Difference between revisions of "CCNA Explorer 4 Network Security"
From Teknologisk videncenter
m (→Logging) |
m (→Sikkerhed) |
||
| Line 1: | Line 1: | ||
{{TOCright}} | {{TOCright}} | ||
=Sikkerhed= | =Sikkerhed= | ||
| + | ==Security Terms== | ||
| + | ;White hat:An individual who looks for vulnerabilities in systems or networks and then reports these vulnerabilities to the owners of the system so that they can be fixed. | ||
| + | ;Black hat: Another term for individuals who use their knowledge of computer systems to break into systems or networks that they are not authorized to use. | ||
| + | ;Hacker:A general term that has historically been used to describe a computer programming expert. More recently, this term is often used in a negative way to describe an individual that attempts to gain unauthorized access to network resources with malicious intent. | ||
| + | ;Cracker:A more accurate term to describe someone who tries to gain unauthorized access to network resources. | ||
| + | ;Phreaker:An individual who manipulates the phone network to cause it to perform a function that is not allowed. | ||
| + | ;Spammer:An individual who sends large quantities of unsolicited e-mail messages. | ||
| + | ;Phisher:Uses e-mail or other means to trick others into providing sensitive information. | ||
| + | ==Hacket Checklist== | ||
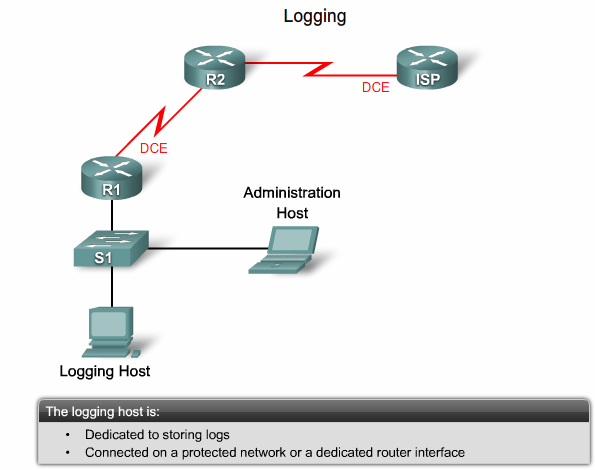
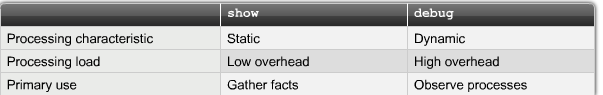
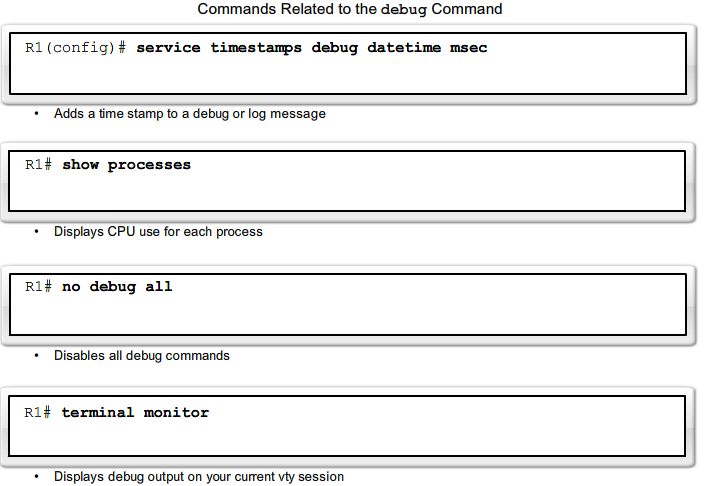
== Logging == | == Logging == | ||
{| | {| | ||
Revision as of 10:12, 25 January 2012
Contents
- 1 Sikkerhed
