CCNP SWITCH/Securing the Campus Infrastructure
Securing the Campus Infrastructure
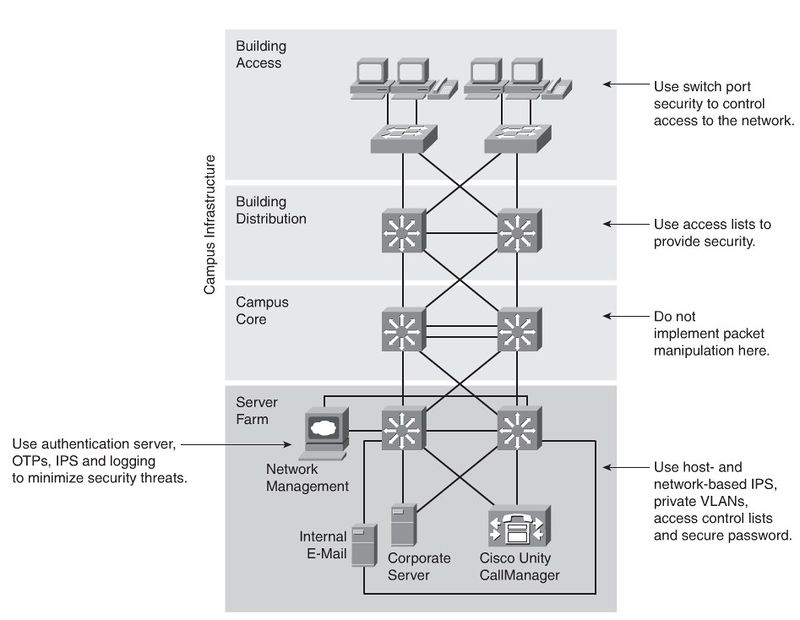
Security Infrastructure Services
Rouge Devices
Company employees sometimes plug inexpensive APs into company network devices to extend the network. But securing the wireless APs is not always a priority. Wired Rouge Devices could also be a problem, because of its nature.
Layer 2 Attack Categories
MAC Layer Attacks
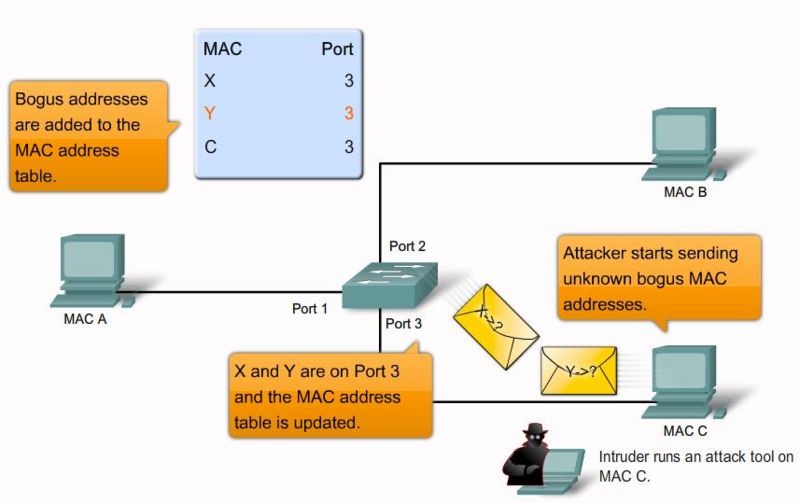
MAC address flooding
Frames with unique, invalid source MAC addresses flood the switch, exhausting content addressable memory (CAM) table space, disallowing new entries from valid hosts. Traffic to valid hosts is subsequently flooded out all ports.
Mitigation:
Port security. MAC address VLAN access maps.
Switch(config-if)#<input>switchport port-security</input>
Switch(config-if)#<input>switchport port-security maximum <value></input>
Switch(config-if)#<input>switchport port-security <mac-addressmac-address></input>
Switch(config-if)#<input>switchport port-security violation{shutdown |restrict |
protect}</input>Debugging:
switch# <input>show port-security interface fastethernet0/1</input>
Port Security : Enabled
Port Status : Secure-up
Violation Mode : Restrict
Aging Time : <notice>60 mins</notice>
Aging Type : Inactivity
SecureStatic Address Aging : Enabled
Maximum MAC Addresses : 2
Total MAC Addresses : 1
Configured MAC Addresses : 0
Sticky MAC Addresses : 0
Last Source Address:Vlan : 001b.d513.2ad2:5
Security Violation Count : 0Security Violation Modes
- Protect: When the number of secure MAC addresses reaches the limit allowed on the port, packets with unknown source addresses are dropped.
