Difference between revisions of "Iptables"
m (→Complete firewall example) |
m |
||
| (16 intermediate revisions by 2 users not shown) | |||
| Line 1: | Line 1: | ||
__TOC__ | __TOC__ | ||
| + | '''NOTE:''' IP tables has been replaced with [[nftables]]. ([[iptables]] command converts into nft rulesets) | ||
[[iptables]] is a packet filtering, NAT/PAT and packet mangling tool for Linux. Used by a variety of Linux distributions including Ubuntu, Redhat and CentOS. Iptables is highly configurable and are used in many firewall solutions. | [[iptables]] is a packet filtering, NAT/PAT and packet mangling tool for Linux. Used by a variety of Linux distributions including Ubuntu, Redhat and CentOS. Iptables is highly configurable and are used in many firewall solutions. | ||
| − | * | + | *Se også [[NAT Linux]] og [[Ip linux command]] |
== Using IPTABLES == | == Using IPTABLES == | ||
Iptables is a commandline command with numerous options, and need some training to master. | Iptables is a commandline command with numerous options, and need some training to master. | ||
| Line 42: | Line 43: | ||
== IPTABLES firewall solutions == | == IPTABLES firewall solutions == | ||
| − | *Shorewall firewall [http://www.shorewall.net/ | + | *Shorewall firewall [http://www.shorewall.net/ |
[[Category:Linux]] | [[Category:Linux]] | ||
| + | |||
== iptables syntax == | == iptables syntax == | ||
<center>'''Format''': iptables ''<nowiki>[</nowiki>''-t'' tabel]'' ''kommando regel handling''</center> | <center>'''Format''': iptables ''<nowiki>[</nowiki>''-t'' tabel]'' ''kommando regel handling''</center> | ||
| Line 175: | Line 177: | ||
|} | |} | ||
| − | == | + | == Very basic firewall == |
Accepts only ping from inside to the outside. The machine is open to the Internet. Could be started in /etc/rc.local. | Accepts only ping from inside to the outside. The machine is open to the Internet. Could be started in /etc/rc.local. | ||
<pre> | <pre> | ||
| Line 188: | Line 190: | ||
EXT_IF="eth0" | EXT_IF="eth0" | ||
| − | # Fjern alle tidligere regler | + | # Fjern alle tidligere regler og ikke indbyggede kæder |
$FW –F | $FW –F | ||
$FW -F -t nat | $FW -F -t nat | ||
| + | $FW –X | ||
| + | $FW -X -t nat | ||
# Sæt default politik til afvisning | # Sæt default politik til afvisning | ||
| Line 208: | Line 212: | ||
</pre> | </pre> | ||
| − | == | + | == Basic firewall == |
iptables-save udskriver en liste over regler. Kommandoen | iptables-save udskriver en liste over regler. Kommandoen | ||
| Line 290: | Line 294: | ||
INT_IF="ens192" # Internal interface | INT_IF="ens192" # Internal interface | ||
| − | # Fjern alle tidligere regler | + | # Fjern alle tidligere regler og ikke indbyggede kæder |
| − | $FW | + | $FW –F |
$FW -F -t nat | $FW -F -t nat | ||
| + | $FW –X | ||
| + | $FW -X -t nat | ||
# Sæt default politik til afvisning | # Sæt default politik til afvisning | ||
| Line 325: | Line 331: | ||
</source> | </source> | ||
| − | ==Complete firewall | + | ==Complete firewall examples== |
| + | ===Using SNAT (Source NAT)=== | ||
<source lang=cli> | <source lang=cli> | ||
| Line 345: | Line 352: | ||
EXT_IF="ens160" # External interface | EXT_IF="ens160" # External interface | ||
INT_IF="ens192" # Internal interface | INT_IF="ens192" # Internal interface | ||
