Difference between revisions of "IPsec Cisco IOS"
From Teknologisk videncenter
m |
m |
||
| Line 119: | Line 119: | ||
FastEthernet0/0 | FastEthernet0/0 | ||
</source> | </source> | ||
| + | Sending some test packets from '''172.16.1.1''' to '''172.16.3.1''' | ||
| + | <source lang="cli"> | ||
| + | C1#<input>ping 172.16.3.1 source 172.16.1.1</input> | ||
| + | Sending 5, 100-byte ICMP Echos to 172.16.3.1, timeout is 2 seconds: | ||
| + | Packet sent with a source address of 172.16.1.1 | ||
| + | .!!!! | ||
| + | Success rate is 80 percent (4/5), round-trip min/avg/max = 1/2/4 ms | ||
| + | C1#show crypto ipsec sa | ||
| + | |||
| + | interface: FastEthernet0/0.1 | ||
| + | Crypto map tag: MYMAP, local addr 192.168.100.103 | ||
| + | |||
| + | protected vrf: (none) | ||
| + | local ident (addr/mask/prot/port): (172.16.1.0/255.255.255.0/0/0) | ||
| + | remote ident (addr/mask/prot/port): (172.16.3.0/255.255.255.0/0/0) | ||
| + | current_peer 192.168.100.104 port 500 | ||
| + | PERMIT, flags={origin_is_acl,ipsec_sa_request_sent} | ||
| + | <notice>#pkts encaps: 4, #pkts encrypt: 4, #pkts digest: 4 | ||
| + | #pkts decaps: 4, #pkts decrypt: 4, #pkts verify: 4</notice> | ||
| + | #pkts compressed: 0, #pkts decompressed: 0 | ||
| + | #pkts not compressed: 0, #pkts compr. failed: 0 | ||
| + | #pkts not decompressed: 0, #pkts decompress failed: 0 | ||
| + | #send errors 1, #recv errors 0 | ||
| + | |||
| + | local crypto endpt.: 192.168.100.103, remote crypto endpt.: 192.168.100.104 | ||
| + | path mtu 1500, ip mtu 1500, ip mtu idb FastEthernet0/0.1 | ||
| + | current outbound spi: 0x521B43F6(1377518582) | ||
| + | |||
| + | inbound esp sas: | ||
| + | spi: 0x92A7A6F8(2460460792) | ||
| + | transform: esp-256-aes esp-sha-hmac , | ||
| + | in use settings ={Tunnel, } | ||
| + | conn id: 2001, flow_id: FPGA:1, crypto map: MYMAP | ||
| + | sa timing: remaining key lifetime (k/sec): (4400183/893) | ||
| + | IV size: 16 bytes | ||
| + | replay detection support: Y | ||
| + | <notice>Status: ACTIVE</notice> | ||
| + | |||
| + | inbound ah sas: | ||
| + | spi: 0xFE07354B(4261885259) | ||
| + | transform: ah-sha-hmac , | ||
| + | in use settings ={Tunnel, } | ||
| + | conn id: 2001, flow_id: FPGA:1, crypto map: MYMAP | ||
| + | sa timing: remaining key lifetime (k/sec): (4400183/887) | ||
| + | replay detection support: Y | ||
| + | <notice>Status: ACTIVE</notice> | ||
| + | |||
| + | inbound pcp sas: | ||
| + | |||
| + | outbound esp sas: | ||
| + | spi: 0x521B43F6(1377518582) | ||
| + | transform: esp-256-aes esp-sha-hmac , | ||
| + | in use settings ={Tunnel, } | ||
| + | conn id: 2002, flow_id: FPGA:2, crypto map: MYMAP | ||
| + | sa timing: remaining key lifetime (k/sec): (4400183/887) | ||
| + | IV size: 16 bytes | ||
| + | replay detection support: Y | ||
| + | <notice>Status: ACTIVE</notice> | ||
| + | |||
| + | outbound ah sas: | ||
| + | spi: 0xB6D629E1(3067488737) | ||
| + | transform: ah-sha-hmac , | ||
| + | in use settings ={Tunnel, } | ||
| + | conn id: 2002, flow_id: FPGA:2, crypto map: MYMAP | ||
| + | sa timing: remaining key lifetime (k/sec): (4400183/886) | ||
| + | replay detection support: Y | ||
| + | <notice>Status: ACTIVE</notice> | ||
| + | |||
| + | outbound pcp sas: | ||
| + | </source> | ||
| + | {{#css: | ||
| + | pre { font-family: Lucida Console; font-weight: bold; font-size: 14px; color: #00FF00; background: black; margin: 10px 50px; width: 800px; line-height: 200%; overflow: auto;} | ||
| + | }} | ||
Revision as of 05:56, 6 August 2009
Eksempler
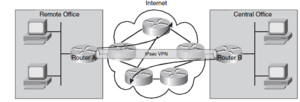
Site-to-Site VPN
R1 config
hostname R1
!
interface loopback 0
ip address 172.16.1.1 255.255.255.0
!
router rip
version 2
network 172.16.1.0
!
crypto isakmp enable
!
crypto isakmp policy 10
authentication pre-share
encryption aes 256
hash sha
group 5
lifetime 3600
!
crypto isakmp key cisco address 192.168.100.104
!
crypto ipsec transform-set 50 esp-aes 256 esp-sha-hmac ah-sha-hmac
exit
!
crypto ipsec security-association lifetime seconds 1800
!
