized Access by Rogue Devices
Switch Attack Categories
- MAC layer attacks
- VLAN attacks
- Spoof attacks
- Switch device attacks
| MAC address Flooding | Port Security |
| VLAN Hooping | Tighten up trunk configurations and the nogotiation state |
| Attacks between devices on a common VLAN | Implement Private VLANS(PVLANs) |
| DHCP Spoofing | USe DHCP Snooping |
| Spanning tree compromises | Proactively configure the primary and backup root devices, Enable root guard |
| MAC Spoofing | Use DHCP Snooping. Port security. |
| ARP Spoofing | Use Dynamic ARP Inspection. DHCP Snooping, Port Security |
| CDP Manipulation | Diable CDP on al ports where it is not intentionally used. |
| SSH & Telnet attacks | Use SSHv2. Use Telnet with VTY ACLs |