| − | + | # Fjern alle tidligere regler og ikke indbyggede kæder | |
| − | # Fjern alle tidligere regler | + | $FW –F |
| − | $FW | ||
$FW -F -t nat | $FW -F -t nat | ||
| − | + | $FW –X | |
| + | $FW -X -t nat | ||
# Sæt default politik til afvisning | # Sæt default politik til afvisning | ||
$FW -P FORWARD DROP | $FW -P FORWARD DROP | ||
#Accepting established and relatec TCP/UDP and ICMP connections | #Accepting established and relatec TCP/UDP and ICMP connections | ||
| + | ## Accept return traffic from inside users. | ||
$FW -A FORWARD -i $EXT_IF -o $INT_IF -m state --state ESTABLISHED,RELATED -j ACCEPT | $FW -A FORWARD -i $EXT_IF -o $INT_IF -m state --state ESTABLISHED,RELATED -j ACCEPT | ||
| + | ## Accept return traffic from insode servers (port forwarding) | ||
| + | $FW -A FORWARD -i $INT_IF -o $EXT_IF -m state --state ESTABLISHED,RELATED -j ACCEPT | ||
# Tillad ping indefra | # Tillad ping indefra | ||
| Line 365: | Line 375: | ||
$FW -t nat -A PREROUTING -p tcp -i $EXT_IF -d $EXT_IP --dport 8080 \ | $FW -t nat -A PREROUTING -p tcp -i $EXT_IF -d $EXT_IP --dport 8080 \ | ||
-j DNAT --to 192.168.1.2:80 | -j DNAT --to 192.168.1.2:80 | ||
| + | #Allow forwarded traffic through firewall | ||
$FW -A FORWARD -p tcp -i $EXT_IF -d 192.168.1.2 --dport 80 -j ACCEPT | $FW -A FORWARD -p tcp -i $EXT_IF -d 192.168.1.2 --dport 80 -j ACCEPT | ||
| − | |||
#Tillad DNS (udp port 53) | #Tillad DNS (udp port 53) | ||
| Line 379: | Line 389: | ||
echo "1" > /proc/sys/net/ipv4/ip_forward | echo "1" > /proc/sys/net/ipv4/ip_forward | ||
| + | |||
| + | </source> | ||
| + | |||
| + | ===Using Masqerading=== | ||
| + | Use masqerading when the external IP address is unknown. For example when using [[DHCP]]. | ||
| + | <source lang=cli> | ||
| + | #!/bin/bash | ||
| + | # | ||
| + | # Start firewall | ||
| + | # | ||
| + | # Tillader ping indefra og ud. | ||
| + | # Lukker for al anden trafik. | ||
| + | # | ||
| + | # OBS! Denne firewall rører udelukkende ved FORWARD | ||
| + | # | ||
| + | |||
| + | # Diverse erklæringer | ||
| + | FW=iptables | ||
| + | INT_NET="192.168.1.0/24" # Internal network behind firewall | ||
| + | EXT_IF="ens160" # External interface | ||
| + | INT_IF="ens192" # Internal interface | ||
| + | |||
| + | # Fjern alle tidligere regler og ikke indbyggede kæder | ||
| + | $FW –F | ||
| + | $FW -F -t nat | ||
| + | $FW –X | ||
| + | $FW -X -t nat | ||
| + | |||
| + | # Sæt default politik til afvisning | ||
| + | $FW -P FORWARD DROP | ||
| + | |||
| + | #Accepting established and relatec TCP/UDP and ICMP connections | ||
| + | ## Accept return traffic from inside users. | ||
| + | $FW -A FORWARD -i $EXT_IF -o $INT_IF -m state --state ESTABLISHED,RELATED -j ACCEPT | ||
| + | ## Accept return traffic from insode servers (port forwarding) | ||
| + | $FW -A FORWARD -i $INT_IF -o $EXT_IF -m state --state ESTABLISHED,RELATED -j ACCEPT | ||
| + | |||
| + | # Tillad ping indefra | ||
| + | $FW -A FORWARD -s $INT_NET -p icmp --icmp-type echo-request -j ACCEPT | ||
| + | |||
| + | iptables -t nat -A POSTROUTING -s $INT_NET -d 0.0.0.0/0 -o $EXT_IF -j MASQUERADE | ||
| + | #Forward port 8080 on $EXT_IP to internal webserver at 192.168.1.2 port 80 | ||
| + | iptables -t nat -A PREROUTING -p tcp -i $EXT_IF --dport 8080 -j DNAT --to-destination 192.168.1.2:80 | ||
| + | |||
