Difference between revisions of "NAT Linux"
m (→When you have a floating address on the external Interface) |
m (→WEB server on the inside network) |
||
| (11 intermediate revisions by the same user not shown) | |||
| Line 1: | Line 1: | ||
| − | + | {{TOCright}} | |
| − | + | [[iptables]] is used for packet filtering and NAT/PAT translation on several Linux distributions including | |
*Ubunto | *Ubunto | ||
*Redhat | *Redhat | ||
*Centos | *Centos | ||
| − | == Basic NAT example using | + | == Basic NAT example using iptables == |
| − | + | [[iptables]] can be configured in two different ways when you boot your machine. The examples will assume you have two Network interface cards. '''eth0''' connected to the internal - private network - and '''eth1''' connected to the external - Internet. | |
*Using a startup script. Example below. | *Using a startup script. Example below. | ||
| − | *Using | + | *Using [[iptables]] save and restore facelity. Example below. |
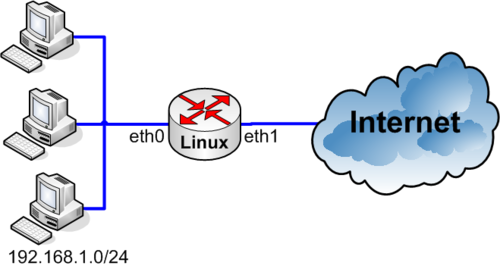
| − | === Using a startup script to configure | + | [[Image:Linux_nat_1.png|none|500px|thumb|Example network]] |
| + | === Using a startup script to configure iptables === | ||
==== When you have a fixed address on the external Interface ==== | ==== When you have a fixed address on the external Interface ==== | ||
When you know your address on the external Interface - not using DHCP - you should use source NAT (SNAT), which is slightly more efficient than using masquerading.<br> | When you know your address on the external Interface - not using DHCP - you should use source NAT (SNAT), which is slightly more efficient than using masquerading.<br> | ||
| Line 18: | Line 19: | ||
# Allow the internal hosts to connect to any IP address on the outside 0.0.0.0/24 | # Allow the internal hosts to connect to any IP address on the outside 0.0.0.0/24 | ||
iptables -t nat -A POSTROUTING -s 192.168.1.0/24 -d 0.0.0.0/0 -j SNAT --to 83.90.47.30 | iptables -t nat -A POSTROUTING -s 192.168.1.0/24 -d 0.0.0.0/0 -j SNAT --to 83.90.47.30 | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
</pre> | </pre> | ||
==== When you have a floating address on the external Interface ==== | ==== When you have a floating address on the external Interface ==== | ||
| Line 36: | Line 24: | ||
Add the following lines to '''/etc/rc.local''' | Add the following lines to '''/etc/rc.local''' | ||
<pre> | <pre> | ||
| − | # Enable IP | + | # Enable IP Forwarding between Interfaces (Routing) |
echo "1" > /proc/sys/net/ipv4/ip_forward | echo "1" > /proc/sys/net/ipv4/ip_forward | ||
# Use iptables Source NAT (SNAT) to translate internal 192.168.1.0/24 IP addresses to the external IP Address that eth0 has | # Use iptables Source NAT (SNAT) to translate internal 192.168.1.0/24 IP addresses to the external IP Address that eth0 has | ||
| Line 42: | Line 30: | ||
iptables -t nat -A POSTROUTING -s 192.168.1.0/24 -d 0.0.0.0/0 -o eth1 -j MASQUERADE | iptables -t nat -A POSTROUTING -s 192.168.1.0/24 -d 0.0.0.0/0 -o eth1 -j MASQUERADE | ||
</pre> | </pre> | ||
| − | use the command ''iptables -L -t nat'' to see the | + | |
| + | === Checking iptables NAT rules and traffic === | ||
| + | The [[iptables]] list option can be used to see [[iptables]] rules and [[iptables]] traffic. | ||
| + | |||
| + | use the command ''iptables -L -t nat'' to see the rules in the [[iptables]] NAT chains. | ||
<pre> | <pre> | ||
[root@bkshost etc]# iptables -L -t nat | [root@bkshost etc]# iptables -L -t nat | ||
| Line 55: | Line 47: | ||
target prot opt source destination | target prot opt source destination | ||
</pre> | </pre> | ||
| − | + | use the command ''iptables -L -t nat '''-v''''' to see the rules in the [[iptables]] chains and the traffic for each rule. | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
<pre> | <pre> | ||
| − | + | [root@bkshost etc]# iptables -L -t nat -v | |
| − | + | Chain PREROUTING (policy ACCEPT 275K packets, 19M bytes) | |
| − | + | pkts bytes target prot opt in out source destination | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | + | Chain POSTROUTING (policy ACCEPT 13846 packets, 1355K bytes) | |
| − | + | pkts bytes target prot opt in out source destination | |
| + | 99447 6447K MASQUERADE all -- * eth1 172.22.0.0/24 0.0.0.0/0 | ||
| − | + | Chain OUTPUT (policy ACCEPT 15307 packets, 1758K bytes) | |
| − | + | pkts bytes target prot opt in out source destination | |
