Difference between revisions of "Iptables"
From Teknologisk videncenter
m (→Using IPTABLES) |
m (→IPTABLES firewall solutions) |
||
| Line 43: | Line 43: | ||
*Shorewall firewall [http://www.shorewall.net/ Shorewall.net 9 | *Shorewall firewall [http://www.shorewall.net/ Shorewall.net 9 | ||
[[Category:Linux]] | [[Category:Linux]] | ||
| + | == very basic Firewall == | ||
| + | Accepts only ping from inside to the outside. The machine is open to the Internet. | ||
| + | <pre> | ||
| + | #!/bin/bash | ||
| + | # | ||
| + | # Start firewall | ||
| + | # Diverse erklæringer | ||
| + | FW=iptables | ||
| + | INT_NET="192.168.54.0/24" | ||
| + | EXT_NET="172.16.0.0/16" | ||
| + | EXT_IP="172.16.4.4" | ||
| + | EXT_IF="eth0" | ||
| + | |||
| + | # Fjern alle tidligere regler | ||
| + | $FW –F | ||
| + | $FW -F -t nat | ||
| + | |||
| + | # Sæt default politik til afvisning | ||
| + | $FW –P FORWARD DROP | ||
| + | |||
| + | # Tillad ping indefra | ||
| + | $FW –A FORWARD –s $INT_NET –p icmp --icmp-type echo-request –j ACCEPT | ||
| + | |||
| + | # Tillad pong udefra | ||
| + | $FW –A FORWARD –d $INT_NET –p icmp --icmp-type echo-reply –j ACCEPT | ||
| + | |||
| + | # Source NAT på udgående pakker | ||
| + | $FW –A POSTROUTING –o $EXT_IF –s $INT_NET –j SNAT --to-source $EXT_IP | ||
| + | |||
| + | #Accept forwarding. Start routing | ||
| + | echo "1" > /proc/sys/net/ipv4/ip_forward | ||
| + | </pre> | ||
Revision as of 15:46, 7 March 2009
Contents
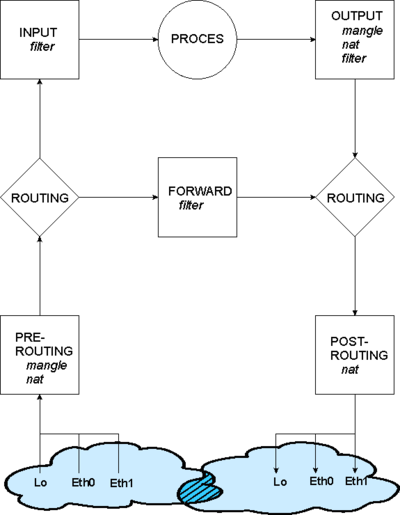
iptables is a packet filtering, NAT/PAT and packet mangling tool for Linux. Used by a variety of Linux distributions including Ubuntu, Redhat and CentOS. Iptables is highly configurable and are used in many firewall solutions.
Using IPTABLES
Iptables is a commandline command with numerous options, and need some training to master. There are three tables you can use filter(default) nat and mangle. Only filter and nat shown below.
The filter chains
Basically iptables has three filters/chains
- INPUT : Packets from a Interface to a local process on the machine. A packet from outside to the machine.
- FORWARD: Packets traversing from one Interface to another Interface
- OUTPUT : Packets from a local process - the machine itself - to the outside world.
See the tables with the command
[root@bkshost sysconfig]# iptables -L Chain INPUT (policy ACCEPT) target prot opt source destination Chain FORWARD (policy ACCEPT) target prot opt source destination Chain OUTPUT (policy ACCEPT) target prot opt source destination
The nat chains
When you use the nat table or mangle tables
- PREROUTING : Incoming packets before Routing decision. Used fx. for Destination nat
- POSTROUTING: Incoming packets after Routing decision. Used fx. for Source nat
- OUTPUT : Packets from a local process - the machine itself - to the outside world.
See the tables with the command
[root@bkshost sysconfig]# iptables -L -t nat Chain PREROUTING (policy ACCEPT) target prot opt source destination Chain POSTROUTING (policy ACCEPT) target prot opt source destination Chain OUTPUT (policy ACCEPT) target prot opt source destination
IPTABLES firewall solutions
- Shorewall firewall [http://www.shorewall.net/ Shorewall.net 9
very basic Firewall
Accepts only ping from inside to the outside. The machine is open to the Internet.
#!/bin/bash # # Start firewall # Diverse erklæringer FW=iptables INT_NET="192.168.54.0/24" EXT_NET="172.16.0.0/16" EXT_IP="172.16.4.4" EXT_IF="eth0" # Fjern alle tidligere regler $FW –F $FW -F -t nat # Sæt default politik til afvisning $FW –P FORWARD DROP # Tillad ping indefra $FW –A FORWARD –s $INT_NET –p icmp --icmp-type echo-request –j ACCEPT # Tillad pong udefra $FW –A FORWARD –d $INT_NET –p icmp --icmp-type echo-reply –j ACCEPT # Source NAT på udgående pakker $FW –A POSTROUTING –o $EXT_IF –s $INT_NET –j SNAT --to-source $EXT_IP #Accept forwarding. Start routing echo "1" > /proc/sys/net/ipv4/ip_forward