| + | #Allow forwarded traffic through firewall | ||
| + | $FW -A FORWARD -p tcp -i $EXT_IF -d 192.168.1.2 --dport 80 -j ACCEPT | ||
| + | |||
| + | #Tillad DNS (udp port 53) | ||
| + | $FW -A FORWARD -p udp -o $EXT_IF --dport 53 -j ACCEPT | ||
| + | |||
| + | |||
| + | #TCP open ports | ||
| + | $FW -A FORWARD -i $INT_IF -p tcp --dport 80 -d 0.0.0.0/0 -j ACCEPT | ||
| + | $FW -A FORWARD -i $INT_IF -p tcp --dport 443 -d 0.0.0.0/0 -j ACCEPT | ||
| + | |||
| + | #Accept forwarding. Start routing | ||
| + | echo "1" > /proc/sys/net/ipv4/ip_forward | ||
</source> | </source> | ||
<!-- | <!-- | ||
| Line 404: | Line 471: | ||
= Links = | = Links = | ||
| + | *[https://netfilter.org/projects/nftables/ nft - iptables replacement] | ||
*[http://www.netfilter.org/documentation/index.html#documentation-howto Dokumentation] | *[http://www.netfilter.org/documentation/index.html#documentation-howto Dokumentation] | ||
== Software == | == Software == | ||
| Line 409: | Line 477: | ||
*[http://www.squid-cache.org/ squid] | *[http://www.squid-cache.org/ squid] | ||
*[http://www.webmin.com/ Webmin] | *[http://www.webmin.com/ Webmin] | ||
| − | [[Category:Linux]][[Category:DatateknikerV7]][[Category:Linux Command]] | + | [[Category:Linux]][[Category:DatateknikerV7]][[Category:Linux Command]][[category:Firewall]] |
Latest revision as of 12:38, 28 October 2023
Contents
NOTE: IP tables has been replaced with nftables. (iptables command converts into nft rulesets) iptables is a packet filtering, NAT/PAT and packet mangling tool for Linux. Used by a variety of Linux distributions including Ubuntu, Redhat and CentOS. Iptables is highly configurable and are used in many firewall solutions.
- Se også NAT Linux og Ip linux command
Using IPTABLES
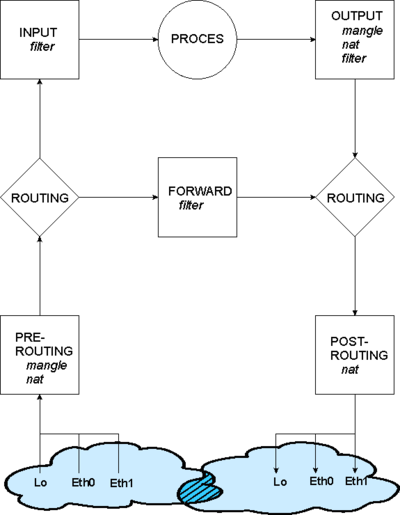
Iptables is a commandline command with numerous options, and need some training to master. There are three tables you can use filter(default) nat and mangle. Only filter and nat shown below.
The filter chains
Basically iptables has three filters/chains
- INPUT : Packets from a Interface to a local process on the machine. A packet from outside to the machine.
- FORWARD: Packets traversing from one Interface to another Interface
- OUTPUT : Packets from a local process - the machine itself - to the outside world.
See the tables with the command
[root@bkshost sysconfig]# iptables -L Chain INPUT (policy ACCEPT) target prot opt source destination Chain FORWARD (policy ACCEPT) target prot opt source destination Chain OUTPUT (policy ACCEPT) target prot opt source destination
The nat chains
When you use the nat table or mangle tables
- PREROUTING : Incoming packets before Routing decision. Used fx. for Destination nat
- POSTROUTING: Incoming packets after Routing decision. Used fx. for Source nat
- OUTPUT : Packets from a local process - the machine itself - to the outside world.
See the tables with the command
[root@bkshost sysconfig]# iptables -L -t nat Chain PREROUTING (policy ACCEPT) target prot opt source destination Chain POSTROUTING (policy ACCEPT) target prot opt source destination Chain OUTPUT (policy ACCEPT) target prot opt source destination
IPTABLES firewall solutions
- Shorewall firewall [http://www.shorewall.net/
iptables syntax
| Tabel | |
| filter | Regler, der bruges til at filtrere uønskede pakker fra.