- 1.1 Security Terms
- 1.2 Hacket Checklist
- 1.3 Logging
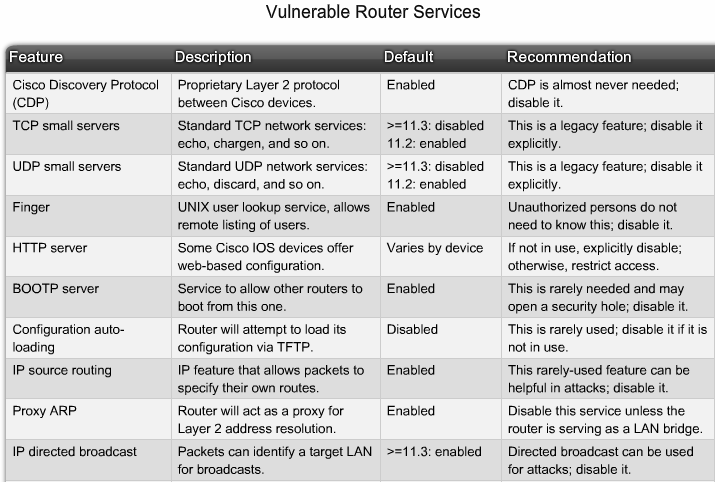
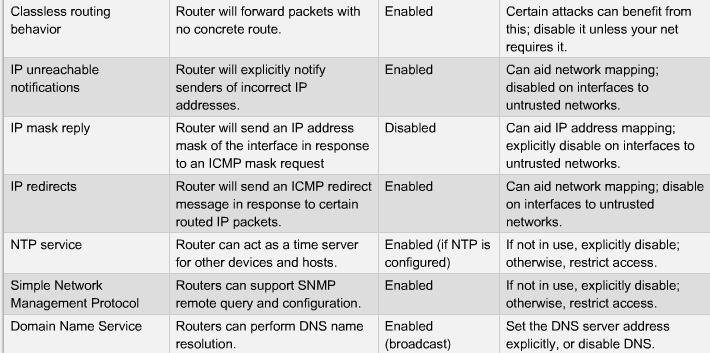
- 1.4 Sårbare Router Services
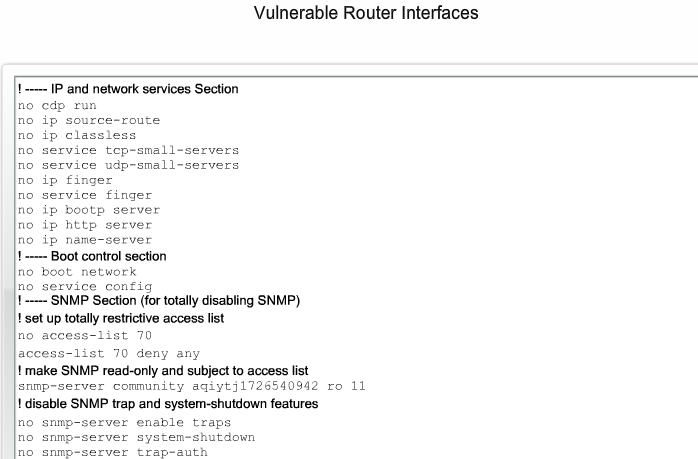
- 1.5 Sårbare Router interfaces
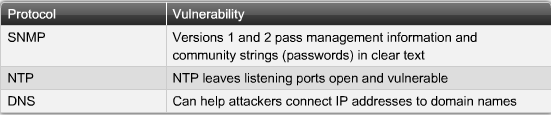
- 1.6 SNMP, NTP og DNS sårbarheder
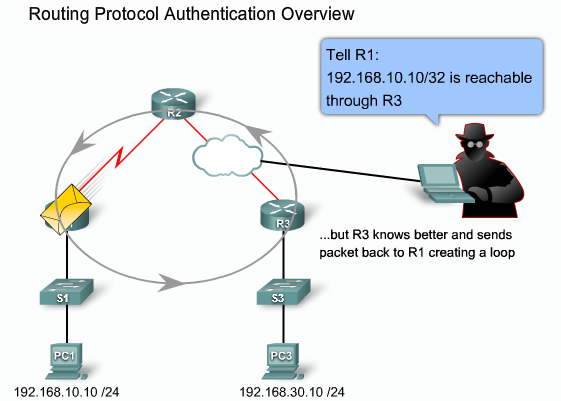
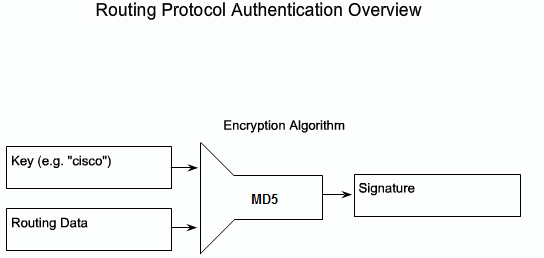
- 1.7 Routenings protokoller sårbarheder
- 1.8 Cisco Auto secure
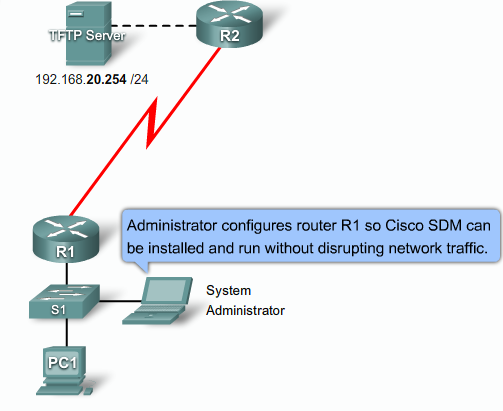
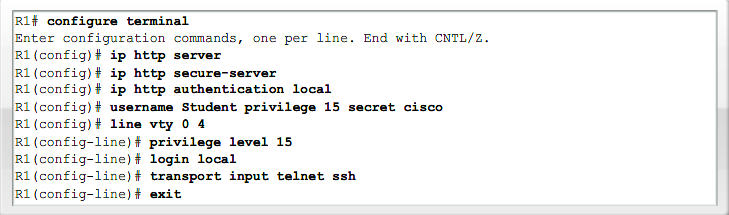
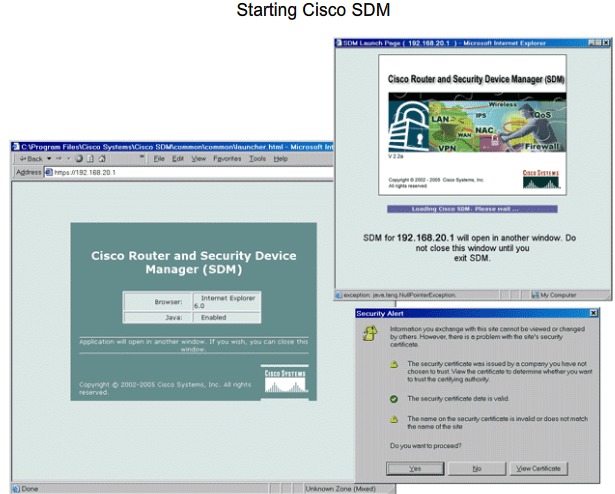
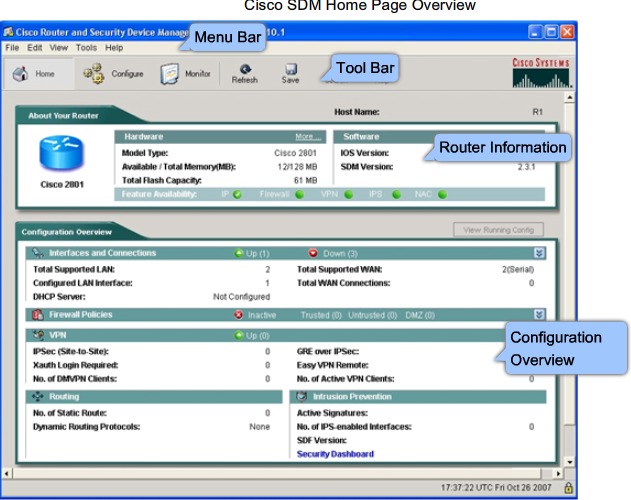
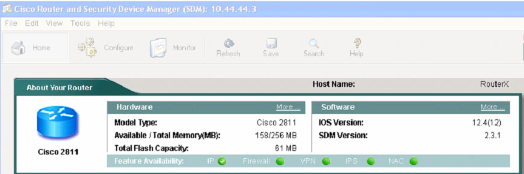
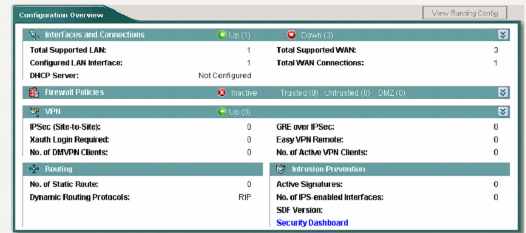
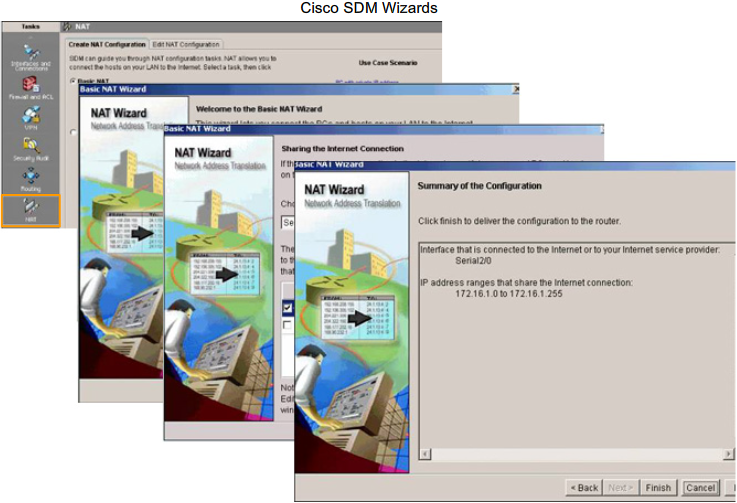
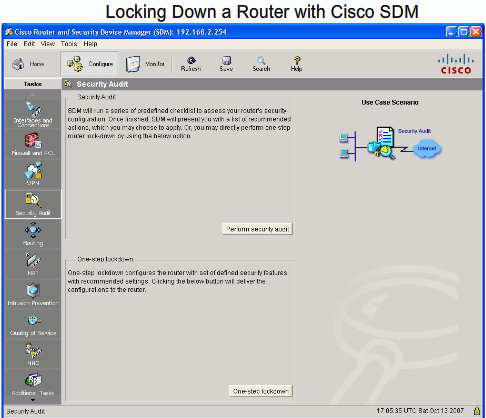
