Difference between revisions of "IPsec Cisco IOS"
m (→IPsec Site-to-Site configuration steps) |
m (→GETVPN) |
||
| (29 intermediate revisions by 2 users not shown) | |||
| Line 1: | Line 1: | ||
| − | [[Category:CCNP]][[Category:CCNP2]][[Category:CCDP]] | + | [[Category:CCNP]][[Category:CCNP2]][[Category:CCDP]][[Category:Security]] |
| − | = IPsec | + | For [[IPv6]] IPsec information see [[IPsec IPv6 Cisco IOS]] |
| + | = IPsec Possibilities = | ||
* IPsec—Internet Protocol Security (IPsec) is a suite of protocols that can provide data confidentiality, data integrity, and data origin authentication to IP packets. | * IPsec—Internet Protocol Security (IPsec) is a suite of protocols that can provide data confidentiality, data integrity, and data origin authentication to IP packets. | ||
* Internet Key Exchange (IKE)—A framework used to exchange security parameters and authentication keys between IPsec endpoints. | * Internet Key Exchange (IKE)—A framework used to exchange security parameters and authentication keys between IPsec endpoints. | ||
| Line 12: | Line 13: | ||
Together, these three protocols offer the various IPsec features mentioned earlier. Every IPsec VPN uses some combination of these protocols to provide the desired features for the VPN. | Together, these three protocols offer the various IPsec features mentioned earlier. Every IPsec VPN uses some combination of these protocols to provide the desired features for the VPN. | ||
=== IKE === | === IKE === | ||
| − | Internet Key Exchange (IKE) is a framework for the negotiation and exchange of security parameters and authentication keys. The IPsec security parameters will be examined later in the “Internet Key Exchange (IKE)” section. For now, it is important to understand that there are a variety of possible options between two IPsec VPN endpoints. The secure negotiation of these parameters used to establish the IPsec VPN characteristics is performed by IKE. IKE also exchanges keys used for the symmetrical encryption algorithms within an IPsec VPN. Compared to other encryption algorithms, symmetrical algorithms tend to be more efficient and easier to implement in hardware. The use of such algorithms requires appropriate key material, and IKE provides the mechanism to exchange the keys. | + | Internet Key Exchange (IKE) is a framework for the negotiation and exchange of security parameters and authentication keys. The IPsec security parameters will be examined later in the “Internet Key Exchange (IKE)” section. For now, it is important to understand that there are a variety of possible options between two IPsec VPN endpoints. The secure negotiation of these parameters used to establish the IPsec VPN characteristics is performed by IKE. IKE also exchanges keys used for the symmetrical encryption algorithms within an IPsec VPN. Compared to other encryption algorithms, symmetrical algorithms tend to be more efficient and easier to implement in hardware. The use of such algorithms requires appropriate key material, and IKE provides the mechanism to exchange the keys.<br/> |
| + | This section describes the Internet Key Exchange protocol which is also called the Internet Security Association and Key Management Protocol.<ref>http://www.cisco.com/c/en/us/td/docs/security/asa/asa70/configuration/guide/config/ike.html#wp1060317</ref> | ||
| + | |||
=== ESP === | === ESP === | ||
