Difference between revisions of "CCNA Explorer 3 Basic Wireless Concepts and Configuration"
From Teknologisk videncenter
m |
m (→Wireless Security Protocols) |
||
| Line 95: | Line 95: | ||
|[[Image:ScreenShot249.jpg|800px|left|thumb|Wireless Security Protocols]] | |[[Image:ScreenShot249.jpg|800px|left|thumb|Wireless Security Protocols]] | ||
|- | |- | ||
| − | | | + | |[[Image:ScreenShot250.jpg|800px|left|thumb|Wireless Association]] |
| + | |- | ||
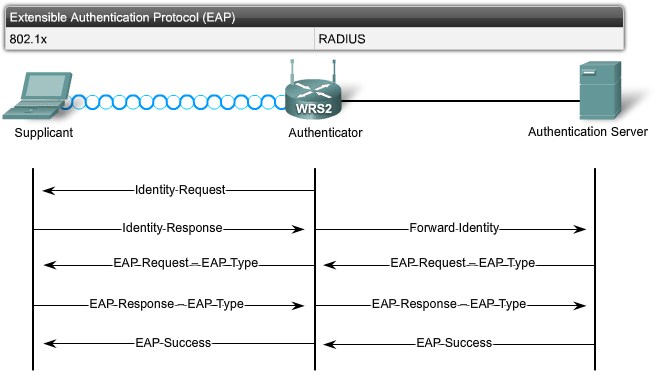
| + | |[[Image:ScreenShot251.jpg|800px|left|thumb|EAP]] | ||
| + | |- | ||
| + | |[[Image:ScreenShot252.jpg|800px|left|thumb|TKIP and AES]] | ||
| + | |- | ||
| + | |[[Image:ScreenShot252.jpg|800px|left|thumb|TKIP and AES]] | ||
| + | |- | ||
| + | | | ||
| + | ===Securing a Wireless LAN=== | ||
| + | {| | ||
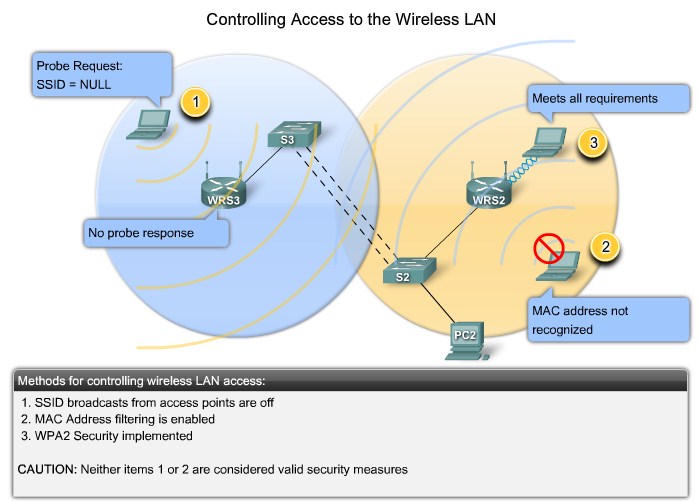
| + | |[[Image:ScreenShot253.jpg|800px|left|thumb|Controlling Access to the Wireless LAN]] | ||
| + | |- | ||
| + | | | ||
| + | ==Configuring Wireless LAN Access== | ||
| + | ===Configuring the Wireless Access Point=== | ||
