Difference between revisions of "IPsec Cisco IOS"
From Teknologisk videncenter
m |
m |
||
| Line 3: | Line 3: | ||
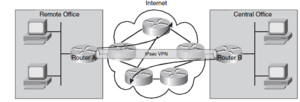
== Site-to-Site VPN == | == Site-to-Site VPN == | ||
[[Image:Site-to-Site IPsec tunnel.png|right|300px|thumb|Site-to-Site IPsec VPN]] | [[Image:Site-to-Site IPsec tunnel.png|right|300px|thumb|Site-to-Site IPsec VPN]] | ||
| + | === R1 config === | ||
| + | <source lang="cli"> | ||
| + | hostname R1 | ||
| + | ! | ||
| + | interface loopback 0 | ||
| + | ip address 172.16.1.1 255.255.255.0 | ||
| + | ! | ||
| + | router rip | ||
| + | version 2 | ||
| + | network 172.16.1.0 | ||
| + | ! | ||
| + | crypto isakmp enable | ||
| + | ! | ||
| + | crypto isakmp policy 10 | ||
| + | authentication pre-share | ||
| + | encryption aes 256 | ||
| + | hash sha | ||
| + | group 5 | ||
| + | lifetime 3600 | ||
| + | ! | ||
| + | crypto isakmp key cisco address 192.168.100.104 | ||
| + | ! | ||
| + | crypto ipsec transform-set 50 esp-aes 256 esp-sha-hmac ah-sha-hmac | ||
| + | exit | ||
| + | ! | ||
| + | crypto ipsec security-association lifetime seconds 1800 | ||
| + | ! | ||
| + | access-list 101 permit ip 172.16.1.0 0.0.0.255 172.16.3.0 0.0.0.255 | ||
| + | ! | ||
| + | crypto map MYMAP 10 ipsec-isakmp | ||
| + | match address 101 | ||
| + | set peer 192.168.100.104 | ||
| + | set pfs group5 | ||
| + | set transform-set 50 | ||
| + | set security-association lifetime seconds 900 | ||
| + | ! | ||
| + | interface fastethernet0/0 | ||
| + | crypto map MYMAP | ||
| + | </source> | ||
| + | |||
| + | === R2 Config === | ||
| + | <source lang="cli"> | ||
| + | hostname R2 | ||
| + | ! | ||
| + | interface loopback 0 | ||
| + | ip address 172.16.3.1 255.255.255.0 | ||
| + | ! | ||
| + | router rip | ||
| + | version 2 | ||
| + | network 172.16.3.0 | ||
| + | network 192.168.100.0 | ||
| + | ! | ||
| + | crypto isakmp enable | ||
| + | ! | ||
| + | crypto isakmp policy 10 | ||
| + | authentication pre-share | ||
| + | encryption aes 256 | ||
| + | hash sha | ||
| + | group 5 | ||
| + | lifetime 3600 | ||
| + | ! | ||
| + | crypto isakmp key cisco address 192.168.100.103 | ||
| + | ! | ||
| + | crypto ipsec transform-set 50 esp-aes 256 esp-sha-hmac ah-sha-hmac | ||
| + | exit | ||
| + | ! | ||
| + | crypto ipsec security-association lifetime seconds 1800 | ||
| + | ! | ||
| + | access-list 101 permit ip 172.16.3.0 0.0.0.255 172.16.1.0 0.0.0.255 | ||
| + | ! | ||
| + | crypto map MYMAP 10 ipsec-isakmp | ||
| + | match address 101 | ||
| + | set peer 192.168.100.103 | ||
| + | set pfs group5 | ||
| + | set transform-set 50 | ||
| + | set security-association lifetime seconds 900 | ||
| + | ! | ||
| + | interface fastethernet0/0 | ||
| + | crypto map MYMAP | ||
| + | </source> | ||
| + | === checking tunnel === | ||
| + | <source lang="cli"> | ||
| + | R1#<input>show crypto isakmp policy</input> | ||
| + | Global IKE policy | ||
| + | Protection suite of priority 10 | ||
| + | encryption algorithm: AES - Advanced Encryption Standard (256 bit keys). | ||
| + | hash algorithm: Secure Hash Standard | ||
| + | authentication method: Pre-Shared Key | ||
| + | Diffie-Hellman group: #5 (1536 bit) | ||
| + | lifetime: 3600 seconds, no volume limit | ||
| + | Default protection suite | ||
| + | encryption algorithm: DES - Data Encryption Standard (56 bit keys). | ||
| + | hash algorithm: Secure Hash Standard | ||
| + | authentication method: Rivest-Shamir-Adleman Signature | ||