- Restrict: When the number of secure MAC addresses reaches the limit allowed on the port, packets with unknown source addresses are dropped. A SNMP trap is sent, a syslog message is logged, and the violation counter increments.
- Shutdown(Default[1]): In this mode, a port security violation causes the interface to immediately become error-disabled and turns off the port LED. It also sends an SNMP trap, logs a syslog message.
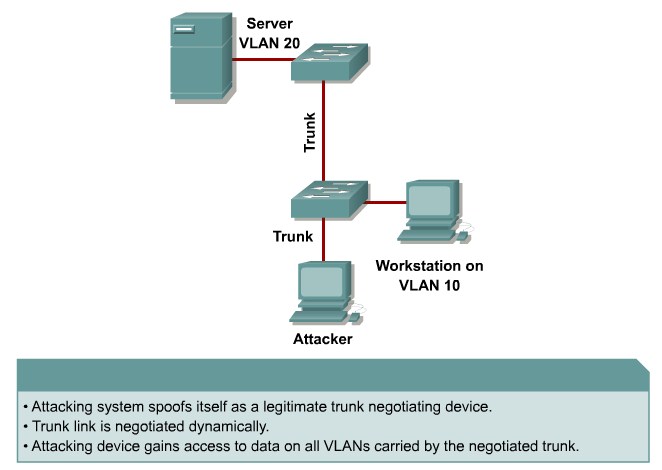
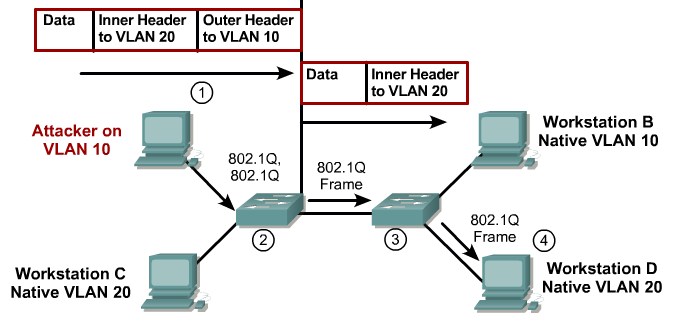
VLAN Attacks
VLAN Hopping
By altering the VLAN ID on packets encapsulated for trunking, an attacking device can send or receive packets on various VLANs, bypassing Layer 3 security measures.
Mitigation:
Tighten up trunk configurations and the negotiation state of unused ports. Place unused ports in a common unused VLAN. Remember to protect against DTP attacks and VLAN hopping.
Attacks between devices on a common VLAN
Devices might need protection from one another, even though they are on a common VLAN. This is especially true on service-provider segments that support devices from multiple customers.
Mitigation:
Implement private VLANs (PVLAN).
Spoofing Attacks
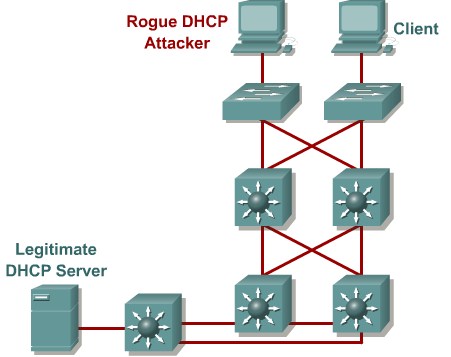
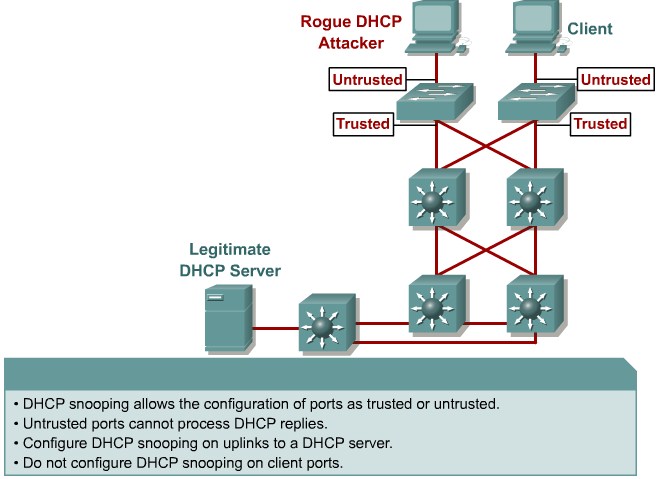
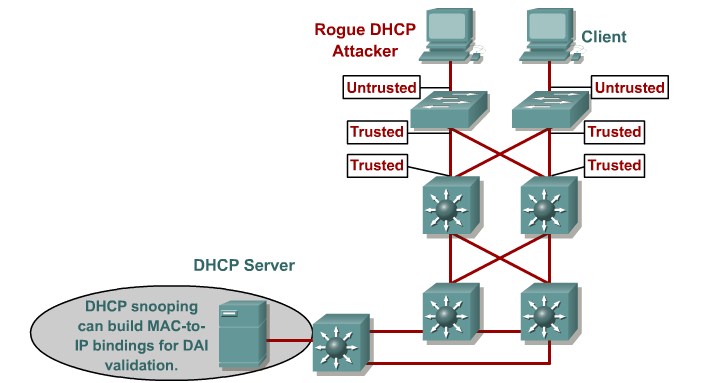
DHCP starvation and spoofing
An attacking device can exhaust the address space available to the DHCP servers for a period of time or establish itself as a DHCP server in man-in-the-middle attacks.