| + | {| | ||
| + | |[[Image:ScreenShot254.jpg|800px|left|thumb|Configuration Steps]] | ||
| + | |- | ||
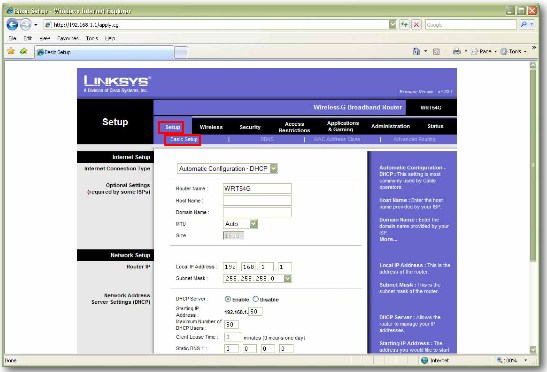
| + | |[[Image:ScreenShot255.jpg|800px|left|thumb|Setup]] | ||
| + | |- | ||
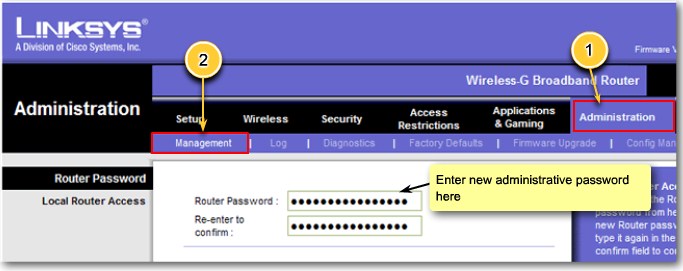
| + | |[[Image:ScreenShot256.jpg|800px|left|thumb|Management]] | ||
| + | |- | ||
| + | |[[Image:ScreenShot257.jpg|800px|left|thumb|Wireless]] | ||
| + | |- | ||
| + | |[[Image:ScreenShot258.jpg|800px|left|thumb|Configuration overview]] | ||
| + | |- | ||
| + | |[[Image:ScreenShot259.jpg|800px|left|thumb|Configure mode]] | ||
| + | |- | ||
| + | |[[Image:ScreenShot260.jpg|800px|left|thumb|Configure SSID]] | ||
| + | |- | ||
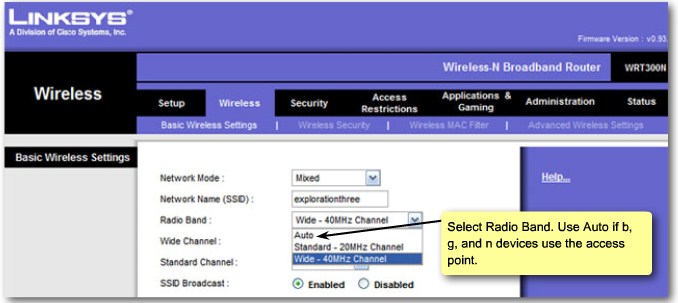
| + | |[[Image:ScreenShot261.jpg|800px|left|thumb|Confiugre Radio Band]] | ||
| + | |- | ||
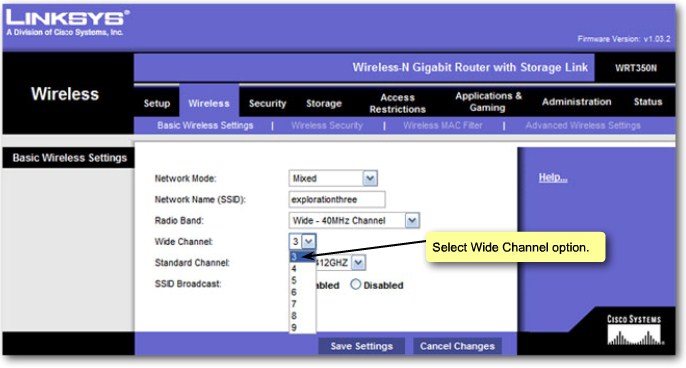
| + | |[[Image:ScreenShot262.jpg|800px|left|thumb|Configure Wide Channel]] | ||
| + | |- | ||
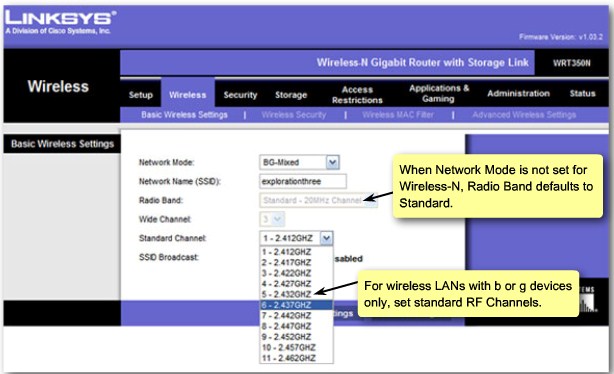
