Difference between revisions of "CCNP SWITCH/Securing the Campus Infrastructure"
m (→VLAN Attacks) |
m (→DHCP starcation and spoofing) |
||
| Line 26: | Line 26: | ||
==Spoofing Attacks== | ==Spoofing Attacks== | ||
| − | ===DHCP | + | ===DHCP starvation and spoofing=== |
| + | An attacking device can exhaust the address space available to the DHCP servers for a period of time or establish itself as a DHCP server in man-in-the-middle attacks.<br/> | ||
| + | '''Mittigation:'''<br/> | ||
| + | Use DHCP snooping | ||
| + | ===Spanning-tree compromises=== | ||
| + | Attacking device spoofs the root bridge in the STP topology. If successful, the network attacker cansee a variety of frames.<br/> | ||
| + | '''Mittigation:'''<br/> | ||
| + | Proactively configure the primary and backup root devices. Enable root guard. | ||
| + | ===MAC spoofing=== | ||
| + | Attacking device spoofs the MAC address of a valid host currently in the CAM table. The switch then forwards frames destined for the valid host to the attacking device.<br/> | ||
| + | '''Mittigation:'''<br/> | ||
| + | Use DHCP snooping, port security. | ||
| + | ===ARP spoofing=== | ||
| + | Attacking device crafts ARP replies intended for valid hosts. The attackingdevice’s MAC address thenbecomes the destination addressfound in the Layer 2 frames sent by the valid network device.<br/> | ||
| + | '''Mittigation:'''<br/> | ||
| + | Use Dynamic ARP Inspection. DHCP snooping, port security. | ||
| + | ==Switch Device Attacks== | ||
| + | ===CDP manipulation=== | ||
| + | Information sent through CDP is transmitted in clear text and unauthenticated, allowing it to be captured and divulge network topology information.<br/> | ||
| + | '''Mittigation:'''<br/> | ||
| + | Disable CDP on all ports where it is not intentionally used. | ||
| + | ===SSH and Telnet attacks=== | ||
| + | Telnet packets can be read in clear text. SSH is an option but has securityissues in version 1.<br/> | ||
| + | '''Mittigation:'''<br/> | ||
| + | Use SSH Version 2. Use telnet with VTY ACLs. | ||
Revision as of 11:04, 2 September 2011
Contents
 This article is under development....
This article is under development....
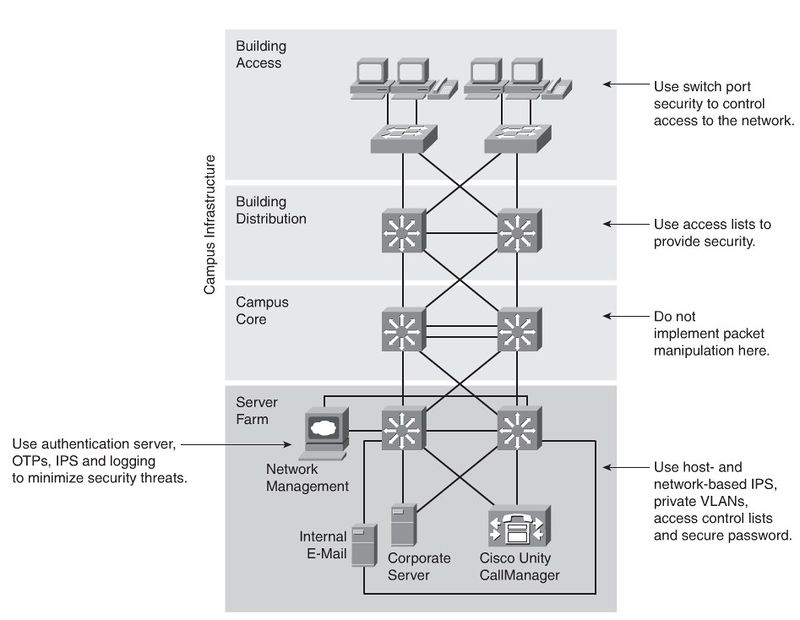
Securing the Campus Infrastructure
Security Infrastructure Services
Rouge Devices
Company employees sometimes plug inexpensive APs into company network devices to extend the network. But securing the wireless APs is not always a priority. Wired Rouge Devices could also be a problem, because of its nature.
Layer 2 Attack Categories
MAC Layer Attacks
MAC address flooding
Frames with unique, invalid source MAC addresses flood the switch, exhausting content addressable memory (CAM) table space, disallowing new entries from valid hosts. Traffic to valid hosts is subsequently flooded out all ports.
Mitigation:
Port security. MAC address VLAN access maps.
VLAN Attacks
VLAN Hopping
By altering the VLAN ID on packets encapsulated for trunking, an attacking device can send or receive packets on various VLANs, bypassing Layer 3 security measures.
Mitigation:
Tighten up trunk configurations and the negotiation state of unused ports. Place unused ports in a common VLAN.
Attacks between devices on a common VLAN
Devices might need protection from one another, even though they are on a common VLAN. This is especially true on service-provider segments that support devices from multiple customers.
Mitigation:
Implement private VLANs (PVLAN).
Spoofing Attacks
DHCP starvation and spoofing
An attacking device can exhaust the address space available to the DHCP servers for a period of time or establish itself as a DHCP server in man-in-the-middle attacks.
Mittigation:
Use DHCP snooping
Spanning-tree compromises
Attacking device spoofs the root bridge in the STP topology. If successful, the network attacker cansee a variety of frames.
Mittigation:
Proactively configure the primary and backup root devices. Enable root guard.
MAC spoofing
Attacking device spoofs the MAC address of a valid host currently in the CAM table. The switch then forwards frames destined for the valid host to the attacking device.
Mittigation:
Use DHCP snooping, port security.
ARP spoofing
Attacking device crafts ARP replies intended for valid hosts. The attackingdevice’s MAC address thenbecomes the destination addressfound in the Layer 2 frames sent by the valid network device.
Mittigation:
Use Dynamic ARP Inspection. DHCP snooping, port security.
Switch Device Attacks
CDP manipulation
Information sent through CDP is transmitted in clear text and unauthenticated, allowing it to be captured and divulge network topology information.
Mittigation:
Disable CDP on all ports where it is not intentionally used.
SSH and Telnet attacks
Telnet packets can be read in clear text. SSH is an option but has securityissues in version 1.
Mittigation:
Use SSH Version 2. Use telnet with VTY ACLs.