Virker på INPUT, OUTPUT og FORWARD kæde |
| mangle | Regler, der bruges til at ændre i indholdet af pakker.
Virker på PREROUTING og OUTPUT kæde |
| nat | Regler, der bruges til at ændre adresser i pakker.
Viker på PREROUTING, OUTPUT og POSTROUTING kæde |
| Kommando | |
| -A kæde | Tilføj (append) for kæde |
| -I kæde [nummer] | Indsæt for kæde. Angives nummer ikke, antages 1 (dvs. først i tabellen) |
| -D kæde | Slet for kæde |
| -F [kæde] | Slet alle regler. Eventuelt i kæde |
| -P kæde politik | Sæt handling for kæde, hvis ingen regler findes. Politik er ACCEPT, DROP og RETURN |
| -L [kæde] | Vis en liste over regler, eventuelt for bestemt kæde |
| Regel | |
| -p [!]protokol | Match, hvis pakke bruger protokol. Protokol kan være tcp, udp, icmp eller andre |
| -s [!]adresse[/maske] | Match, hvis kilde adresse på pakke passer. Der kan angives en maske til et subnet (både 24 og 255.255.255.0 kan bruges) |
| -d [!]adresse[/maske] | Match, hvis destinatinsadresse på pakke passer. Der kan angives en maske til et subnet (både 24 og 255.255.255.0 kan bruges) |
| -i [!]interface | Match, hvis input interface er anvendt til at modtage pakken |
| -o [!]interface | Match, hvis output interface skal anvendes til at sende pakken |
| --sport [!] [port[:port]] | Match, hvis kildeport eller kildeport interval (f.eks. 22:80) anvendes i pakken. Bruges med tcp og udp (se -p regel) |
| --dport [!] [port[:port]] | Match, hvis destinationsport eller destinationsport interval (f.eks. 22:80) anvendes i pakken. Bruges med tcp og udp (se -p regel) |
| --icmp-type [!]typenavn | Match, hvis ICMP meddelelse er af typenavn, f.eks. echo-request, echo-reply, source-quench, time-exceeded, destination-unreachable, network-unreachable, host-unreachable, protocol-unreachable og port-unreachable. Bruges med icmp (se -p regel) |
| Bruges ! i ovenstående regler, virker match modsat. F.eks. vil -p !tcp matche alle pakker, der ikke bruger tcp. | |
| Handling | |
| -j ACCEPT | Accepter pakker, dvs. lad dem gå videre |
| -j DROP | Drop pakker, dvs. smid dem væk |
| -j SNAT --to-source adresse[:port] | Lav ændring i pakkens source IP, hvor adresse bliver den nye source IP og port den nye source port |
| -j DNAT
--to-destination adresse[:port] |
Lav ændring i pakkens destination IP, hvor adresse bliver den nye destination IP og port den nye destination port |
Very basic firewall
Accepts only ping from inside to the outside. The machine is open to the Internet. Could be started in /etc/rc.local.
#!/bin/bash # # Start firewall # Diverse erklæringer FW=iptables INT_NET="192.168.54.0/24" EXT_NET="172.16.0.0/16" EXT_IP="172.16.4.4" EXT_IF="eth0" # Fjern alle tidligere regler og ikke indbyggede kæder $FW –F $FW -F -t nat $FW –X $FW -X -t nat # Sæt default politik til afvisning $FW –P FORWARD DROP # Tillad ping indefra $FW –A FORWARD –s $INT_NET –p icmp --icmp-type echo-request –j ACCEPT # Tillad pong udefra $FW –A FORWARD –d $INT_NET –p icmp --icmp-type echo-reply –j ACCEPT # Source NAT på udgående pakker $FW -t nat –A POSTROUTING –o $EXT_IF –s $INT_NET –j SNAT --to-source $EXT_IP #Accept forwarding. Start routing echo "1" > /proc/sys/net/ipv4/ip_forward
Basic firewall
iptables-save udskriver en liste over regler. Kommandoen
iptables-save > /etc/sysconfig/iptables
Gør nuværende opsætning af iptables permanent dvs. den loades under opstart af iptables scriptet /etc/init.d/iptables.