Encapsulating Security Payload (ESP) provides the framework for the data confidentiality, data integrity, data origin authentication, and optional anti-replay features of IPsec. While ESP is the only IPsec protocol that provides data encryption, it also can provide all of the IPsec features mentioned earlier. Because of this, ESP is primarily used in IPsec VPNs today. The following encryption methods are available to IPsec ESP: | Encapsulating Security Payload (ESP) provides the framework for the data confidentiality, data integrity, data origin authentication, and optional anti-replay features of IPsec. While ESP is the only IPsec protocol that provides data encryption, it also can provide all of the IPsec features mentioned earlier. Because of this, ESP is primarily used in IPsec VPNs today. The following encryption methods are available to IPsec ESP: | ||
| Line 30: | Line 33: | ||
|- | |- | ||
|} | |} | ||
| + | ;HMAC | ||
| + | :hash-based message authentication code. It may be used to simultaneously verify both the data integrity and the authentication of a message | ||
| + | |||
Both MD5 and SHA-1 use a shared secret key for both the calculation and verification of the message authentication values. The cryptographic strength of the HMAC is dependent upon the properties of the underlying hash function. Both MD5 and SHA-1 take variable-length input data and create a fixed-length hash. The difference is the size and strength of the hash created. Although IPsec uses only the first 96 bits of the 160-bit SHA-1 hash, it is considered more secure than MD5 (although SHA-1 is computationally slower than MD5). | Both MD5 and SHA-1 use a shared secret key for both the calculation and verification of the message authentication values. The cryptographic strength of the HMAC is dependent upon the properties of the underlying hash function. Both MD5 and SHA-1 take variable-length input data and create a fixed-length hash. The difference is the size and strength of the hash created. Although IPsec uses only the first 96 bits of the 160-bit SHA-1 hash, it is considered more secure than MD5 (although SHA-1 is computationally slower than MD5). | ||
| + | |||
== IPsec operation == | == IPsec operation == | ||
#Interesting traffic discovered (ACL list) | #Interesting traffic discovered (ACL list) | ||
| Line 46: | Line 53: | ||
group 5 | group 5 | ||
lifetime 3600 | lifetime 3600 | ||
| + | ! | ||
| + | crypto isakmp key cisco address 80.1.2.3 | ||
</source> | </source> | ||
* 2: Configure the IPsec transform set (IKE phase 2 and tunnel termination) | * 2: Configure the IPsec transform set (IKE phase 2 and tunnel termination) | ||
| Line 89: | Line 98: | ||
{| | {| | ||
|valign="top"| | |valign="top"| | ||
| − | *Cisco eksempel [[ | + | *Cisco eksempel [[Media:IP sec site-to-site cli.pdf|IPsec Site-to-Site using CLI]] (Loads PDF) |
| − | *Cisco eksempel [[ | + | *Cisco eksempel [[Media:IP sec site-to-site sdm.pdf|IPsec Site-to-Site using SDM]] (Loads PDF) |
| − | Before configuring IPsec make sure you can ping between the Routers.You must be able to ping the two endpoints of the tunnel. In the example below | + | Before configuring IPsec make sure you can ping between the Routers.You must be able to ping the two endpoints of the tunnel. In the example below Router-A endpoint is 192.168.100.103 on fastethernet 0/0 and Router-B endpoint is 192.168.100.104 on fastethernet 0/0. The configuration Tunnels all trafic between 172.16.1.0/24 on Router-A and 172.16.3.0/24 on Router-B. |
