Difference between revisions of "RIP JUNOS"
m (added Category:SRX Packet-Based Forwarding using HotCat) |
m (added Category:SRX Flow-Based Forwarding using HotCat) |
||
| Line 238: | Line 238: | ||
[[Category:Juniper]] | [[Category:Juniper]] | ||
[[Category:SRX Packet-Based Forwarding]] | [[Category:SRX Packet-Based Forwarding]] | ||
| + | [[Category:SRX Flow-Based Forwarding]] | ||
Latest revision as of 14:31, 16 October 2014
Contents
Setup
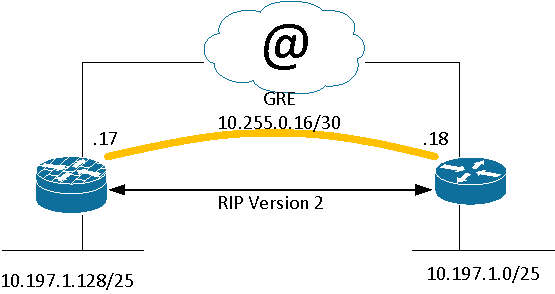
Cisco router er forbundet via en GRE tunnel til en SRX100. Netværket hedder 10.255.0.16/30 på tunnellen.
Netværket bag Cisco routeren 10.197.1.0/25 samt de statiske routes skal sendes til SRX100'eren og 10.197.1.128/25 netværket bag SRX100'eren skal sendes tilbage til Cisco routeren.
Cisco configurationen
Skal tillade det internt 10.197.1.0/25 netværk og nogle statisk konfigurerede host routes på tværs af tunnellen.
EM565039#<input>show run</input>
router rip
version 2
redistribute static
passive-interface ATM0.34
network 10.0.0.0
distribute-list prefix RIP-OUT out
no auto-summary
!
ip prefix-list RIP-OUT seq 5 deny 0.0.0.0/0
ip prefix-list RIP-OUT seq 10 permit 10.197.0.0/16 le 32
ip prefix-list RIP-OUT seq 20 permit 87.48.0.0/16 ge 32
!deny 0.0.0.0/0 er lidt dobbelt konfekt med det virker:-)
Verification
Her sikrer vi os at de rigtige netværk bliver sendt til naboen over tunnellen
EM565039#<input>debug ip rip</input>
RIP protocol debugging is on
Oct 1 20:56:32.403 UTC+2: RIP: sending v2 update to 224.0.0.9 via Tunnel20 (10.255.0.18)
Oct 1 20:56:32.403 UTC+2: RIP: build update entries
Oct 1 20:56:32.403 UTC+2: <notice>10.197.1.0/25 via 0.0.0.0, metric 1, tag 0</notice>
Oct 1 20:56:32.403 UTC+2: <notice>87.48.131.50/32 via 0.0.0.0, metric 1, tag 0</notice>
Oct 1 20:56:32.403 UTC+2: <notice>87.48.131.54/32 via 0.0.0.0, metric 1, tag 0</notice>
Oct 1 20:56:32.403 UTC+2: <notice>87.48.133.100/32 via 0.0.0.0, metric 1, tag 0</notice>Nu er vi sikker på Cisco enden sender RIP routes så lad os kigge på Juniper enden
Juniper konfiguration
RIP
Konfigurationen af rip ligger under protocol rip. Sender version 2 RIP beskeder som multicast, og modtager kun version 2 beskeder.
[edit protocols rip]
root@SRX100# <input>show</input>
send multicast;
receive version-2;
group RIP-GR {
neighbor gr-0/0/0.20;
}Hvis vi kontrollerer route tabellen ser vi ingen lærte rip routes:
[edit protocols rip]
root@SRX100# <input>run show route protocol rip</input>
inet.0: 25 destinations, 25 routes (25 active, 0 holddown, 0 hidden)
+ = Active Route, - = Last Active, * = Both
224.0.0.9/32 *[RIP/100] 00:03:27, metric 1
MultiRecv
inet6.0: 19 destinations, 25 routes (19 active, 0 holddown, 0 hidden)RIP statistikkerne siger at vi ikke modtager nogle pakker via tunnelen, selv om vi har verificeret Cisco routeren sender.
root@SRX100# run show rip statistics
RIPv2 info: port 520; holddown 120s.
rts learned rts held down rqsts dropped resps dropped
0 0 0 0
gr-0/0/0.20: 0 routes learned; 0 routes advertised; timeout 180s; update interval 30s
Counter Total Last 5 min Last minute
------- ----------- ----------- -----------
Updates Sent 0 0 0
Triggered Updates Sent 0 0 0
Responses Sent 0 0 0
Bad Messages 0 0 0
RIPv1 Updates Received 0 0 0
RIPv1 Bad Route Entries 0 0 0
RIPv1 Updates Ignored 0 0 0
<notice>RIPv2 Updates Received 0 0 0</notice>
RIPv2 Bad Route Entries 0 0 0
RIPv2 Updates Ignored 0 0 0
Authentication Failures 0 0 0
RIP Requests Received 0 0 0
RIP Requests Ignored 0 0 0
none 0 0 0Security Zones
SRX firewallen kører flow-mode og RIP skal tillades i sikkerheds zonen, GRE interfacet tilhører.
Zonen her hedder VOICE da den bruges til IPT.
