Difference between revisions of "Netband Project - IOS firewall"
From Teknologisk videncenter
(→Configuration) |
(→Verification) |
||
| Line 62: | Line 62: | ||
===Verification=== | ===Verification=== | ||
| − | <pre>B1rt1#sh ip port-map | + | <pre>B1rt1#sh ip port-map http |
| − | Default mapping: | + | Default mapping: http tcp port 80 system defined |
| − | + | Default mapping: http tcp port 8001 user defined | |
| − | |||
| − | |||
| − | Default mapping: | ||
| − | |||
| − | |||
| − | |||
| − | |||
</pre> | </pre> | ||
==External Links== | ==External Links== | ||
[http://www.cisco.com/en/US/docs/ios/sec_data_plane/configuration/guide/sec_cfg_content_ac_ps6350_TSD_Products_Configuration_Guide_Chapter.html Cisco IOS Security Configuration Guide] | [http://www.cisco.com/en/US/docs/ios/sec_data_plane/configuration/guide/sec_cfg_content_ac_ps6350_TSD_Products_Configuration_Guide_Chapter.html Cisco IOS Security Configuration Guide] | ||
Revision as of 09:01, 28 April 2009
<accesscontrol>NetBand</accesscontrol> This page is part of the Netband Project
Contents
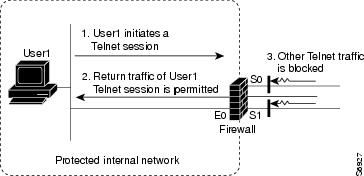
Context Based Access Control (CBAC)
- filters TCP and UDP packets based on application-layer protocol session information.
- more flexible than access control lists, that checks packets at the network layer, or at most, the transport layer
- inspects packet sequence numbers in TCP connections
- detects unusually high rates of new connections and issue alert messages.
- creates temporary openings in the return acl to allow traffic back in.
Configuration
- Note: The router only keeps track of the configured protocols. Unconfigured protocols are allowed through without inspection or tracking if the interface acls permit
ip inspect audit-trail ip inspect name iosfw ftp ip inspect name iosfw tcp ip inspect name iosfw udp ip inspect name iosfw http ip inspect name iosfw https ! interface FastEthernet0/0 description OUTSIDE ip inspect iosfw out ip access-group 101 in ! access-list 101 permit udp any eq isakmp any eq isakmp access-list 101 permit esp any any access-list 101 permit tcp any any eq 22 access-list 101 deny ip any any log
Verification
B1rt1#sh ip inspect sessions Established Sessions Session 65E14830 (10.2.1.10:3935)=>(195.137.194.128:80) http SIS_OPEN Session 65E15310 (10.2.1.10:3936)=>(195.137.194.128:80) http SIS_OPEN Session 65E15058 (10.2.1.10:3937)=>(195.137.194.128:80) http SIS_OPEN Session 65E155C8 (10.2.1.10:3934)=>(195.137.194.128:80) http SIS_OPEN
- Syslog audit trail
Apr 27 10:22:06.521: %FW-6-SESS_AUDIT_TRAIL_START: Start http session: initiator (10.2.1.10:3898) -- responder (195.137.194.128:80) Apr 27 10:22:18.044: %FW-6-SESS_AUDIT_TRAIL: Stop http session: initiator (10.2.1.10:3898) sent 1247 bytes -- responder (195.137.194.128:80) sent 144791 bytes Apr 27 10:48:36.770: %FW-6-SESS_AUDIT_TRAIL_START: Start tcp session: initiator (10.2.1.10:3958) -- responder (192.168.1.1:23) Apr 27 10:49:30.769: %FW-6-SESS_AUDIT_TRAIL: Stop tcp session: initiator (10.2.1.10:3958) sent 74 bytes -- responder (192.168.1.1:23) sent 255 bytes
Intrusion Prevention System (IPS)
- See Netband Project - IOS ips for further information and configuration
Authentication Proxy
Port to Application Mapping (PAM)
- customize TCP or UDP port numbers for network services or applications.
- information in the PAM table enables CBAC supported services to run on nonstandard ports
Configuration
ip port-map http port tcp 8001 description Alternative http port ... ip inspect name iosfw http ...
Verification
B1rt1#sh ip port-map http Default mapping: http tcp port 80 system defined Default mapping: http tcp port 8001 user defined