| + | Diffie-Hellman group: #1 (768 bit) | ||
| + | lifetime: 86400 seconds, no volume limit | ||
| + | R1#<input>show crypto ipsec transform-set</input> | ||
| + | Transform set 50: { ah-sha-hmac } | ||
| + | will negotiate = { Tunnel, }, | ||
| + | { esp-256-aes esp-sha-hmac } | ||
| + | will negotiate = { Tunnel, }, | ||
| + | R1#show crypto map | ||
| + | Crypto Map "MYMAP" 10 ipsec-isakmp | ||
| + | Peer = 192.168.100.104 | ||
| + | Extended IP access list 101 | ||
| + | access-list 101 permit ip 172.16.1.0 0.0.0.255 172.16.3.0 0.0.0.255 | ||
| + | Current peer: 192.168.100.104 | ||
| + | Security association lifetime: 4608000 kilobytes/900 seconds | ||
| + | PFS (Y/N): Y | ||
| + | DH group: group5 | ||
| + | Transform sets={ | ||
| + | 50, | ||
| + | } | ||
| + | Interfaces using crypto map MYMAP: | ||
| + | FastEthernet0/0 | ||
| + | </source> | ||
Revision as of 05:40, 6 August 2009
Eksempler
Site-to-Site VPN
R1 config
hostname R1
!
interface loopback 0
ip address 172.16.1.1 255.255.255.0
!
router rip
version 2
network 172.16.1.0
!
crypto isakmp enable
!
crypto isakmp policy 10
authentication pre-share
encryption aes 256
hash sha
group 5
lifetime 3600
!
crypto isakmp key cisco address 192.168.100.104
!
crypto ipsec transform-set 50 esp-aes 256 esp-sha-hmac ah-sha-hmac
exit
!
crypto ipsec security-association lifetime seconds 1800
!
access-list 101 permit ip 172.16.1.0 0.0.0.255 172.16.3.0 0.0.0.255
!
crypto map MYMAP 10 ipsec-isakmp
match address 101
set peer 192.168.100.104
set pfs group5
set transform-set 50
set security-association lifetime seconds 900
!
interface fastethernet0/0
crypto map MYMAPR2 Config
hostname R2
!
interface loopback 0
ip address 172.16.3.1 255.255.255.0
!
router rip
version 2
network 172.16.3.0
network 192.168.100.0
!
crypto isakmp enable
!
crypto isakmp policy 10
authentication pre-share
encryption aes 256
hash sha
group 5
lifetime 3600
!
crypto isakmp key cisco address 192.168.100.103
!
crypto ipsec transform-set 50 esp-aes 256 esp-sha-hmac ah-sha-hmac
exit
!
crypto ipsec security-association lifetime seconds 1800
!
access-list 101 permit ip 172.16.3.0 0.0.0.255 172.16.1.0 0.0.0.255
!
crypto map MYMAP 10 ipsec-isakmp
match address 101
set peer 192.168.100.103
set pfs group5
set transform-set 50
set security-association lifetime seconds 900
!
interface fastethernet0/0
crypto map MYMAPchecking tunnel
R1#<input>show crypto isakmp policy</input>
Global IKE policy
Protection suite of priority 10
encryption algorithm: AES - Advanced Encryption Standard (256 bit keys).
hash algorithm: Secure Hash Standard
authentication method: Pre-Shared Key
Diffie-Hellman group: #5 (1536 bit)
lifetime: 3600 seconds, no volume limit
Default protection suite
encryption algorithm: DES - Data Encryption Standard (56 bit keys).
hash algorithm: Secure Hash Standard
authentication method: Rivest-Shamir-Adleman Signature
Diffie-Hellman group: #1 (768 bit)
lifetime: 86400 seconds, no volume limit
R1#<input>show crypto ipsec transform-set</input>
Transform set 50: { ah-sha-hmac }
will negotiate = { Tunnel, },
{ esp-256-aes esp-sha-hmac }
will negotiate = { Tunnel, },
R1#show crypto map
Crypto Map "MYMAP" 10 ipsec-isakmp
Peer = 192.168.100.104
Extended IP access list 101
access-list 101 permit ip 172.16.1.0 0.0.0.255 172.16.3.0 0.0.0.255
Current peer: 192.168.100.104
Security association lifetime: 4608000 kilobytes/900 seconds
PFS (Y/N): Y
DH group: group5
Transform sets={
50,
}
Interfaces using crypto map MYMAP:
FastEthernet0/0