| + | |[[Image:ScreenShot263.jpg|800px|left|thumb|Configure standard channel]] | ||
| + | |- | ||
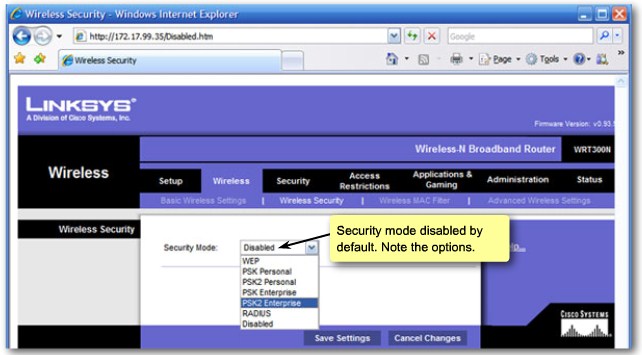
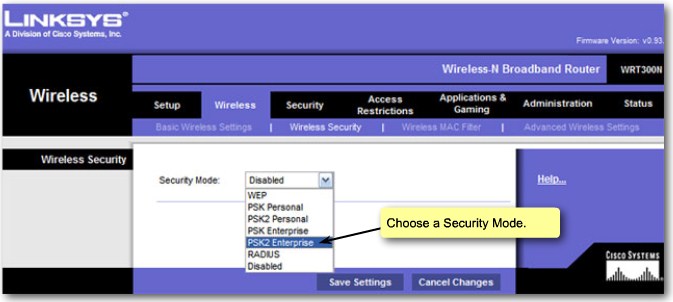
| + | |[[Image:ScreenShot264.jpg|800px|left|thumb|Wireless Security - Overview]] | ||
| + | |- | ||
| + | |[[Image:ScreenShot265.jpg|800px|left|thumb|Wireless Security - Mode]] | ||
| + | |- | ||
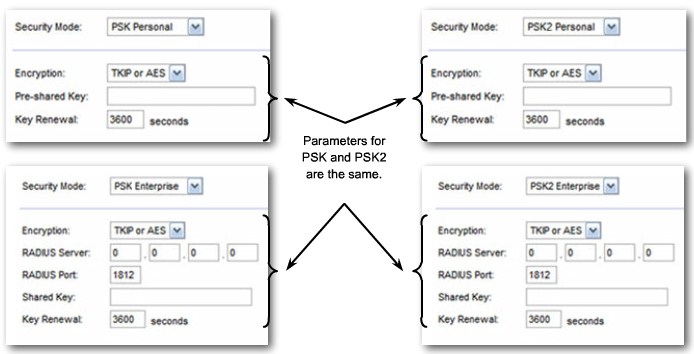
| + | |[[Image:ScreenShot266.jpg|800px|left|thumb|Wireless Security - Mode Parameters]] | ||
| + | |- | ||
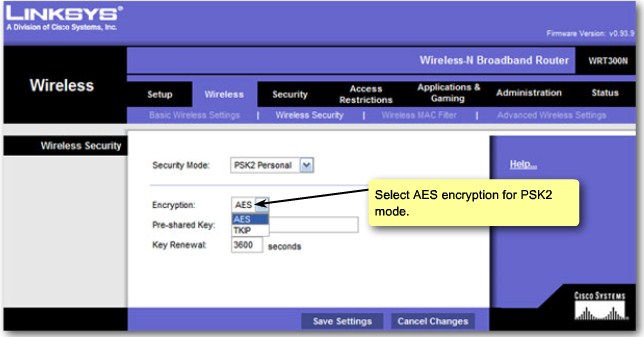
| + | |[[Image:ScreenShot267.jpg|800px|left|thumb|Wireless Security - Encryption]] | ||
| + | |- | ||
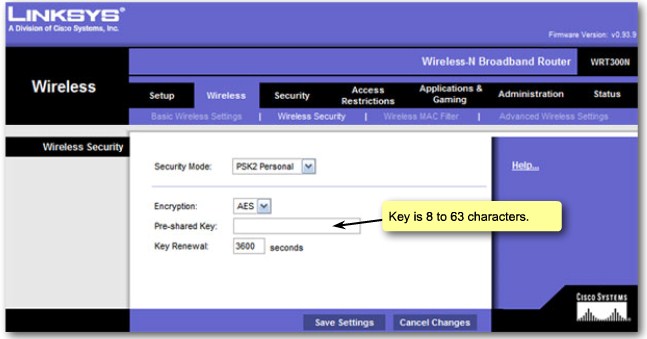
| + | |[[Image:ScreenShot268.jpg|800px|left|thumb|Wireless Security - Key]] | ||
| + | |- | ||
| + | | | ||
| + | ===Configuring Wireless NIC=== | ||
Revision as of 13:01, 26 August 2010
Contents
Basic Wireless Concepts and Configuration
The Wireless LAN
Why Use Wireless?
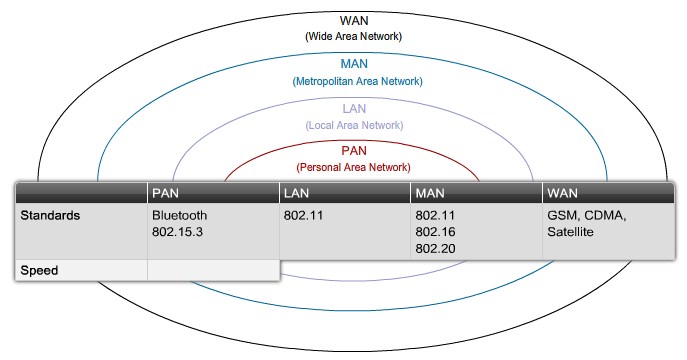
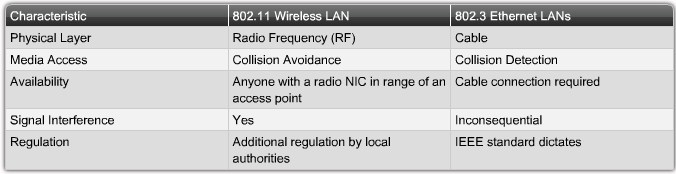
Wireless LAN Standards
|