- 1.9 Cisco SDM (Secure Device Manager)
- 1.10 Installer nyeste version af IOS
- 1.11 IOS Filsystemer
- 1.12 Cisco IOS Trouble shooting commands
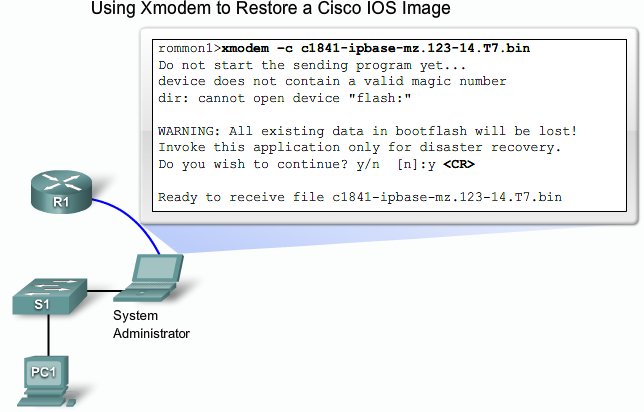
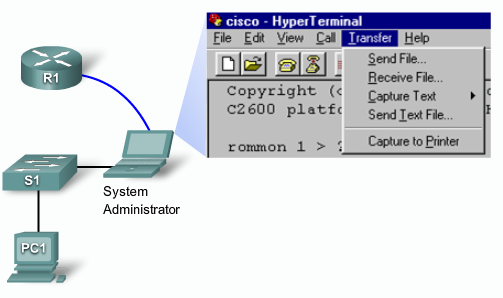
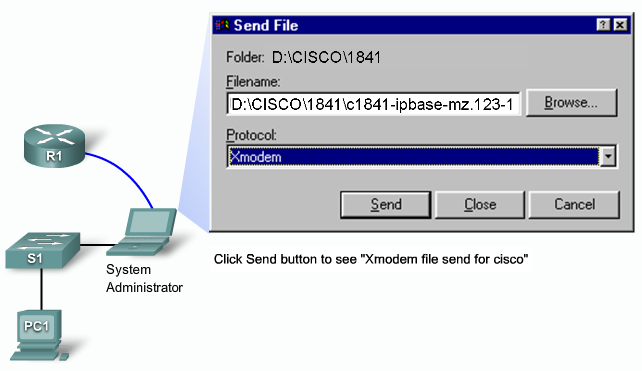
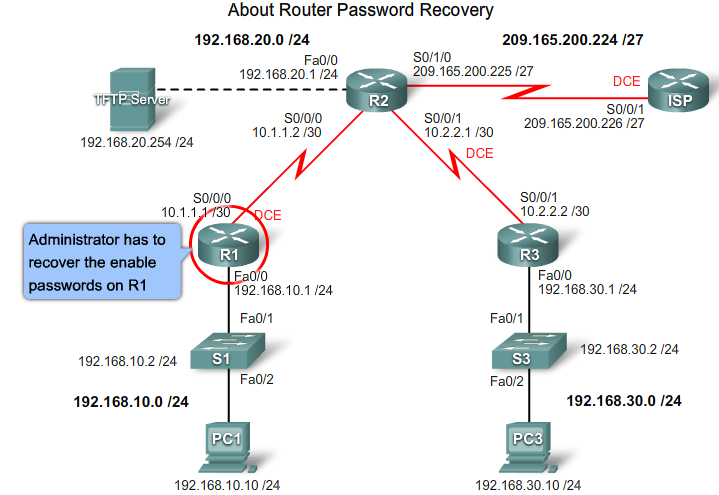
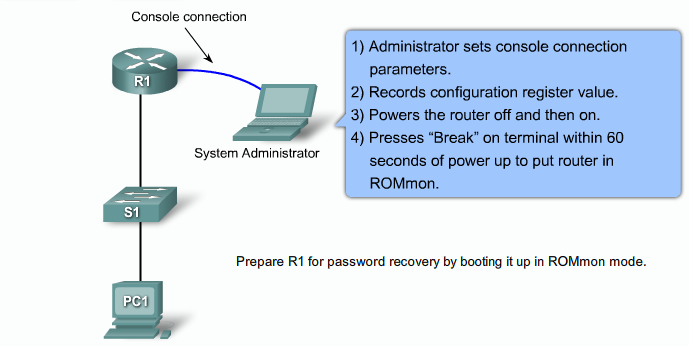
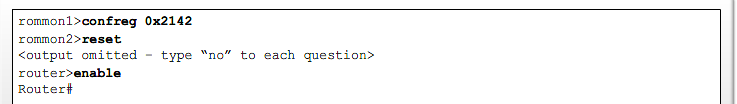
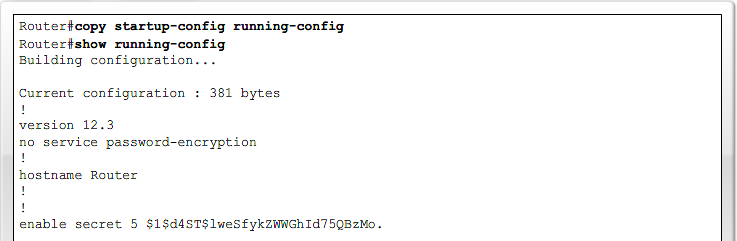
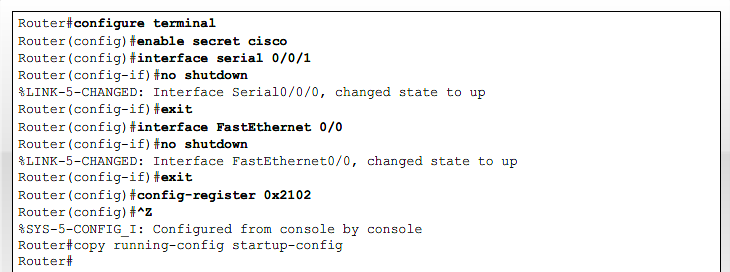
- 1.13 Recovering lost Router password
- 1.14 Opsummering
Sikkerhed
Security Terms
- White hat
- An individual who looks for vulnerabilities in systems or networks and then reports these vulnerabilities to the owners of the system so that they can be fixed.
- Black hat
- Another term for individuals who use their knowledge of computer systems to break into systems or networks that they are not authorized to use.
- Hacker
- A general term that has historically been used to describe a computer programming expert. More recently, this term is often used in a negative way to describe an individual that attempts to gain unauthorized access to network resources with malicious intent.
- Cracker
- A more accurate term to describe someone who tries to gain unauthorized access to network resources.
- Phreaker
- An individual who manipulates the phone network to cause it to perform a function that is not allowed.
- Spammer
- An individual who sends large quantities of unsolicited e-mail messages.
- Phisher
- Uses e-mail or other means to trick others into providing sensitive information.