|- | |- | ||
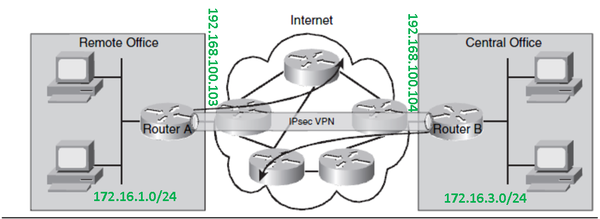
| − | |[[Image: | + | |[[Image:Tegning1.png|left|600px|thumb|Picture 1: Site-to-Site IPsec VPN]] |
|} | |} | ||
=== R1 config === | === R1 config === | ||
| Line 284: | Line 293: | ||
outbound pcp sas: | outbound pcp sas: | ||
</source> | </source> | ||
| − | + | ||
| − | + | == Site-to-Site VPN with dynamic IP address in remote site== | |
| − | }} | + | ===HQ IOS Router=== |
| + | When using NAT remember to '''deny''' permitted traffic in the tunnel in the nat access-list. | ||
| + | <source lang=cli> | ||
| + | crypto isakmp policy 1 | ||
| + | encr 3des | ||
| + | hash md5 | ||
| + | authentication pre-share | ||
| + | group 2 | ||
| + | lifetime 86400 | ||
| + | ! | ||
| + | crypto isakmp key SECRETPW address 0.0.0.0 0.0.0.0 | ||
| + | ! | ||
| + | ip access-list extended VPN1-TRAFFIC | ||
| + | permit ip 10.10.10.0 0.0.0.255 20.20.20.0 0.0.0.255 | ||
| + | ! | ||
| + | crypto ipsec transform-set TS esp-3des esp-md5-hmac | ||
| + | ! | ||
| + | crypto map VPN 1 ipsec-isakmp dynamic HQ-VPN | ||
| + | ! | ||
| + | crypto dynamic-map HQ-VPN 10 | ||
| + | set security-association lifetime seconds 86400 | ||
| + | set transform-set TS | ||
| + | match address VPN1-TRAFFIC | ||
| + | ! | ||
| + | interface FastEthernet0/1 | ||
| + | description Internet | ||
| + | ip address 74.200.90.5 255.255.255.0 | ||
| + | crypto map VPN | ||
| + | ! | ||
| + | interface FastEthernet0/2 | ||
| + | description Secure inside network | ||
| + | ip address 10.10.10.1 | ||
| + | </source> | ||
| + | |||
| + | ===Remote site=== | ||
| + | <source lang=cli> | ||
| + | crypto isakmp policy 1 | ||
| + | encr 3des | ||
| + | hash md5 | ||
| + | authentication pre-share | ||
| + | group 2 | ||
| + | lifetime 86400 | ||
| + | ! | ||
| + | crypto isakmp key SECRETPW address 74.200.90.5 | ||
| + | ! | ||
| + | ip access-list extended VPN-TRAFFIC | ||
| + | permit ip 20.20.20.0 0.0.0.255 10.10.10.0 0.0.0.255 | ||
| + | ! | ||
| + | crypto ipsec transform-set TS esp-3des esp-md5-hmac | ||
| + | ! | ||
| + | crypto map VPN2HQ 10 ipsec-isakmp | ||
| + | set peer 74.200.90.5 | ||
| + | set transform-set TS | ||
| + | match address VPN-TRAFFIC | ||
| + | ! | ||
| + | interface FastEthernet0/1 | ||
| + | description Interface to internet | ||
| + | ip address dhcp | ||
| + | crypto map VPN2HQ | ||
| + | ! | ||
| + | interface FastEthernet0/2 | ||
| + | description Secure inside network | ||
| + | ip address 20.20.20.1 | ||
| + | </source> | ||
| + | ==Using NAT on tunnel source Interface== | ||
| + | When using NAT on the Tunnel interface, remember to ''deny'' tunnel destination network in the NAT access list as [[NAT Cisco IOS|NAT]] is performed before crypto map is checked. See [[Understand the order of operations for Cisco IOS]] | ||
| + | =Configuring more than one IPsec tunnel= | ||
| + | <source lang=cli> | ||
| + | crypto keyring site-1-keyring | ||
| + | pre-shared-key address 1.1.1.1 key abcd | ||
| + | pre-shared-key address 2.2.2.2 key abcd | ||
| + | crypto keyring site-2-keyring | ||
| + | pre-shared-key address 3.3.3.3 key abcd | ||
| + | ! | ||
| + | crypto isakmp policy 1 | ||
| + | encr 3des | ||
| + | authentication pre-share | ||
| + | group 2 | ||
| + | crypto isakmp profile site-1-a-prof | ||
| + | keyring site-1-keyring | ||
| + | match identity address 1.1.1.1 255.255.255.255 | ||
| + | crypto isakmp profile site-1-b-prof | ||
