Difference between revisions of "Netband Project"
(→Equipment list) |
m (→Course description) |
||
| (79 intermediate revisions by 3 users not shown) | |||
| Line 1: | Line 1: | ||
| − | + | The main goal of this project is to design, implement and test some of the many security functionalities in Cisco IOS. | |
| − | |||
| − | |||
| + | __TOC__ | ||
| − | + | == Course description == | |
| + | |||
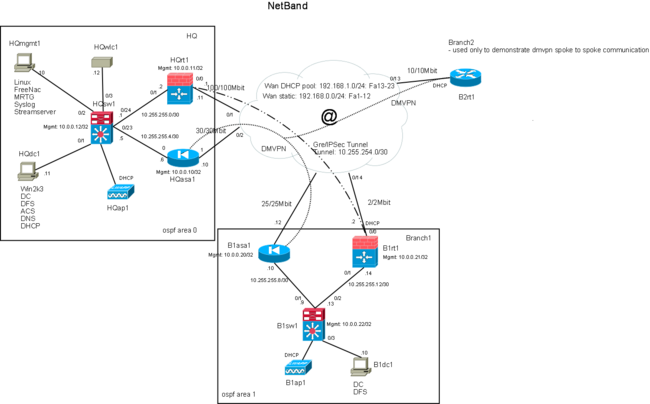
| + | A small company setup is used to illustrate and document the various relevant security features on an network infrastructure. The bussiness case evolves around a small to medium sized company with a centralized HQ and a number of remote branch offices. The project will consist mainly of cisco switches, routers and Asa firewall appliances. In order to support and demonstrate selected features, a small number of linux and windows servers are installed. The servers are just used as support so only basic configuration and security are implemented. | ||
| + | |||
| + | <br> | ||
| + | |||
| + | [[Image:Valgfag.png|thumb|none|650px|Network diagram]] | ||
| + | |||
| + | <br> | ||
| + | |||
| + | The project will touch on the following areas: | ||
| + | |||
| + | *[[DMVPN]] | ||
| + | *[[Netband Project - WLC | WLC]] | ||
| + | *[[Netband_Project_-_IPSec/Gre|IPSec vpn]] | ||
| + | *[[Asa firewall]] | ||
| + | *[[Netband_Project_-_Zone_based_Firewall(ZFW)|Zone based firewall]] | ||
| + | *[[Netband Project - IOS firewall | IOS firewall]] | ||
| + | *[[Netband Project - IOS ips |IOS ips]] | ||
| + | *[[Netband Project - DHCP Snooping | DHCP snooping]] | ||
| + | *[[Netband Project - Dynamic Arp Inspection | Dynamic Arp Inspection]] | ||
| + | *[[Netband Project - IP Source Guard | IP Source Guard]] | ||
| + | *[[Netband Project - SNMPv3 | SNMPv3]] | ||
| + | *[[Netband_Project_-_Embedded_Event_Manager_%28EEM%29|Embedded event manager ]] | ||
| + | *[[Netband Project - 802.1x | 802.1x]] | ||
| + | *[[VMPS]] | ||
| + | *[[Netband Project - CoPP | CoPP]] | ||
| + | *[[Netband Project - Private Vlan|Private vlans]] | ||
| + | *[[Netband Project - Multicast|Multicast]] | ||
| + | *[[Netband_Project_-_Device_hardening|Device hardening]] | ||
| + | *[[Netband Project - Syslog|Syslog]] | ||
| + | *[[Netband_Project_-_Windows_server#DHCP|DHCP]] | ||
| + | *[[Netband_Project_-_Windows_server#DFS|DFS]] | ||
| + | *[[Netband_Project_-_Windows_server#Active_Domain|AD]] | ||
| + | *[[Netband_Project_-_Goodies|Goodies]] | ||
| + | *[[Network access control]] | ||
| + | |||
| + | == Ip addresses == | ||
| − | + | HQ | |
| + | {| cellspacing="1" cellpadding="1" border="1" style="width: 534px; height: 87px;" | ||
| + | |- | ||
| + | | Vlan name | ||
| + | | Ip address range | ||
| + | | Vlan number | ||
| + | |- | ||
| + | | ServerHQ | ||
| + | | 10.1.1.0/24 | ||
| + | | 3 | ||
| + | |- | ||
| + | | GuestHQ | ||
| + | | 172.16.0.0/24 | ||
| + | | 4 | ||
| + | |- | ||
| + | | ClientHQ | ||
| + | | 10.1.2.0/24 | ||
| + | | 5 | ||
| + | |- | ||
| + | | PhoneHQ | ||
| + | | 10.1.3.0/24 | ||
| + | | 6 | ||
| + | |} | ||
| − | + | Branch1 | |
| − | |||
| − | |||
| + | {| cellspacing="1" cellpadding="1" border="1" style="width: 534px; height: 87px;" | ||