Mittigation:
Use DHCP snooping
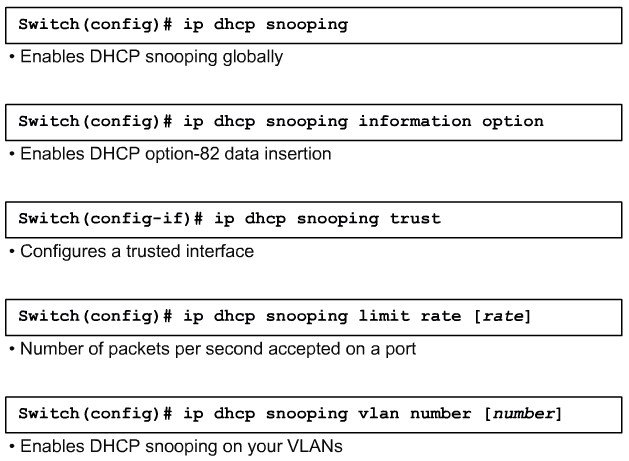
Configure DHCP Snooping
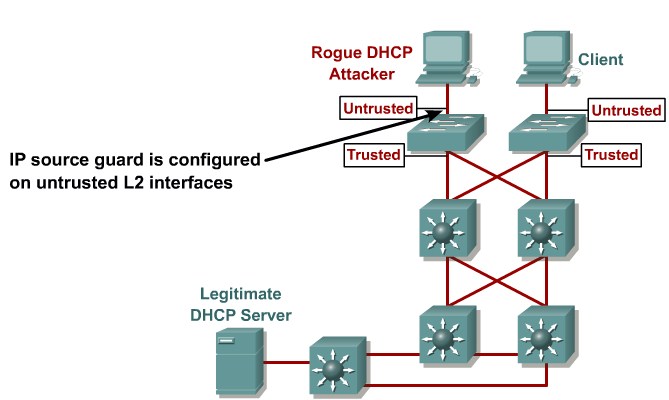
IP Source spoofing
Attacking devices spoof there source address to pretend to be someone else
Mittigation:
Enable IP Source Guard
Configure IP Source Guard
Spanning-tree compromises
Attacking device spoofs the root bridge in the STP topology. If successful, the network attacker cansee a variety of frames.
Mittigation:
Proactively configure the primary and backup root devices. Enable root guard.
MAC spoofing
Attacking device spoofs the MAC address of a valid host currently in the CAM table. The switch then forwards frames destined for the valid host to the attacking device.
Mittigation:
Use DHCP snooping, port security.
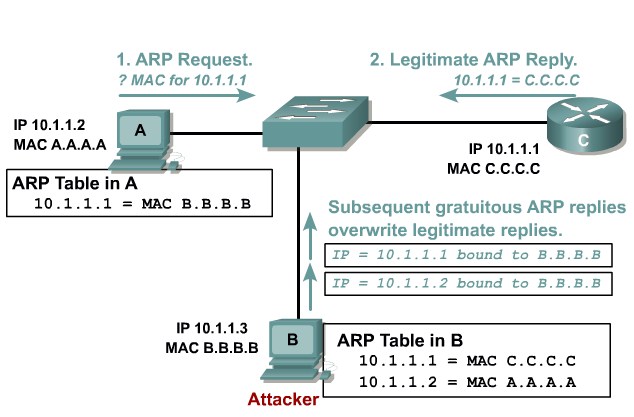
ARP spoofing
Attacking device crafts ARP replies intended for valid hosts. The attackingdevice’s MAC address thenbecomes the destination addressfound in the Layer 2 frames sent by the valid network device.
