Difference between revisions of "IPv6 Firewall Cisco IOS ACL based"
From Teknologisk videncenter
m (removed Category:IPv6 using HotCat) |
m (added Category:IPv6 Security using HotCat) |
||
| (One intermediate revision by the same user not shown) | |||
| Line 140: | Line 140: | ||
</source> | </source> | ||
| − | |||
[[Category:Firewall]] | [[Category:Firewall]] | ||
| + | [[Category:IPv6 Security]] | ||
Latest revision as of 11:41, 21 May 2014
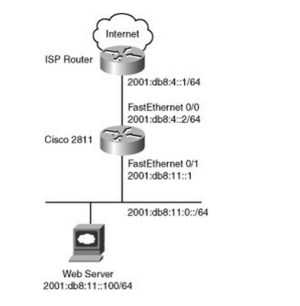
IPv6 firewall example using access lists.
Contents
Access-lists as firewall
One of the fundamental problems with ACLs is the fact that they do not maintain state information about the traffic flows. ACLs do not observe what host on which interface initiated the conversation or which end of the conversation is the client and which end is the server. Standard ACLs do not have any concept of TCP SYN, SYN ACK, ACK, or FIN flags and their influence on a TCP establishment and connection. Therefore, ACLs tend to be less granular than policies that are configured on a fully stateful packet-filtering firewall. ACLs might be fast but they are not extremely precise.
Internet inbound trafic
ipv6 access-list Internet-Inbound
remark Deny loopback address
deny ipv6 ::1/128 any
remark Deny IPv4-compatible addresses
deny ipv6 0::/96 any
remark Deny IPv4-mapped addresses (obsolete)
deny ipv6 ::ffff:0.0.0.0/96 any
remark Deny auto tunneled packets w/compatible addresses (RFC 4291)
deny ipv6 ::0.0.0.0/96 any
remark Deny other compatible addresses
deny ipv6 ::224.0.0.0/100 any log
deny ipv6 ::127.0.0.0/104 any log
deny ipv6 ::0.0.0.0/104 any log
deny ipv6 ::255.0.0.0/104 any log
remark Deny false 6to4 packets
deny ipv6 2002:e000::/20 any log
deny ipv6 2002:7f00::/24 any log
deny ipv6 2002:0000::/24 any log
deny ipv6 2002:ff00::/24 any log
deny ipv6 2002:0a00::/24 any log
deny ipv6 2002:ac10::/28 any log
deny ipv6 2002:c0a8::/32 any log
remark Permit good NDP messages since we deny and log at the end
permit icmp fe80::/10 any nd-na
permit icmp fe80::/10 any nd-ns
remark Deny Link-Local communications
deny ipv6 fe80::/10 any
remark Deny Site-Local (deprecated)
deny ipv6 fec0::/10 any
remark Deny Unique-Local packets
deny ipv6 fc00::/7 any
remark Deny multicast packets
deny ipv6 ff00::/8 any
remark Deny Documentation Address
deny ipv6 2001:db8::/32 any
remark Deny 6Bone addresses (deprecated)
deny ipv6 3ffe::/16 any
remark Deny RH0 packets
deny ipv6 any any routing-type 0 log
remark Deny our own addresses coming inbound
deny ipv6 2001:db8:11::/48 any log
remark permit BGP to and from our EBGP neighbor
permit tcp host 2001:db8:4::1 host 2001:db8:4::2 eq bgp
permit tcp host 2001:db8:4::1 eq bgp host 2001:db8:4::2
remark Permit traffic to our web server
permit tcp any host 2001:db8:11::100 eq www
remark Permit our returned traffic from internal clients
permit tcp any 2001:db8:11::/48 range 1024 65535
permit udp any 2001:db8:11::/48 range 1024 65535
remark Permit inbound DNS responses to our internal caching DNS server
permit udp any eq domain host 2001:db8:11:30:20c:29ff:fe5d:982a
remark Permit good ICMPv6 message types
permit icmp any 2001:db8:11::/48 destination-unreachable
permit icmp any 2001:db8:11::/48 packet-too-big
permit icmp any 2001:db8:11::/48 time-exceeded
permit icmp any 2001:db8:11::/48 parameter-problem
permit icmp any 2001:db8:11::/48 echo-reply
remark Permit our ISP to ping our external interface
permit icmp host 2001:db8:4::1 host 2001:db8:4::2 echo-request
remark Deny everything else and log it
deny ipv6 any any logInternet outbound trafic
ipv6 access-list Internet-Outbound
remark Deny loopback address
deny ipv6 any ::1/128
remark Deny IPv4-compatible addresses
deny ipv6 any 0::/96
remark Deny IPv4-mapped addresses (obsolete)
deny ipv6 any ::ffff:0.0.0.0/96
remark Deny auto tunneled packets w/compatible addresses (RFC 4291)
deny ipv6 any ::0.0.0.0/96
remark Deny other compatible addresses
deny ipv6 any ::224.0.0.0/100 log
deny ipv6 any ::127.0.0.0/104 log
deny ipv6 any ::0.0.0.0/104 log
deny ipv6 any ::255.0.0.0/104 log
remark Deny false 6to4 packets
deny ipv6 any 2002:e000::/20 log
deny ipv6 any 2002:7f00::/24 log
deny ipv6 any 2002:0000::/24 log
deny ipv6 any 2002:ff00::/24 log
deny ipv6 any 2002:0a00::/24 log
deny ipv6 any 2002:ac10::/28 log
deny ipv6 any 2002:c0a8::/32 log
remark Permit good NDP messages since we deny and log at the end
permit icmp fe80::/10 any nd-na
permit icmp fe80::/10 any nd-ns
remark Deny Link-Local communications
deny ipv6 any fe80::/10
remark Deny Site-Local (deprecated)
deny ipv6 any fec0::/10
remark Deny Unique-Local packets
deny ipv6 any fc00::/7
remark Deny multicast packets
deny ipv6 any ff00::/8
remark Deny Documentation Address
deny ipv6 any 2001:db8::/32
remark Deny 6Bone addresses (deprecated)
deny ipv6 any 3ffe::/16
remark Deny RH0 packets
deny ipv6 any any routing-type 0 log
remark Permit outbound DNS requests from our internal caching DNS server
permit udp host 2001:db8:11:30:20c:29ff:fe5d:982a any eq domain
remark Permit good ICMPv6 message types
permit icmp 2001:db8:11::/48 any destination-unreachable
permit icmp 2001:db8:11::/48 any packet-too-big
permit icmp 2001:db8:11::/48 any time-exceeded
permit icmp 2001:db8:11::/48 any parameter-problem
permit icmp 2001:db8:11::/48 any echo-reply
remark Permit our own addresses going outbound
permit ipv6 2001:db8:11::/48 any
remark Deny everything else and log it
deny ipv6 any any logApplying the access lists
interface FastEthernet 0/0
description Link to IPv6 Internet
ipv6 address 2001:db8:4::2/64
ipv6 nd dad attempts 0
ipv6 traffic-filter Internet-Inbound in
interface FastEthernet 0/1
description Link to internal IPv6 network
ipv6 address 2001:db8:11::1/64
ipv6 nd dad attempts 0
ipv6 traffic-filter Internet-Outbound in