| + | |- | ||
| + | | Vlan name | ||
| + | | Ip address range | ||
| + | | Vlan number | ||
| + | |- | ||
| + | | ServerB1 | ||
| + | | 10.2.1.0/24 | ||
| + | | 3 | ||
| + | |- | ||
| + | | GuestB1 | ||
| + | | 172.16.1.0/24 | ||
| + | | 4 | ||
| + | |- | ||
| + | | ClientB1 | ||
| + | | 10.2.2.0/24 | ||
| + | | 5 | ||
| + | |- | ||
| + | | PhoneB1 | ||
| + | | 10.2.3.0/24 | ||
| + | | 6 | ||
| + | |} | ||
| + | Misc. | ||
| − | + | {| cellspacing="1" cellpadding="1" border="1" style="width: 538px; height: 87px;" | |
| + | |- | ||
| + | | Purpose | ||
| + | | Ip address range | ||
| + | |- | ||
| + | | Lan p2p links | ||
| + | | 10.255.255.x/30 | ||
| + | |- | ||
| + | | Management | ||
| + | | 10.0.0.x/32 | ||
| + | |- | ||
| + | | Gre p2p links | ||
| + | | 10.255.254.x/30 | ||
| + | |} | ||
| + | /*see the network diagram for the ip address assignments | ||
== Equipment list == | == Equipment list == | ||
| Line 22: | Line 115: | ||
'''HQ<br/>''' | '''HQ<br/>''' | ||
1 x Asa5505<br/> | 1 x Asa5505<br/> | ||
| − | 1 x Wlc2006<br/> | + | 1 x [[Netband_Project_-_WLC|Wlc2006]]<br/> |
| − | 1 x Catalyst 3560 PoE<br/> | + | 1 x Catalyst 3560 PoE (default IOS:(C3560-IPSERVICES-M), Version 12.2(25)SEE3, RAM 128MB, Flash: 16MB)<br/> |
1 x 1221 Lap<br/> | 1 x 1221 Lap<br/> | ||
| − | 1 x 2801<br/> | + | 1 x 2801 (IOS Software, 2801 Software (C2801-ADVIPSERVICESK9-M), Version 12.4(9)T, RAM: 128MB, Flash: 64MB)<br/> |
'''Branch 1<br/>''' | '''Branch 1<br/>''' | ||
1 x Asa5505<br/> | 1 x Asa5505<br/> | ||
| − | 1 x Catalyst 3560 PoE<br/> | + | 1 x Catalyst 3560 PoE (default IOS:(C3560-IPSERVICES-M), Version 12.2(25)SEE3, RAM 128MB, Flash: 16MB)<br/> |
1 x 1221 Lap<br/> | 1 x 1221 Lap<br/> | ||
| − | 1 x 2801<br/> | + | 1 x 2801 (IOS Software, 2801 Software (C2801-ADVIPSERVICESK9-M), Version 12.4(9)T, RAM: 128MB, Flash: 64MB)<br/> |
'''Cloud<br/>''' | '''Cloud<br/>''' | ||
| − | 1 x 2801<br/> | + | 1 x 2801 ((C2801-ADVIPSERVICESK9-M), Version 12.4(9)T, RAM: 128MB, Flash: 64MB)<br/> |
| − | 1 x 3560<br/> | + | 1 x 3560 ((C3560-IPSERVICES-M), Version 12.2(25)SEB4, RAM:128MB, Flash: 32MB)<br/> |
| − | = | + | ==Reference links== |
| + | Include this in all documents | ||
<pre> | <pre> | ||
| − | + | This page is part of the [[Netband_Project|Netband Project]] | |
</pre> | </pre> | ||
| + | ==Passwords== | ||
| + | [[Netband_Project_-_Inet_router|Internet NAT router]](192.168.138.148): cisco<br/> | ||
| + | [[Netband_Project_-_Inet_Switch|Internet Switch]](192.168.0.5): cisco<br/> | ||
| + | [[Netband Project - Ubuntu server|Ubuntu server]] (10.1.1.10): administrator or root:ciscodisco<br/> | ||
| + | [[Netband_Project_-_Windows_server|W2k3 Server HQ]] (10.1.1.11): Administrator:ciscodisco<br/> | ||
| + | AD client users: | ||
| + | user1:user1pw<br/> | ||
| + | AD domain amdin users: adadm:ciscodisco | ||
| − | = | + | =External Links= |
| − | + | [[Category:network]][[Category:CCNP]][[category:students]] | |
| − | |||
| − | |||
| − | |||
Latest revision as of 15:21, 22 August 2010
The main goal of this project is to design, implement and test some of the many security functionalities in Cisco IOS.
