Introduction to Network Maintenance
understanding Maintenance Mode
Introducing network maintenance
- Hardware and software installation and configuration.
- Troubleshooting problem reports.
- Monitoring and tuning network performance.
- Planning for network expansion.
- Documenting the network and any changes made to the network.
- Ensuring compliance with legal regulations and corporate policies.
- Securing the network against internal and external threats.
Proactive Versus Reactive Network Maintenance
- Structured tasks: Performed as a predefined plan.
- Interrupt driven tasks: Involve resolving issues as they are reported.
Well Known Network Maintenance Models
Maintenance models
| Model |
Explanation
|
| FCAPS |
Fault-, Configuration-, Accounting-, Performance- and Security management
|
| defined by ISO
|
| ITIL |
IT Infrastructure Library
|
| Defines a collection of best-practice recommendations that work together to meet business goals.
|
| TMN |
Telecommunications Management Network
|
| ITU-T variation of FCAPS - See above - specially targeted towards Tele Communication Networks
|
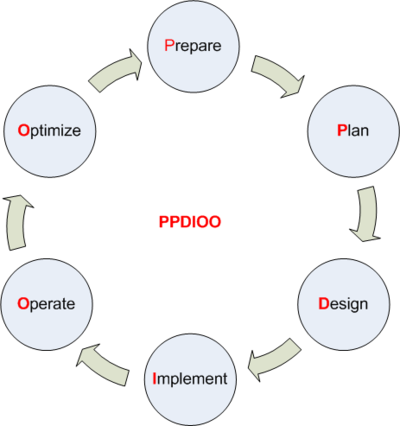
| PPDIOO |
Also called Cisco Lifecycle Services (See drawing below
|
FCAPS
FCAPS examples
| Type of Management |
Examples of tasks
|
| Fault Management
|
Use network management software to collect information from routers and switches.
|
| Send an E-mail alert when CPU utilization exceeds 80 percent.
|
| respond to incoming trouble tickets from the help desk.
|
| Configuration management
|
Require logging of any changes to hardware or software configurations.
|
| Implement a change management system to alert relevant personal.
|
| Accounting management
|
Invoice IP telephony users for their long distance and international calls
|
| Performance management
|
Monitor network performance for both LAN and WAN links
|
| Deploy QoS to utilize limited WAN bandwidth.
|
| Security management
|
Deploy firewall, VPN and IPS technologies
|
| Create a security policy dictating acceptable network use
|
| Use AAA server to validate user credentials
|
| Assign appropriate user privileges
|
| Log user activity
|
!
ip ftp username hotbu
ip ftp password F8iJk
!
archive
path ftp://192.168.2.33/R1-config
write-memory
time-period 1440