access-list 101 permit ip 172.16.1.0 0.0.0.255 172.16.3.0 0.0.0.255
!
crypto map MYMAP 10 ipsec-isakmp
match address 101
set peer 192.168.100.104
set pfs group5
set transform-set 50
set security-association lifetime seconds 900
!
interface fastethernet0/0
crypto map MYMAPR2 Config
hostname R2
!
interface loopback 0
ip address 172.16.3.1 255.255.255.0
!
router rip
version 2
network 172.16.3.0
network 192.168.100.0
!
crypto isakmp enable
!
crypto isakmp policy 10
authentication pre-share
encryption aes 256
hash sha
group 5
lifetime 3600
!
crypto isakmp key cisco address 192.168.100.103
!
crypto ipsec transform-set 50 esp-aes 256 esp-sha-hmac ah-sha-hmac
exit
!
crypto ipsec security-association lifetime seconds 1800
!
access-list 101 permit ip 172.16.3.0 0.0.0.255 172.16.1.0 0.0.0.255
!
crypto map MYMAP 10 ipsec-isakmp
match address 101
set peer 192.168.100.103
set pfs group5
set transform-set 50
set security-association lifetime seconds 900
!
interface fastethernet0/0
crypto map MYMAPchecking tunnel
R1#<input>show crypto isakmp policy</input>
Global IKE policy
Protection suite of priority 10
encryption algorithm: AES - Advanced Encryption Standard (256 bit keys).
hash algorithm: Secure Hash Standard
authentication method: Pre-Shared Key
Diffie-Hellman group: #5 (1536 bit)
lifetime: 3600 seconds, no volume limit
Default protection suite
encryption algorithm: DES - Data Encryption Standard (56 bit keys).
hash algorithm: Secure Hash Standard
authentication method: Rivest-Shamir-Adleman Signature
Diffie-Hellman group: #1 (768 bit)
lifetime: 86400 seconds, no volume limit
R1#<input>show crypto ipsec transform-set</input>
Transform set 50: { ah-sha-hmac }
will negotiate = { Tunnel, },
{ esp-256-aes esp-sha-hmac }
will negotiate = { Tunnel, },
R1#show crypto map
Crypto Map "MYMAP" 10 ipsec-isakmp
Peer = 192.168.100.104
Extended IP access list 101
access-list 101 permit ip 172.16.1.0 0.0.0.255 172.16.3.0 0.0.0.255
Current peer: 192.168.100.104
Security association lifetime: 4608000 kilobytes/900 seconds
PFS (Y/N): Y
DH group: group5
Transform sets={
50,
}
Interfaces using crypto map MYMAP:
FastEthernet0/0Sending some test packets from 172.16.1.1 to 172.16.3.1
C1#<input>ping 172.16.3.1 source 172.16.1.1</input>
Sending 5, 100-byte ICMP Echos to 172.16.3.1, timeout is 2 seconds:
Packet sent with a source address of 172.16.1.1
.!!!!
Success rate is 80 percent (4/5), round-trip min/avg/max = 1/2/4 ms
C1#show crypto ipsec sa
interface: FastEthernet0/0.1
Crypto map tag: MYMAP, local addr 192.168.100.103
protected vrf: (none)
local ident (addr/mask/prot/port): (172.16.1.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (172.16.3.0/255.255.255.0/0/0)
current_peer 192.168.100.104 port 500
PERMIT, flags={origin_is_acl,ipsec_sa_request_sent}
<notice>#pkts encaps: 4, #pkts encrypt: 4, #pkts digest: 4
#pkts decaps: 4, #pkts decrypt: 4, #pkts verify: 4</notice>
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 1, #recv errors 0
local crypto endpt.: 192.168.100.103, remote crypto endpt.: 192.168.100.104
path mtu 1500, ip mtu 1500, ip mtu idb FastEthernet0/0.1
current outbound spi: 0x521B43F6(1377518582)
inbound esp sas:
spi: 0x92A7A6F8(2460460792)
transform: esp-256-aes esp-sha-hmac ,
in use settings ={Tunnel, }
conn id: 2001, flow_id: FPGA:1, crypto map: MYMAP
sa timing: remaining key lifetime (k/sec): (4400183/893)
IV size: 16 bytes
replay detection support: Y
<notice>Status: ACTIVE</notice>
inbound ah sas:
spi: 0xFE07354B(4261885259)
transform: ah-sha-hmac ,
in use settings ={Tunnel, }
conn id: 2001, flow_id: FPGA:1, crypto map: MYMAP
sa timing: remaining key lifetime (k/sec): (4400183/887)
replay detection support: Y
<notice>Status: ACTIVE</notice>
inbound pcp sas:
outbound esp sas:
spi: 0x521B43F6(1377518582)
transform: esp-256-aes esp-sha-hmac ,
in use settings ={Tunnel, }
conn id: 2002, flow_id: FPGA:2, crypto map: MYMAP
sa timing: remaining key lifetime (k/sec): (4400183/887)
IV size: 16 bytes
replay detection support: Y
<notice>Status: ACTIVE</notice>
outbound ah sas:
spi: 0xB6D629E1(3067488737)
transform: ah-sha-hmac ,
in use settings ={Tunnel, }
conn id: 2002, flow_id: FPGA:2, crypto map: MYMAP
sa timing: remaining key lifetime (k/sec): (4400183/886)
replay detection support: Y
<notice>Status: ACTIVE</notice>
outbound pcp sas: