Difference between revisions of "Netband Project - CoPP"
From Teknologisk videncenter
(→Configuration) |
(→External Links) |
||
| Line 62: | Line 62: | ||
==External Links== | ==External Links== | ||
| − | + | Prior to 12.4(4)T | |
<br> | <br> | ||
| + | [http://www.cisco.com/en/US/prod/collateral/iosswrel/ps6537/ps6586/ps6642/prod_white_paper0900aecd804fa16a.html CoPP] | ||
| + | <br> | ||
| + | [http://www.cisco.com/web/about/security/intelligence/coppwp_gs.html CoPP best practice design guide] | ||
[http://www.cisco.com/en/US/docs/ios/qos/configuration/guide/ctrl_plane_prot_ps6441_TSD_Products_Configuration_Guide_Chapter.html CoP] | [http://www.cisco.com/en/US/docs/ios/qos/configuration/guide/ctrl_plane_prot_ps6441_TSD_Products_Configuration_Guide_Chapter.html CoP] | ||
Revision as of 12:40, 15 April 2009
<accesscontrol>NetBand</accesscontrol> This page is part of the Netband Project
Control Plane Policing
- The Control Plane Policing feature allows users to configure a quality of service (QoS) filter that manages the traffic flow of control plane packets to protect the control plane of Cisco IOS routers and switches against reconnaissance and denial-of-service (DoS) attacks.
- CoPP can help maintain packet forwarding and protocol states despite an attack or heavy traffic load on the router or switch.
- Uses MQC (Modular QoS CLI)
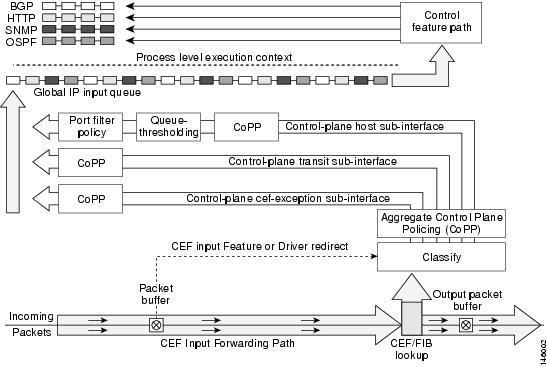
- Control Plane Policing Architecture
- Prior to 12.4(4)T it was only possible to configure the aggregate interface
Configuration
Versions prior to 12.4(4)T ip access-list extended coppacl-igp permit ospf any host 224.0.0.5 permit ospf any host 224.0.0.6 permit ospf any any ! ip access-list extended coppacl-management permit tcp 10.0.0.0 0.255.255.255 any eq 22 permit tcp 10.0.0.0 0.255.255.255 any eq telnet permit udp host 10.1.1.10 any eq snmp permit udp host 10.0.0.11 any eq ntp ! ip access-list extended coppacl-monitoring permit icmp any any ttl-exceeded permit icmp any any port-unreachable permit icmp any any echo-reply permit icmp any any echo ! ip access-list extended coppacl-critical-app permit udp host 0.0.0.0 host 255.255.255.255 eq bootps permit udp host 10.1.1.11 eq bootps any eq bootps ! class-map match-all coppclass-igp match access-group name coppacl-igp class-map match-all coppclass-management match access-group name coppacl-management class-map match-all coppclass-monitoring match access-group name coppacl-monitoring class-map match-all coppclass-critical-app match access-group name coppacl-critical-app class-map match-all coppclass-layer2 match protocol arp ! policy-map copp-policy class coppclass-igp class coppclass-management police rate 250 pps conform-action transmit exceed-action drop class coppclass-monitoring police rate 50 pps conform-action transmit exceed-action drop class coppclass-critical-app police rate 75 pps conform-action transmit exceed-action drop class coppclass-layer2 police rate 25 pps conform-action transmit exceed-action drop class class-default police rate 10 pps conform-action transmit exceed-action drop ! control-plane service-policy input copp-policy
External Links
Prior to 12.4(4)T
CoPP
CoPP best practice design guide
CoP