| + | keyring site-1-keyring | ||
| + | match identity address 2.2.2.2 255.255.255.255 | ||
| + | crypto isakmp profile site-2-prof | ||
| + | keyring site-2-keyring | ||
| + | match identity address 3.3.3.3 255.255.255.255 | ||
| + | ! | ||
| + | ! | ||
| + | crypto ipsec transform-set strong ah-sha-hmac esp-3des | ||
| + | ! | ||
| + | crypto map ipsec-maps 10 ipsec-isakmp | ||
| + | description ** Site 1 VPN A ** | ||
| + | set peer 1.1.1.1 | ||
| + | set transform-set strong | ||
| + | set isakmp-profile site-1-a-prof | ||
| + | match address site-1-a-acl | ||
| + | crypto map ipsec-maps 20 ipsec-isakmp | ||
| + | description ** Site 1 VPN B ** | ||
| + | set peer 2.2.2.2 | ||
| + | set transform-set strong | ||
| + | set isakmp-profile site-1-b-prof | ||
| + | match address site-1-b-acl | ||
| + | crypto map ipsec-maps 30 ipsec-isakmp | ||
| + | description ** Site 2 ** | ||
| + | set peer 3.3.3.3 | ||
| + | set transform-set strong | ||
| + | set isakmp-profile site-2-prof | ||
| + | match address site-2-acl | ||
| + | ! | ||
| + | interface Dialer1 | ||
| + | crypto map ipsec-maps | ||
| + | ! | ||
| + | ip access-list extended site-1-a-acl | ||
| + | permit ip 192.168.0.0 0.0.0.255 192.168.1.0 0.0.0.255 | ||
| + | ip access-list extended site-1-b-acl | ||
| + | permit ip 192.168.0.0 0.0.0.255 192.168.2.0 0.0.0.255 | ||
| + | ip access-list extended site-2-acl | ||
| + | permit ip 192.168.0.0 0.0.0.255 192.168.3.0 0.0.0.255 | ||
| + | </source> | ||
| + | ===Links=== | ||
| + | *[http://www.firewall.cx/cisco-technical-knowledgebase/cisco-routers/936-cisco-router-vpn-dynamic-endpoint.html CONFIGURING CISCO SITE TO SITE IPSEC VPN WITH DYNAMIC IP ENDPOINT CISCO ROUTERS] | ||
| + | *[http://www.mustbegeek.com/configure-site-to-site-ipsec-vpn-tunnel-in-cisco-ios-router/ configure site-to-site ipsec vpn-tunnel] | ||
| + | ====GETVPN==== | ||
| + | Group Encrypted Transport VPN - | ||
| + | *[https://www.cisco.com/c/dam/en/us/products/collateral/security/group-encrypted-transport-vpn/GETVPN_DIG_version_2_0_External.pdf Cisco Group Encrypted Transport VPN (GETVPN) Design and Implementation Guide] | ||
| + | ====WireGuard==== | ||
| + | *[https://www.wireguard.com/ WireGuard homepage] | ||
| + | |||
| + | ===References=== | ||
| + | <references/> | ||
| + | {{Source cli}} | ||
Latest revision as of 07:23, 10 March 2021
For IPv6 IPsec information see IPsec IPv6 Cisco IOS
IPsec Possibilities
- IPsec—Internet Protocol Security (IPsec) is a suite of protocols that can provide data confidentiality, data integrity, and data origin authentication to IP packets.
- Internet Key Exchange (IKE)—A framework used to exchange security parameters and authentication keys between IPsec endpoints.
- Encryption Algorithms—Mathematical algorithms (and the associated keys) used to make data unreadable to everyone except those who have the proper keying material.
- Public Key Infrastructure—A hierarchical framework for managing the security attributes for devices that engage in secure communications across a network.
IPsec protokoller
IPsec consists of three primary protocols to help implement the overall IPsec architecture:
- Internet Key Exchange (IKE)
- Encapsulating Security Payload (ESP)
- Authentication Header (AH)
Together, these three protocols offer the various IPsec features mentioned earlier. Every IPsec VPN uses some combination of these protocols to provide the desired features for the VPN.