Her er et eksempel på et simpelt firewall script, hvor der åbnet for ping fra det interne net og ud. Samtidig ændres alle interne IP til ekstern IP 172.16.4.4:
#!/bin/bash # # Start firewall # # Tillader ping indefra og ud. # Lukker for al anden trafik. # # OBS! Denne firewall rører udelukkende ved FORWARD # # Diverse erklæringer FW=iptables INT_NET="192.168.54.0/24" EXT_NET="172.16.0.0/16" EXT_IP="172.16.4.4" EXT_IF="eth0" # Fjern alle tidligere regler $FW –F # Sæt default politik til afvisning $FW –P FORWARD DROP # Tillad ping indefra $FW –A FORWARD –s $INT_NET –p icmp --icmp-type echo-request –j ACCEPT # Tillad pong udefra $FW –A FORWARD –d $INT_NET –p icmp --icmp-type echo-reply –j ACCEPT # Source NAT på udgående pakker $FW -t nat –A POSTROUTING –o $EXT_IF –s $INT_NET –j SNAT --to-source $EXT_IP
NAT Masqerading
Masqerading anvendes hvis det eksterne netkort får tildelt en IP adresse med DHCP.
# Enable IP Forwading between Interfaces (Routing)
echo "1" > /proc/sys/net/ipv4/ip_forward
# Allow the internal hosts to connect to any IP address on the outside 0.0.0.0/24
iptables -t nat -A POSTROUTING -s 172.20.0.0/24 -d 0.0.0.0/0 -o eth0 -j MASQUERADETCP
established
iptables -A FORWARD -i eth0 -o eth1 -m state --state ESTABLISHED,RELATED -j ACCEPT
Port forwarding
#!/bin/bash
#
# Start firewall
#
# Tillader ping indefra og ud.
# Port forwarder port 8080 til intern server port 80
# Lukker for al anden trafik.
#
# OBS! Denne firewall rører udelukkende ved FORWARD
#
# Diverse erklæringer
FW=iptables
INT_NET="192.168.1.0/24" # Internal network behind firewall
EXT_NET="192.168.138.0/24" # External public network
EXT_IP="192.168.138.250" # External public IP address
EXT_IF="ens160" # External interface
INT_IF="ens192" # Internal interface
# Fjern alle tidligere regler og ikke indbyggede kæder
$FW –F
$FW -F -t nat
$FW –X
$FW -X -t nat
# Sæt default politik til afvisning
$FW -P FORWARD DROP
# Tillad ping indefra
$FW -A FORWARD -s $INT_NET -p icmp --icmp-type echo-request -j ACCEPT
# Tillad pong udefra
$FW -A FORWARD -d $INT_NET -p icmp --icmp-type echo-reply -j ACCEPT
# Source NAT på udgående pakker
$FW -t nat -A POSTROUTING -o $EXT_IF -s $INT_NET -j SNAT --to-source $EXT_IP
#Accept forwarding. Start routing
echo "1" > /proc/sys/net/ipv4/ip_forward
#Forward port 8080 on $EXT_IP to internal webserver at 192.168.1.2 port 80
#Port forward i PREROUTING kæde
$FW -t nat -A PREROUTING -p tcp -i $EXT_IF -d $EXT_IP --dport 8080 \
-j DNAT --to 192.168.1.2:80
#Tillad trafik fra $EXT_IF til intern server til port 80
$FW -A FORWARD -p tcp -i $EXT_IF -d 192.168.1.2 --dport 80 -j ACCEPT
#Tillad returtrafik fra intern server fra port 80
$FW -A FORWARD -p tcp -i $INT_IF -d 0.0.0.0/0 -s 192.168.1.2 --sport 80 -j ACCEPT
#Tillad DNS (udp port 53)
iptables -A FORWARD -p udp -o ens160 --dport 53 -j ACCEPT
iptables -A FORWARD -p udp -i ens160 --sport 53 -j ACCEPT
Complete firewall examples
Using SNAT (Source NAT)