Contents
Course description
A small company setup is used to illustrate and document the various relevant security features on an network infrastructure. The bussiness case evolves around a small to medium sized company with a centralized HQ and a number of remote branch offices. The project will consist mainly of cisco switches, routers and Asa firewall appliances. In order to support and demonstrate selected features, a small number of linux and windows servers are installed. The servers are just used as support so only basic configuration and security are implemented.
The project will touch on the following areas:
- DMVPN
- WLC
- IPSec vpn
- Asa firewall
- Zone based firewall
- IOS firewall
- IOS ips
- DHCP snooping
- Dynamic Arp Inspection
- IP Source Guard
- SNMPv3
- Embedded event manager
- 802.1x
- VMPS
- CoPP
- Private vlans
- Multicast
- Device hardening
- Syslog
- DHCP
- DFS
- AD
- Goodies
- Network access control
Ip addresses
HQ
| Vlan name | Ip address range | Vlan number |
| ServerHQ | 10.1.1.0/24 | 3 |
| GuestHQ | 172.16.0.0/24 | 4 |
| ClientHQ | 10.1.2.0/24 | 5 |
| PhoneHQ | 10.1.3.0/24 | 6 |
Branch1
| Vlan name | Ip address range | Vlan number |
| ServerB1 | 10.2.1.0/24 | 3 |
| GuestB1 | 172.16.1.0/24 | 4 |
| ClientB1 | 10.2.2.0/24 | 5 |
| PhoneB1 | 10.2.3.0/24 | 6 |
Misc.
| Purpose | Ip address range |
| Lan p2p links | 10.255.255.x/30 |
| Management | 10.0.0.x/32 |
| Gre p2p links | 10.255.254.x/30 |
/*see the network diagram for the ip address assignments
Equipment list
HQ
1 x Asa5505
1 x Wlc2006
1 x Catalyst 3560 PoE (default IOS:(C3560-IPSERVICES-M), Version 12.2(25)SEE3, RAM 128MB, Flash: 16MB)
1 x 1221 Lap
1 x 2801 (IOS Software, 2801 Software (C2801-ADVIPSERVICESK9-M), Version 12.4(9)T, RAM: 128MB, Flash: 64MB)
Branch 1
1 x Asa5505
1 x Catalyst 3560 PoE (default IOS:(C3560-IPSERVICES-M), Version 12.2(25)SEE3, RAM 128MB, Flash: 16MB)
1 x 1221 Lap
1 x 2801 (IOS Software, 2801 Software (C2801-ADVIPSERVICESK9-M), Version 12.4(9)T, RAM: 128MB, Flash: 64MB)
Cloud
1 x 2801 ((C2801-ADVIPSERVICESK9-M), Version 12.4(9)T, RAM: 128MB, Flash: 64MB)
1 x 3560 ((C3560-IPSERVICES-M), Version 12.2(25)SEB4, RAM:128MB, Flash: 32MB)
Reference links
Include this in all documents
This page is part of the [[Netband_Project|Netband Project]]
Passwords
Internet NAT router(192.168.138.148): cisco
Internet Switch(192.168.0.5): cisco
Ubuntu server (10.1.1.10): administrator or root:ciscodisco
W2k3 Server HQ (10.1.1.11): Administrator:ciscodisco
AD client users:
user1:user1pw
AD domain amdin users: adadm:ciscodisco