IKE
Internet Key Exchange (IKE) is a framework for the negotiation and exchange of security parameters and authentication keys. The IPsec security parameters will be examined later in the “Internet Key Exchange (IKE)” section. For now, it is important to understand that there are a variety of possible options between two IPsec VPN endpoints. The secure negotiation of these parameters used to establish the IPsec VPN characteristics is performed by IKE. IKE also exchanges keys used for the symmetrical encryption algorithms within an IPsec VPN. Compared to other encryption algorithms, symmetrical algorithms tend to be more efficient and easier to implement in hardware. The use of such algorithms requires appropriate key material, and IKE provides the mechanism to exchange the keys.
This section describes the Internet Key Exchange protocol which is also called the Internet Security Association and Key Management Protocol.[1]
ESP
Encapsulating Security Payload (ESP) provides the framework for the data confidentiality, data integrity, data origin authentication, and optional anti-replay features of IPsec. While ESP is the only IPsec protocol that provides data encryption, it also can provide all of the IPsec features mentioned earlier. Because of this, ESP is primarily used in IPsec VPNs today. The following encryption methods are available to IPsec ESP:
- Data Encryption Standard (DES)—An older method of encrypting information that has enjoyed widespread use.
- Triple Data Encryption Standard (3DES)—A block cipher that uses DES three times.
- Advanced Encryption Standard (AES)—One of the most popular symmetric key algorithms used today.
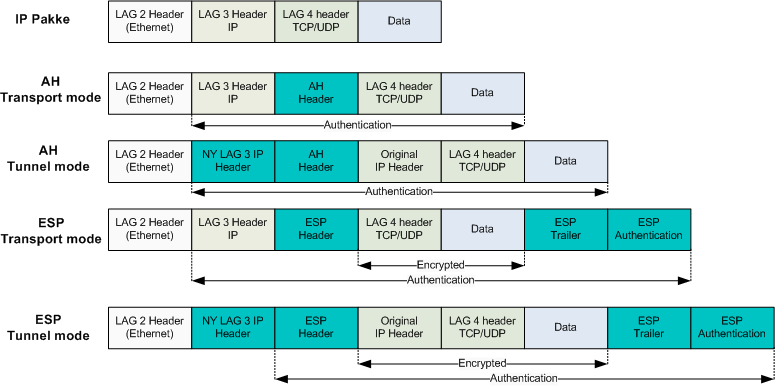
AH
Authentication Header (AH) provides the framework for the data integrity, data origin authentication, and optional anti-replay features of IPsec. Note that data confidentiality is not provided by AH. AH ensures that the data has not been modified or tampered with, but does not hide the data from inquisitive eyes during transit. As such, the use of AH alone in today’s networks has faded in favor of ESP. Both AH and ESP use a Hash-based Message Authentication Code (HMAC) as the authentication and integrity check. Table below shows the HMAC hash algorithms in IPsec.
| Hash Algorithm | input | Output | User by IPsec |
|---|---|---|---|
| Message Digest 5(MD5) | Variable | 128 bits | 128 bits |
| Secure hash Algorithm (SHA-1) | Variable | 160 bits | First 96 bits |
- HMAC
- hash-based message authentication code. It may be used to simultaneously verify both the data integrity and the authentication of a message
Both MD5 and SHA-1 use a shared secret key for both the calculation and verification of the message authentication values. The cryptographic strength of the HMAC is dependent upon the properties of the underlying hash function. Both MD5 and SHA-1 take variable-length input data and create a fixed-length hash. The difference is the size and strength of the hash created. Although IPsec uses only the first 96 bits of the 160-bit SHA-1 hash, it is considered more secure than MD5 (although SHA-1 is computationally slower than MD5).