[edit security zones security-zone VOICE]
root@SRX100# <input>show</input>
host-inbound-traffic {
system-services {
ping;
}
<notice>protocols {
rip;
}</notice>
}Og straks begynder opdateringerne at trille ind:
root@SRX100# <input>run show rip statistics</input>
RIPv2 info: port 520; holddown 120s.
rts learned rts held down rqsts dropped resps dropped
4 0 0 0
gr-0/0/0.20: 4 routes learned; 0 routes advertised; timeout 180s; update interval 30s
Counter Total Last 5 min Last minute
------- ----------- ----------- -----------
Updates Sent 0 0 0
Triggered Updates Sent 0 0 0
Responses Sent 0 0 0
Bad Messages 0 0 0
RIPv1 Updates Received 0 0 0
RIPv1 Bad Route Entries 0 0 0
RIPv1 Updates Ignored 0 0 0
<notice>RIPv2 Updates Received 2 0 0</notice>
RIPv2 Bad Route Entries 0 0 0
RIPv2 Updates Ignored 0 0 0
Authentication Failures 0 0 0
RIP Requests Received 0 0 0
RIP Requests Ignored 0 0 0
none 0 0 0
root@SRX100# <input>run show route protocol rip</input>
inet.0: 29 destinations, 29 routes (29 active, 0 holddown, 0 hidden)
+ = Active Route, - = Last Active, * = Both
<notice>10.197.1.0/25 *[RIP/100] 00:01:16, metric 2, tag 0
> to 10.255.0.18 via gr-0/0/0.20
87.48.131.50/32 *[RIP/100] 00:01:16, metric 2, tag 0
> to 10.255.0.18 via gr-0/0/0.20
87.48.131.54/32 *[RIP/100] 00:01:16, metric 2, tag 0
> to 10.255.0.18 via gr-0/0/0.20
87.48.133.100/32 *[RIP/100] 00:01:16, metric 2, tag 0
> to 10.255.0.18 via gr-0/0/0.20</notice>
224.0.0.9/32 *[RIP/100] 00:10:44, metric 1
MultiRecvMen der bliver ikke sendt nogle updates den anden retning
EM565039#show ip route rip
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route, H - NHRP, l - LISP
+ - replicated route, % - next hop override
Gateway of last resort is 93.166.111.101 to network 0.0.0.0
EM565039#<input>debug ip rip</input>
RIP protocol debugging is on
EM565039#
Oct 1 21:22:35.884 UTC+2: RIP: sending v2 update to 224.0.0.9 via Tunnel20 (10.255.0.18)
Oct 1 21:22:35.884 UTC+2: RIP: build update entries
Oct 1 21:22:35.884 UTC+2: 10.197.1.0/25 via 0.0.0.0, metric 1, tag 0
Oct 1 21:22:35.884 UTC+2: 87.48.131.50/32 via 0.0.0.0, metric 1, tag 0
Oct 1 21:22:35.884 UTC+2: 87.48.131.54/32 via 0.0.0.0, metric 1, tag 0
Oct 1 21:22:35.884 UTC+2: 87.48.133.100/32 via 0.0.0.0, metric 1, tag 0
EM565039#Routing Policies
Der er endnu ikke oprettet nogle import og export politikker.
- import
- Alt modtaget trafik bliver automatisk sendt til route tabellen. implicit permit
- export
- Intet bliver taget fra route tabellen og send til naboer uden en explicit permit. implicit deny
Alle direkte forbundne netværk bliver exporteret hvis de ligger indenfor 10.197.1.0/24 og har en /24 eller længere maske.
[edit policy-options policy-statement RIP-EXPORT]
root@SRX100# <input>show</input>
term 1 {
from {
protocol direct;
route-filter 10.197.1.0/24 orlonger;
}
then accept;
}
[edit protocols rip]
root@SRX100# <input>show</input>
send multicast;
receive version-2;
group RIP-GR {
<notice>export RIP-EXPORT;</notice>
neighbor gr-0/0/0.20;
}Og SRX'en begynder nu at sende updates
root@SRX100# <input>run show rip statistics</input>
RIPv2 info: port 520; holddown 120s.
rts learned rts held down rqsts dropped resps dropped
4 0 0 0
gr-0/0/0.20: 4 routes learned; 1 routes advertised; timeout 180s; update interval 30s
Counter Total Last 5 min Last minute
------- ----------- ----------- -----------
<notice>Updates Sent 1 0 0
Triggered Updates Sent 1 0 0</notice>
Responses Sent 0 0 0
Bad Messages 0 0 0
RIPv1 Updates Received 0 0 0
RIPv1 Bad Route Entries 0 0 0
RIPv1 Updates Ignored 0 0 0
RIPv2 Updates Received 29 11 3
RIPv2 Bad Route Entries 0 0 0
RIPv2 Updates Ignored 0 0 0
Authentication Failures 0 0 0
RIP Requests Received 0 0 0
RIP Requests Ignored 0 0 0
none 0 0 0Cisco routeren begynder også at modtage opdateringer
Oct 1 21:32:24.909 UTC+2: RIP: received v2 update from 10.255.0.17 on Tunnel20
Oct 1 21:32:24.909 UTC+2: <notice>10.197.1.128/25</notice> via 0.0.0.0 in 1 hops
EM565039#<input>show ip route rip</input>
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route, H - NHRP, l - LISP
+ - replicated route, % - next hop override
Gateway of last resort is 93.166.111.101 to network 0.0.0.0
10.0.0.0/8 is variably subnetted, 7 subnets, 3 masks
<notice>R 10.197.1.128/25 [120/1] via 10.255.0.17, 00:00:02, Tunnel20</notice>
EM565039#