#!/bin/bash
#
# Start firewall
#
# Tillader ping indefra og ud.
# Lukker for al anden trafik.
#
# OBS! Denne firewall rører udelukkende ved FORWARD
#
# Diverse erklæringer
FW=iptables
INT_NET="192.168.1.0/24" # Internal network behind firewall
EXT_NET="192.168.138.0/24" # External public network
EXT_IP="192.168.138.250" # External public IP address
EXT_IF="ens160" # External interface
INT_IF="ens192" # Internal interface
# Fjern alle tidligere regler og ikke indbyggede kæder
$FW –F
$FW -F -t nat
$FW –X
$FW -X -t nat
# Sæt default politik til afvisning
$FW -P FORWARD DROP
#Accepting established and relatec TCP/UDP and ICMP connections
## Accept return traffic from inside users.
$FW -A FORWARD -i $EXT_IF -o $INT_IF -m state --state ESTABLISHED,RELATED -j ACCEPT
## Accept return traffic from insode servers (port forwarding)
$FW -A FORWARD -i $INT_IF -o $EXT_IF -m state --state ESTABLISHED,RELATED -j ACCEPT
# Tillad ping indefra
$FW -A FORWARD -s $INT_NET -p icmp --icmp-type echo-request -j ACCEPT
# Source NAT på udgående pakker
$FW -t nat -A POSTROUTING -o $EXT_IF -s $INT_NET -j SNAT --to-source $EXT_IP
#Forward port 8080 on $EXT_IP to internal webserver at 192.168.1.2 port 80
$FW -t nat -A PREROUTING -p tcp -i $EXT_IF -d $EXT_IP --dport 8080 \
-j DNAT --to 192.168.1.2:80
#Allow forwarded traffic through firewall
$FW -A FORWARD -p tcp -i $EXT_IF -d 192.168.1.2 --dport 80 -j ACCEPT
#Tillad DNS (udp port 53)
$FW -A FORWARD -p udp -o $EXT_IF --dport 53 -j ACCEPT
#TCP open ports
$FW -A FORWARD -i $INT_IF -p tcp --dport 80 -d 0.0.0.0/0 -j ACCEPT
$FW -A FORWARD -i $INT_IF -p tcp --dport 443 -d 0.0.0.0/0 -j ACCEPT
#Accept forwarding. Start routing
echo "1" > /proc/sys/net/ipv4/ip_forwardUsing Masqerading
Use masqerading when the external IP address is unknown. For example when using DHCP.
#!/bin/bash
#
# Start firewall
#
# Tillader ping indefra og ud.
# Lukker for al anden trafik.
#
# OBS! Denne firewall rører udelukkende ved FORWARD
#
# Diverse erklæringer
FW=iptables
INT_NET="192.168.1.0/24" # Internal network behind firewall
EXT_IF="ens160" # External interface
INT_IF="ens192" # Internal interface
# Fjern alle tidligere regler og ikke indbyggede kæder
$FW –F
$FW -F -t nat
$FW –X
$FW -X -t nat
# Sæt default politik til afvisning
$FW -P FORWARD DROP
#Accepting established and relatec TCP/UDP and ICMP connections
## Accept return traffic from inside users.
$FW -A FORWARD -i $EXT_IF -o $INT_IF -m state --state ESTABLISHED,RELATED -j ACCEPT
## Accept return traffic from insode servers (port forwarding)
$FW -A FORWARD -i $INT_IF -o $EXT_IF -m state --state ESTABLISHED,RELATED -j ACCEPT
# Tillad ping indefra
$FW -A FORWARD -s $INT_NET -p icmp --icmp-type echo-request -j ACCEPT
iptables -t nat -A POSTROUTING -s $INT_NET -d 0.0.0.0/0 -o $EXT_IF -j MASQUERADE
#Forward port 8080 on $EXT_IP to internal webserver at 192.168.1.2 port 80
iptables -t nat -A PREROUTING -p tcp -i $EXT_IF --dport 8080 -j DNAT --to-destination 192.168.1.2:80
#Allow forwarded traffic through firewall
$FW -A FORWARD -p tcp -i $EXT_IF -d 192.168.1.2 --dport 80 -j ACCEPT
#Tillad DNS (udp port 53)
$FW -A FORWARD -p udp -o $EXT_IF --dport 53 -j ACCEPT
#TCP open ports
$FW -A FORWARD -i $INT_IF -p tcp --dport 80 -d 0.0.0.0/0 -j ACCEPT
$FW -A FORWARD -i $INT_IF -p tcp --dport 443 -d 0.0.0.0/0 -j ACCEPT
#Accept forwarding. Start routing
echo "1" > /proc/sys/net/ipv4/ip_forward