IPsec operation
- Interesting traffic discovered (ACL list)
- IKE phase 1 (Security negotiation and establish secure communication channel)
- IKE phase 2 (Establishing the tunnel negotiate IPsec transform set and establish and maintain tunnel)
- Secure data transfer (IKE phase 2 renegoitiate keys at intervals)
- Tunnel termination
IPsec Site-to-Site configuration steps
- 1:Configure ISAKMP policy (IKE phase 1)
crypto isakmp policy 10
authentication pre-share
encryption aes 256
hash sha
group 5
lifetime 3600
!
crypto isakmp key cisco address 80.1.2.3- 2: Configure the IPsec transform set (IKE phase 2 and tunnel termination)
crypto ipsec transform-set 50 esp-aes 256 esp-sha-hmac ah-sha-hmac
exit- 3: Configure Crypto ACL (Specifying interesting traffic which go through the secure channel)
access-list 101 permit ip 172.16.1.0 0.0.0.255 172.16.3.0 0.0.0.255- 4: Configure the Crypto map (IKE phase 2)
crypto map MYMAP 10 ipsec-isakmp
match address 101
set peer 80.1.2.3
set transform-set 50
set security-association lifetime seconds 900- 5: Apply the crypto map to the interface (IKE phase 2)
interface fastethernet0/0
ip address 90.2.3.4 255.255.255.0
crypto map MYMAP- 6: Configure the interface ACL. Permit IPsec to go through (Not necessary if everything open).
access-list 110 permit ahp host 80.1.2.3 host 90.2.3.4
access-list 110 permit esp host 80.1.2.3 host 90.2.3.4
access-list 110 permit udp host 80.1.2.3 host 90.2.3.4 eq isakmp
!
interface fastethernet0/0
ip access-group 110 inIPsec modes
Eksempler
Site-to-Site VPN
Before configuring IPsec make sure you can ping between the Routers.You must be able to ping the two endpoints of the tunnel. In the example below Router-A endpoint is 192.168.100.103 on fastethernet 0/0 and Router-B endpoint is 192.168.100.104 on fastethernet 0/0. The configuration Tunnels all trafic between 172.16.1.0/24 on Router-A and 172.16.3.0/24 on Router-B. |
R1 config
hostname R1
!
interface loopback 0
ip address 172.16.1.1 255.255.255.0
!
router rip
version 2
network 172.16.1.0
!
crypto isakmp enable
!
crypto isakmp policy 10
authentication pre-share
encryption aes 256
hash sha
group 5
lifetime 3600
!
crypto isakmp key cisco address 192.168.100.104
!
crypto ipsec transform-set 50 esp-aes 256 esp-sha-hmac ah-sha-hmac
exit
!
crypto ipsec security-association lifetime seconds 1800
!
access-list 101 permit ip 172.16.1.0 0.0.0.255 172.16.3.0 0.0.0.255
!
crypto map MYMAP 10 ipsec-isakmp
match address 101
set peer 192.168.100.104
set pfs group5
set transform-set 50
set security-association lifetime seconds 900
!
interface fastethernet0/0
ip address 192.168.100.103 255.255.255.0
crypto map MYMAPR2 Config
hostname R2
!
interface loopback 0
ip address 172.16.3.1 255.255.255.0
!
router rip
version 2
network 172.16.3.0
network 192.168.100.0
!
crypto isakmp enable
!
crypto isakmp policy 10
authentication pre-share
encryption aes 256
hash sha
group 5
lifetime 3600
!
crypto isakmp key cisco address 192.168.100.103
!
crypto ipsec transform-set 50 esp-aes 256 esp-sha-hmac ah-sha-hmac
exit
!
crypto ipsec security-association lifetime seconds 1800
!
access-list 101 permit ip 172.16.3.0 0.0.0.255 172.16.1.0 0.0.0.255
!
crypto map MYMAP 10 ipsec-isakmp
match address 101
set peer 192.168.100.103
set pfs group5
set transform-set 50
set security-association lifetime seconds 900
!
interface fastethernet0/0
ip address 192.168.100.104 255.255.255.0
crypto map MYMAPchecking tunnel
R1#<input>show crypto isakmp policy</input>
Global IKE policy
Protection suite of priority 10
encryption algorithm: AES - Advanced Encryption Standard (256 bit keys).
hash algorithm: Secure Hash Standard
authentication method: Pre-Shared Key
Diffie-Hellman group: #5 (1536 bit)
lifetime: 3600 seconds, no volume limit
Default protection suite
encryption algorithm: DES - Data Encryption Standard (56 bit keys).