Mittigation:
Use Dynamic ARP Inspection. DHCP snooping, port security.
Switch# <input>configure terminal</input>
Enter configuration commands, one per line. End with CNTL/Z.
Switch(config)# <input>ip arp inspection vlan 10</input>
Switch(config)# <input>interface gigabitEthernet 1/1</input>
Switch(config-if)# <input>description Uplink Port</input>
Switch(config-if)# <input>ip arp inspection trust</input>
Switch(config-if)# <input>end</input>Switch Device Attacks
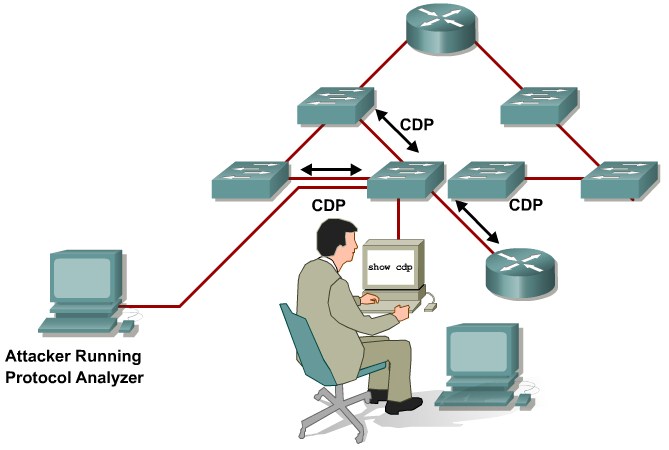
CDP manipulation
Information sent through CDP is transmitted in clear text and unauthenticated, allowing it to be captured and divulge network topology information.
Mittigation:
Disable CDP on all ports where it is not intentionally used.
Switch(config)# <input>no cdp run</input>
Switch(config-if)# <input>no cdp enable</input>Configure LLDP
Switch(config)# <input>lldp run</input>
Switch(config-if)# <input>lldp enable</input>
Switch(config-if)# <input>end</input>
switch# <input>show lldp neighbor</input>
Capability codes:
(R) Router, (B) Bridge, (T) Telephone, (C) DOCSIS Cable Device
(W) WLAN Access Point, (P) Repeater, (S) Station, (O) Other
Device ID Local Intf Hold-time Capability Port ID
c2960-8 Fa0/8 120 B Fa0/8
Total entries displayed: 1SSH and Telnet attacks
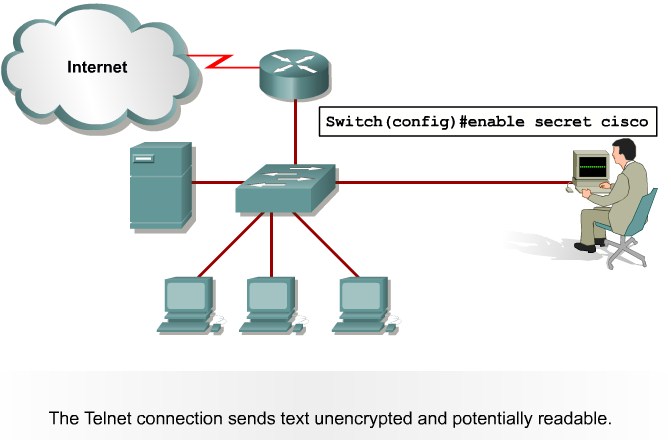
Telnet packets can be read in clear text. SSH is an option but has securityissues in version 1.
Mittigation:
Use SSH Version 2. Use telnet with VTY ACLs.
Switch(config)# <input>aaa new-model</input>
Switch(config)# <input>aaa authentication login default local</input>
Switch(config)# <input>username Joe password User</input>
Switch(config)# <input>ip domain-name sshtest.lab</input>
Switch(config)# <input>crypto key generate key</input>
Switch(config)# <input>line vty 0 15</input>
Switch(config-line)# <input>login local</input>
Switch(config-line)# <input>transport input ssh</input>VTY ACLs
Switch(config)# <input>access-list 100 permit ip 10.1.1.0 0.0.0.255 any</input>
Switch(config)# <input>line vty 0 15</input>
Switch(config-line)#<input> access-class 100 in</input>AAA
Authentication
Authentication provides a method for handling the following:
- User identification
- Login and password dialog
- Challenge and response
- Messaging
- Encryption
Switch(config)# <input>aaa new-model</input>
Switch(config)# <input>aaa authentication login TEST tacacs+</input>
Switch(config)# <input>tacacs-server host 192.168.100.100</input>
Switch(config)# <input>line vty 0 4</input>
Switch(config-line)# <input>login authentication TEST</input>Authorization
Switches and routers use AAA authorization to limit the services that are available to specific users. AAA authorization uses information retrieved from the user’s profile, which is located either in the local user database on the switch or on the security server.
