Difference between revisions of "Netband Project - IOS firewall"
From Teknologisk videncenter
(→Verificcation) |
(→Configuration) |
||
| Line 10: | Line 10: | ||
[[Image:Netband-cbac.jpg|thumb|none|600px|CBAC]] | [[Image:Netband-cbac.jpg|thumb|none|600px|CBAC]] | ||
===Configuration=== | ===Configuration=== | ||
| − | <pre> ip inspect name iosfw ftp | + | <pre> ip inspect audit-trail |
| + | ip inspect name iosfw ftp | ||
ip inspect name iosfw tcp | ip inspect name iosfw tcp | ||
ip inspect name iosfw udp | ip inspect name iosfw udp | ||
| − | ip inspect name iosfw http | + | ip inspect name iosfw http audit-trail on |
ip inspect name iosfw https | ip inspect name iosfw https | ||
! | ! | ||
Revision as of 11:02, 27 April 2009
<accesscontrol>NetBand</accesscontrol> This page is part of the Netband Project
Contents
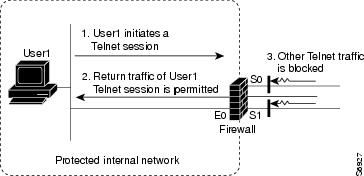
Context Based Access Control (CBAC)
- filters TCP and UDP packets based on application-layer protocol session information.
- more flexible than access control lists, that checks packets at the network layer, or at most, the transport layer
- inspects packet sequence numbers in TCP connections
- detects unusually high rates of new connections and issue alert messages.
- creates temporary openings in the return acl to allow traffic back in.
Configuration
ip inspect audit-trail ip inspect name iosfw ftp ip inspect name iosfw tcp ip inspect name iosfw udp ip inspect name iosfw http audit-trail on ip inspect name iosfw https ! interface FastEthernet0/0 description OUTSIDE ip inspect iosfw in ip access-group 101 in ! access-list 101 permit udp any eq isakmp any eq isakmp access-list 101 permit esp any any access-list 101 permit tcp any any eq 22 access-list 101 deny ip any any log
Verificcation
B1rt1#sh ip inspect sessions Half-open Sessions Session 65E15880 (192.168.0.1:123)=>(10.255.255.13:123) udp SIS_OPENING