hash algorithm: Secure Hash Standard
authentication method: Rivest-Shamir-Adleman Signature
Diffie-Hellman group: #1 (768 bit)
lifetime: 86400 seconds, no volume limit
R1#<input>show crypto ipsec transform-set</input>
Transform set 50: { ah-sha-hmac }
will negotiate = { Tunnel, },
{ esp-256-aes esp-sha-hmac }
will negotiate = { Tunnel, },
R1#show crypto map
Crypto Map "MYMAP" 10 ipsec-isakmp
Peer = 192.168.100.104
Extended IP access list 101
access-list 101 permit ip 172.16.1.0 0.0.0.255 172.16.3.0 0.0.0.255
Current peer: 192.168.100.104
Security association lifetime: 4608000 kilobytes/900 seconds
PFS (Y/N): Y
DH group: group5
Transform sets={
50,
}
Interfaces using crypto map MYMAP:
FastEthernet0/0Sending some test packets from 172.16.1.1 to 172.16.3.1
C1#<input>ping 172.16.3.1 source 172.16.1.1</input>
Sending 5, 100-byte ICMP Echos to 172.16.3.1, timeout is 2 seconds:
Packet sent with a source address of 172.16.1.1
.!!!!
Success rate is 80 percent (4/5), round-trip min/avg/max = 1/2/4 ms
C1#<input>show crypto ipsec sa</input>
interface: FastEthernet0/0.1
Crypto map tag: MYMAP, local addr 192.168.100.103
protected vrf: (none)
local ident (addr/mask/prot/port): (172.16.1.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (172.16.3.0/255.255.255.0/0/0)
current_peer 192.168.100.104 port 500
PERMIT, flags={origin_is_acl,ipsec_sa_request_sent}
<notice>#pkts encaps: 4, #pkts encrypt: 4, #pkts digest: 4
#pkts decaps: 4, #pkts decrypt: 4, #pkts verify: 4</notice>
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 1, #recv errors 0
local crypto endpt.: 192.168.100.103, remote crypto endpt.: 192.168.100.104
path mtu 1500, ip mtu 1500, ip mtu idb FastEthernet0/0.1
current outbound spi: 0x521B43F6(1377518582)
inbound esp sas:
spi: 0x92A7A6F8(2460460792)
transform: esp-256-aes esp-sha-hmac ,
in use settings ={Tunnel, }
conn id: 2001, flow_id: FPGA:1, crypto map: MYMAP
sa timing: remaining key lifetime (k/sec): (4400183/893)
IV size: 16 bytes
replay detection support: Y
<notice>Status: ACTIVE</notice>
inbound ah sas:
spi: 0xFE07354B(4261885259)
transform: ah-sha-hmac ,
in use settings ={Tunnel, }
conn id: 2001, flow_id: FPGA:1, crypto map: MYMAP
sa timing: remaining key lifetime (k/sec): (4400183/887)
replay detection support: Y
<notice>Status: ACTIVE</notice>
inbound pcp sas:
outbound esp sas:
spi: 0x521B43F6(1377518582)
transform: esp-256-aes esp-sha-hmac ,
in use settings ={Tunnel, }
conn id: 2002, flow_id: FPGA:2, crypto map: MYMAP
sa timing: remaining key lifetime (k/sec): (4400183/887)
IV size: 16 bytes
replay detection support: Y
<notice>Status: ACTIVE</notice>
outbound ah sas:
spi: 0xB6D629E1(3067488737)
transform: ah-sha-hmac ,
in use settings ={Tunnel, }
conn id: 2002, flow_id: FPGA:2, crypto map: MYMAP
sa timing: remaining key lifetime (k/sec): (4400183/886)
replay detection support: Y
<notice>Status: ACTIVE</notice>
outbound pcp sas:Site-to-Site VPN with dynamic IP address in remote site
HQ IOS Router
When using NAT remember to deny permitted traffic in the tunnel in the nat access-list.