</pre> | </pre> | ||
| − | + | === WEB server on the inside network === | |
| + | If you have a WEB server on the inside network for example 192.168.1.30, which should be accessible from the outside. (eth1) | ||
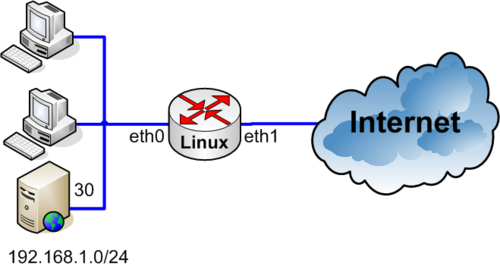
| + | [[Image:Linux_nat_2.png|none|500px|thumb|Example network]] | ||
<pre> | <pre> | ||
| − | + | iptables -A PREROUTING -t nat -i eth1 -p tcp --dport 80 -j DNAT --to 192.168.1.30:80 | |
| − | + | iptables -A PREROUTING -t nat -i eth1 -p tcp --dport 443 -j DNAT --to 192.168.1.30:443 | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
</pre> | </pre> | ||
| − | === | + | ==IP destination nat Forwarding with source nat== |
| − | |||
<pre> | <pre> | ||
| + | iptables -t nat -A PREROUTING -i eth1 -d 83.90.239.187 -j DNAT --to 192.168.139.103 | ||
| + | iptables -t nat -A POSTROUTING -o eth0 -d 192.168.139.103 -j SNAT --to-source 172.16.4.17 | ||
| + | </pre> | ||
[[Category:Linux]] | [[Category:Linux]] | ||
Latest revision as of 15:25, 11 December 2013
iptables is used for packet filtering and NAT/PAT translation on several Linux distributions including
- Ubunto
- Redhat
- Centos
Basic NAT example using iptables
iptables can be configured in two different ways when you boot your machine. The examples will assume you have two Network interface cards. eth0 connected to the internal - private network - and eth1 connected to the external - Internet.
- Using a startup script. Example below.
- Using iptables save and restore facelity. Example below.
Using a startup script to configure iptables
When you have a fixed address on the external Interface
When you know your address on the external Interface - not using DHCP - you should use source NAT (SNAT), which is slightly more efficient than using masquerading.
Add the following lines to /etc/rc.local
# Enable IP Forwading between Interfaces (Routing) echo "1" > /proc/sys/net/ipv4/ip_forward # Use iptables Source NAT (SNAT) to translate internal 192.168.1.0/24 IP addresses to the external IP Address 83.90.47.30 # Allow the internal hosts to connect to any IP address on the outside 0.0.0.0/24 iptables -t nat -A POSTROUTING -s 192.168.1.0/24 -d 0.0.0.0/0 -j SNAT --to 83.90.47.30
When you have a floating address on the external Interface
When you don't know your external IP Address and are fetching it from a DHCP server, you can use masquerading
Add the following lines to /etc/rc.local
# Enable IP Forwarding between Interfaces (Routing) echo "1" > /proc/sys/net/ipv4/ip_forward # Use iptables Source NAT (SNAT) to translate internal 192.168.1.0/24 IP addresses to the external IP Address that eth0 has # Allow the internal hosts to connect to any IP address on the outside 0.0.0.0/24 iptables -t nat -A POSTROUTING -s 192.168.1.0/24 -d 0.0.0.0/0 -o eth1 -j MASQUERADE
Checking iptables NAT rules and traffic
The iptables list option can be used to see iptables rules and iptables traffic.
use the command iptables -L -t nat to see the rules in the iptables NAT chains.
[root@bkshost etc]# iptables -L -t nat Chain PREROUTING (policy ACCEPT) target prot opt source destination Chain POSTROUTING (policy ACCEPT) target prot opt source destination MASQUERADE all -- 192.168.1.0/24 anywhere Chain OUTPUT (policy ACCEPT) target prot opt source destination
use the command iptables -L -t nat -v to see the rules in the iptables chains and the traffic for each rule.
[root@bkshost etc]# iptables -L -t nat -v Chain PREROUTING (policy ACCEPT 275K packets, 19M bytes) pkts bytes target prot opt in out source destination Chain POSTROUTING (policy ACCEPT 13846 packets, 1355K bytes) pkts bytes target prot opt in out source destination 99447 6447K MASQUERADE all -- * eth1 172.22.0.0/24 0.0.0.0/0 Chain OUTPUT (policy ACCEPT 15307 packets, 1758K bytes) pkts bytes target prot opt in out source destination
WEB server on the inside network
If you have a WEB server on the inside network for example 192.168.1.30, which should be accessible from the outside. (eth1)
iptables -A PREROUTING -t nat -i eth1 -p tcp --dport 80 -j DNAT --to 192.168.1.30:80 iptables -A PREROUTING -t nat -i eth1 -p tcp --dport 443 -j DNAT --to 192.168.1.30:443
IP destination nat Forwarding with source nat
iptables -t nat -A PREROUTING -i eth1 -d 83.90.239.187 -j DNAT --to 192.168.139.103 iptables -t nat -A POSTROUTING -o eth0 -d 192.168.139.103 -j SNAT --to-source 172.16.4.17