Switch(config)# <input>aaa new-model</input>
Switch(config)#<input>aaa authorization commands 0 default if-authenticated group tacacs+</input>
Switch(config)# <input>line vty 0 4</input>
Switch(config-line)# <input>authorization commands 0 default</input>Accounting
AAA supports the following six different accounting types:
- Network accounting:Provides information for all PPP, SLIP, or ARAP sessions, including packet and byte counts.
- Connection accounting:Provides information about all outbound connections made from the network, such as Telnet and rlogin.
- EXEC accounting:Provides information about user EXEC terminal sessions (user shells) on the network access server, including username, date, start and stop times, the access server IP address, and (for dial-in users) the telephone number from which the call originated.
- System accounting:Provides information about all system-level events (for example, when the system reboots and when accounting is turned on or off).
- Command accounting:Provides information about the EXEC shell commands for a specified privilege level executed on a network access server.
- Resource accounting:Provides start and stop record support for calls that have passed user authentication.
Switch(config)# <input>aaa new-model</input>
Switch(config)# <input>aaa accounting exec default start-stop group tacacs+</input>
Switch(config)# <input>line vty 0 4</input>
Switch(config-line)# <input>accounting exec default</input>802.1X
se CCNP_3_Minimizing_Service_Loss_and_Data_Theft_in_a_Campus_Network#802.1x_Port-Based_Authentication
Organizational Security Policies
A well-established security policy has these characteristics:
- Provides a process for auditing existing network security
- Provides a general security framework for implementing network security
- Defines disallowed behaviors toward electronic data
- Determines which tools and procedures are needed for the organization
- Communicates consensus among a group of key decision makers and defines responsibilities of users and administrators
- Defines a process for handling network security incidents
- Enables an enterprisewide, all-site security implementation and enforcement plan
Securing Switch Devices and Protocols
Device security best practice: Configure strong system passwords.
- Restrict management access using ACLs.
- Secure physical access to the console.
- Secure access to vty lines.
- Configure system warning banners.
- Disable unneeded or unused services.
- Trim and minimize the use of CDP/LLDP.
- Disable the integrated HTTP daemon (where appropriate).
- Configure basic system logging (syslog).
- Secure SNMP.
- Limit trunking connections and propagated VLANs.
- Secure the spanning-tree topology.
Disabling Unneeded or Unused Services
- TCP Small Servers (Echo, Chargen, Discard, Daytime)
- UDP Small Servers (Echo, Discard, Chargen)
- Finger
- BOOTP server
- Identification service
- NTP without authentication
- Source routing
- ICMP unreachables
- ICMP redirects
- Directed broadcast forwarding
Monitoring Performance with SPAN and VSPAN
Switch(config)# monitor session 1 source interface FastEthernet 3/1
Switch(config)# monitor session 1 destination interface FastEthernet 3/5Se også
Catalyst Switched Port Analyzer (SPAN) Configuration Example
Configuring SPAN
Embedded Event Manager (EEM)
This page is part of the Netband Project
Embedded Event Manager is a service on IOS based routers witch monitors the system and takes action on events like log messages, routing updates or specific time of day.
Configuration
This code shows how to monitor the log for successfull login attempts and send an email.
event manager applet LogIn-Succeded event syslog pattern "SSH-5-SSH2_USERAUTH.*Succeeded" maxrun 20 action 1.0 mail server "<ip-adr-of-smtp-server>" to "admin@mydoamin.com" from "router@mydomain.com" subject "Login Succeeded" body "$_syslog_msg"
This code shows how to maintain a consistent configuration backup without extra work. This sends a mail with the configuration each time a write command is issued.
event manager applet ConfigChange-Write_Memory event cli pattern "write memory" sync no skip no action 1.0 cli command "enable" action 1.1 cli command "show run" action 2.0 mail server "<ip-adr-of-smtp-server>" to "admin@mydomain.dk" from "router@mydomain.com" subject "Running config dump" body "$_cli_result" event manager applet ConfigChange-wr event cli pattern "wr" sync no skip no action 1.0 cli command "enable" action 1.1 cli command "show run" action 2.0 mail server "<ip-adr-of-smtp-server>" to "admin@mydomain.com" from "router@mydomain.com" subject "Running config dump" body "$_cli_result"