crypto isakmp policy 1
encr 3des
hash md5
authentication pre-share
group 2
lifetime 86400
!
crypto isakmp key SECRETPW address 0.0.0.0 0.0.0.0
!
ip access-list extended VPN1-TRAFFIC
permit ip 10.10.10.0 0.0.0.255 20.20.20.0 0.0.0.255
!
crypto ipsec transform-set TS esp-3des esp-md5-hmac
!
crypto map VPN 1 ipsec-isakmp dynamic HQ-VPN
!
crypto dynamic-map HQ-VPN 10
set security-association lifetime seconds 86400
set transform-set TS
match address VPN1-TRAFFIC
!
interface FastEthernet0/1
description Internet
ip address 74.200.90.5 255.255.255.0
crypto map VPN
!
interface FastEthernet0/2
description Secure inside network
ip address 10.10.10.1Remote site
crypto isakmp policy 1
encr 3des
hash md5
authentication pre-share
group 2
lifetime 86400
!
crypto isakmp key SECRETPW address 74.200.90.5
!
ip access-list extended VPN-TRAFFIC
permit ip 20.20.20.0 0.0.0.255 10.10.10.0 0.0.0.255
!
crypto ipsec transform-set TS esp-3des esp-md5-hmac
!
crypto map VPN2HQ 10 ipsec-isakmp
set peer 74.200.90.5
set transform-set TS
match address VPN-TRAFFIC
!
interface FastEthernet0/1
description Interface to internet
ip address dhcp
crypto map VPN2HQ
!
interface FastEthernet0/2
description Secure inside network
ip address 20.20.20.1Using NAT on tunnel source Interface
When using NAT on the Tunnel interface, remember to deny tunnel destination network in the NAT access list as NAT is performed before crypto map is checked. See Understand the order of operations for Cisco IOS
Configuring more than one IPsec tunnel
crypto keyring site-1-keyring
pre-shared-key address 1.1.1.1 key abcd
pre-shared-key address 2.2.2.2 key abcd
crypto keyring site-2-keyring
pre-shared-key address 3.3.3.3 key abcd
!
crypto isakmp policy 1
encr 3des
authentication pre-share
group 2
crypto isakmp profile site-1-a-prof
keyring site-1-keyring
match identity address 1.1.1.1 255.255.255.255
crypto isakmp profile site-1-b-prof
keyring site-1-keyring
match identity address 2.2.2.2 255.255.255.255
crypto isakmp profile site-2-prof
keyring site-2-keyring
match identity address 3.3.3.3 255.255.255.255
!
!
crypto ipsec transform-set strong ah-sha-hmac esp-3des
!
crypto map ipsec-maps 10 ipsec-isakmp
description ** Site 1 VPN A **
set peer 1.1.1.1
set transform-set strong
set isakmp-profile site-1-a-prof
match address site-1-a-acl
crypto map ipsec-maps 20 ipsec-isakmp
description ** Site 1 VPN B **
set peer 2.2.2.2
set transform-set strong
set isakmp-profile site-1-b-prof
match address site-1-b-acl
crypto map ipsec-maps 30 ipsec-isakmp
description ** Site 2 **
set peer 3.3.3.3
set transform-set strong
set isakmp-profile site-2-prof
match address site-2-acl
!
interface Dialer1
crypto map ipsec-maps
!
ip access-list extended site-1-a-acl
permit ip 192.168.0.0 0.0.0.255 192.168.1.0 0.0.0.255
ip access-list extended site-1-b-acl
permit ip 192.168.0.0 0.0.0.255 192.168.2.0 0.0.0.255
ip access-list extended site-2-acl
permit ip 192.168.0.0 0.0.0.255 192.168.3.0 0.0.0.255Links
- CONFIGURING CISCO SITE TO SITE IPSEC VPN WITH DYNAMIC IP ENDPOINT CISCO ROUTERS
- configure site-to-site ipsec vpn-tunnel
GETVPN
Group Encrypted Transport VPN -